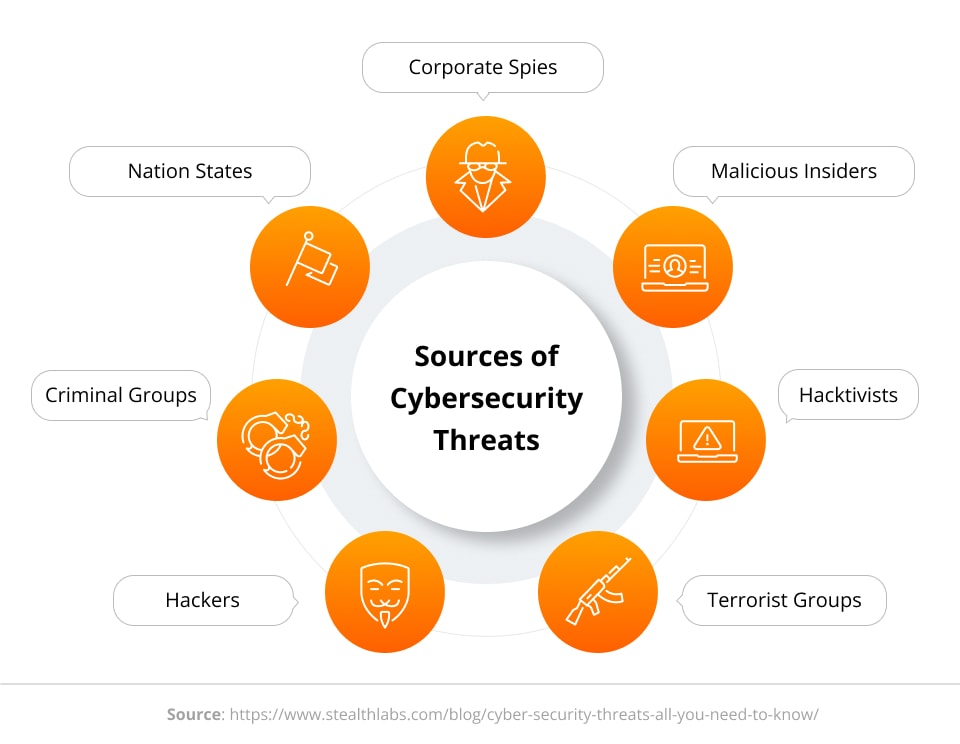
The Significance of Cybersecurity in the Workplace
Cybersecurity has become an essential pillar of modern business operations. Understanding the intricacies of this landscape is crucial for organizations aiming to protect their assets, data, and reputation.
Understanding the Threat Landscape
The threats businesses face today are more sophisticated than ever before. Cybercriminals employ various methods, such as phishing emails, ransomware attacks, and DDoS (Distributed Denial of Service) assaults. Recognizing these tactics helps organizations stay proactive rather than reactive.
- Phishing Attacks: These deceptive schemes often lure employees into disclosing sensitive information.
- Ransomware: A prevalent method where hackers encrypt critical files and demand a ransom for their release.
- Malware: Malicious software designed to harm or exploit devices and networks.
Impact of Cyber Attacks on Businesses
The repercussions of cyber attacks can be devastating, leading to significant financial losses and damaging reputations. For instance, a company might experience:
- Data Breaches: Which can expose sensitive customer information.
- Operational Disruption: That hinders productivity and affects services.
- Legal Repercussions: Resulting from non-compliance with data protection regulations.
As seen with various high-profile cases, the fallout from cyber incidents isn’t just immediate; it also instills long-term trust issues with clients and partners. Therefore, investing in a robust cybersecurity strategy is not just wise—it’s essential.

Building a Comprehensive Cybersecurity Strategy
To effectively combat cyber threats, organizations must focus on building a robust cybersecurity strategy. This involves understanding potential vulnerabilities and implementing effective defense mechanisms.
Assessing Vulnerabilities and Risks
The first critical step is assessing where your organization’s weaknesses lie. This involves conducting thorough audits of systems, networks, and software. Here are some common areas to evaluate:
- Software Vulnerabilities: Outdated applications or unpatched systems can become easy targets.
- Network Security: Open ports or weak firewalls may expose sensitive resources.
- Employee Awareness: Often, human error is a significant vulnerability. Are staff trained to recognize phishing attempts?
Utilizing tools like vulnerability scanners can help identify these risks systematically.
Implementing Multi-Layered Defense Mechanisms
Once vulnerabilities are identified, organizations should adopt a multi-layered defense strategy, often referred to as “Defense in Depth.” This approach involves using various security measures to protect the business comprehensively.
Some effective layers include:
- Firewalls: To block unauthorized access while allowing authorized communications.
- Antivirus Solutions: To detect and eliminate malware threats.
- Encryption: So sensitive data remains secure even if compromised.
By layering these defenses, organizations can create a stronger barrier against potential cyber threats, ensuring a more secure workplace for everyone.
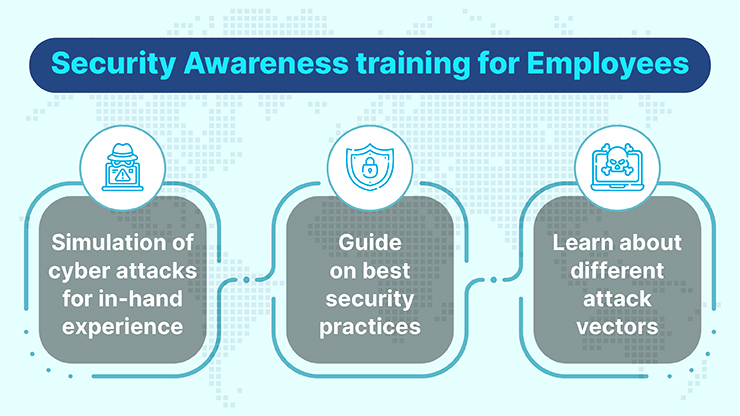
Employee Training and Awareness Programs
With a solid cybersecurity strategy in place, the next step revolves around the human factor—employees. Effective employee training and awareness programs are vital for maintaining security standards in any organization.
Educating Staff on Cybersecurity Best Practices
Informing employees about cybersecurity best practices can dramatically reduce risks. Regular training sessions can encompass essential topics such as:
- Recognizing Phishing Attacks: Teaching staff how to identify suspicious emails.
- Creating Strong Passwords: Encouraging the use of complex passwords and secure password managers.
- Safe Browsing Habits: Educating on the dangers of accessing unsecured websites.
For example, during a recent training session, a colleague recounted how they almost fell for a phishing scam. Sharing stories like these can make the training relatable and impactful.
Creating a Culture of Security Awareness
Beyond training, fostering a culture of security awareness is crucial. This means making cybersecurity a priority throughout the organization. Leaders can:
- Encourage Open Communication: Create a safe space for employees to report suspicious activities without fear of reprimand.
- Reward Good Cyber Hygiene: Recognizing those who practice strong security can motivate others.
By embedding cybersecurity into the company culture, organizations empower employees to become active participants in safeguarding their data, ultimately enhancing the overall security posture.

Investing in Advanced Security Technologies
As organizations strive to enhance their cybersecurity frameworks, investing in advanced security technologies becomes imperative. Robust solutions protect digital assets while ensuring streamlined operations.
Utilizing Endpoint Protection Solutions
A critical component of modern security is endpoint protection. With employees using multiple devices—laptops, tablets, and smartphones—these endpoints must be secured. Effective endpoint protection solutions offer:
- Real-Time Threat Analysis: Continuous monitoring for potential breaches.
- Malware Protection: Safeguarding against viruses and unauthorized software.
- Device Management: Ensuring that all devices comply with security policies.
For instance, I once witnessed a friend’s company avert a full-blown ransomware attack due to their proactive deployment of endpoint solutions. It can truly be a game-changer.
Deploying Intrusion Detection Systems
Along with endpoint protection, deploying intrusion detection systems (IDS) is essential. IDS continuously monitors network traffic for suspicious activities by:
- Analyzing Traffic Patterns: Identifying anomalies that might suggest a breach.
- Alerting IT Teams: Instant notifications can empower swift responses to potential threats.
- Logging Data for Review: Keeping records can help in future threat assessments.
By integrating these advanced technologies, organizations not only enhance their defenses but also foster a comprehensive cybersecurity strategy that can adapt to emerging risks.

Incident Response and Recovery Planning
Even with robust cybersecurity measures, incidents can and do happen. Therefore, having a well-thought-out incident response and recovery plan is essential for minimizing damage and ensuring business continuity.
Developing a Protocol for Responding to Security Breaches
Creating a clear protocol for responding to security breaches can significantly streamline recovery efforts. This protocol should include:
- Identification of Roles: Designate team members as Incident Response Leaders, Communication Officers, and Technical Specialists.
- Incident Classification: Establish different levels of severity to prioritize responses accordingly.
- Communication Plans: Develop guidelines for internal and external communications to manage stakeholder expectations.
Notably, during a recent security bridge in a small firm, having a predefined protocol helped their team act quickly and effectively, minimizing disruption.
Establishing Backup and Recovery Procedures
Equally important is the establishment of solid backup and recovery procedures. Organizations should:
- Regularly Back Up Data: Use both on-site and cloud solutions to ensure redundancy.
- Test Recovery Plans: Regularly conduct drills to confirm that backup systems function properly and that the team knows how to execute recovery tasks.
- Document Everything: Maintain logs of what data is backed up and where it’s stored.
By combining effective incident response protocols with reliable backup procedures, organizations can bolster their resilience and quickly bounce back from cyber incidents, maintaining trust and operational integrity.
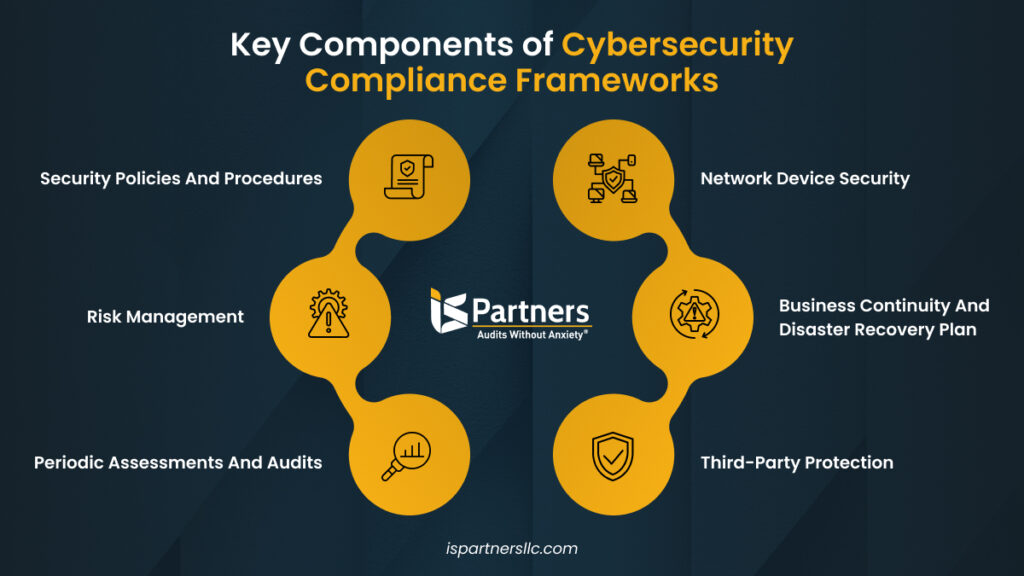
Compliance with Regulatory Requirements
In today’s digital landscape, compliance with regulatory requirements is not just a legal obligation but a critical component of a robust cybersecurity strategy. Businesses must ensure they adhere to various data protection standards to safeguard sensitive information.
Meeting Data Protection Standards
Data protection standards, such as GDPR and CCPA, are essential for maintaining customer trust and avoiding hefty fines. To meet these standards, organizations should focus on:
- Data Encryption: Protect personal data both at rest and in transit to prevent unauthorized access.
- Privacy Policies: Develop clear and transparent privacy policies that inform users how their data will be used.
- Regular Audits: Conduct assessments to ensure compliance and identify potential gaps in security.
For example, a friend working at a tech startup shared how implementing GDPR-compliant processes not only helped them avoid penalties but also improved client relationships.
Addressing Industry-Specific Regulations
In addition to general data protection standards, many industries have specific regulations that organizations must comply with. These may include:
- HIPAA for healthcare organizations: Protecting patient information and electronic health records.
- PCI-DSS for the payment card industry: Safeguarding credit card transactions and customer data.
Understanding and implementing these industry-specific regulations is crucial for fostering compliance and enhancing overall cybersecurity posture. By diligently adhering to these requirements, organizations can not only protect sensitive data but also build a reputation for trustworthiness in their respective markets.

Continuous Monitoring and Evaluation
In the ever-evolving landscape of cybersecurity, continuous monitoring and evaluation are crucial for staying one step ahead of threats. Organizations must commit to ongoing assessments to ensure their defenses are robust and effective.
Conducting Regular Security Audits
Regular security audits form the backbone of a proactive cybersecurity strategy. These audits should encompass:
- Comprehensive Assessments: Analyze systems, applications, and networks to identify vulnerabilities.
- Policy Evaluations: Review current security policies to ensure they align with best practices.
- Employee Feedback: Gather insights from staff about potential security weaknesses they may perceive.
For instance, a company that conducts semi-annual security audits discovered outdated software that, if left unchecked, could have exposed them to significant risks.
Adapting the Strategy to Evolving Threats
As threats evolve, organizations must be agile in adapting their cybersecurity strategies. This includes:
- Staying Informed: Keeping abreast of the latest cyber threats and trends through industry reports and news.
- Implementing New Technologies: Integrating new tools and solutions that can better address emerging threats.
- Ongoing Employee Training: Reinforcing training programs to align with the latest best practices and challenge areas.
By committing to continuous monitoring and adapting strategies to address emerging threats, organizations can maintain a resilient cybersecurity posture, effectively protecting their assets and information in this dynamic environment.

Collaboration with External Security Experts
In the complex realm of cybersecurity, collaboration with external security experts can significantly enhance an organization’s defenses. Leveraging external resources helps fill gaps in expertise and resources, ultimately creating a more fortified security landscape.
Engaging Third-Party Security Services
Engaging third-party security services allows organizations to benefit from specialized knowledge and cutting-edge tools that might not be feasible internally. Key offerings often include:
- Vulnerability Assessments: Experts can conduct thorough assessments to uncover weaknesses that internal teams might overlook.
- Incident Response Support: In the event of a breach, external specialists can provide immediate assistance and containment strategies.
- Security Consulting: Insight from seasoned professionals can help organizations develop tailored strategies and implement best practices.
For instance, a colleague once shared that after employing a third-party service, they identified vulnerabilities in their infrastructure that significantly reduced their exposure to threats.
Participating in Information Sharing Networks
Moreover, participating in information sharing networks fosters collaboration among peers and strengthens collective defenses. Consider these benefits:
- Access to Threat Intelligence: Quickly share information about emerging threats and vulnerabilities.
- Benchmarking Against Peers: Organizations can assess their security postures against industry standards.
- Collective Learning: Engaging in discussions about strategies and experiences enhances overall security knowledge.
By collaborating with external security experts and participating in information sharing, organizations can bolster their defenses against cyber threats, ensuring a proactive and informed approach to security in today’s dynamic environment.

