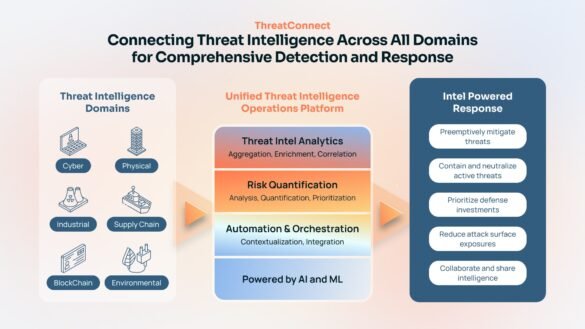
Understanding Threat Intelligence Platforms
Definition and Scope of Threat Intelligence
Threat intelligence refers to the collection, evaluation, and analysis of data regarding potential or current attacks that could compromise an organization’s assets. In simpler terms, it’s all about understanding the landscape of cyber threats that could impact business operations. This intelligence can range from basic indicators of compromise (IoCs) to more complex insights into attack methods, threat actors, and emerging vulnerabilities.
Role of Threat Intelligence Platforms in Cybersecurity
Threat intelligence platforms (TIPs) play a crucial role in enhancing cybersecurity measures. These platforms aggregate, analyze, and disseminate threat data, enabling organizations to:
- Stay Ahead of Threats: By providing real-time updates on emerging threats.
- Improve Incident Response: Ensuring a faster and more efficient reaction to breaches.
- Enhance Collaboration: Facilitating information sharing across departments.
Consider a mid-sized firm that faced multiple phishing attempts; by implementing a TIP, they gained visibility into threat patterns and could proactively mitigate risks, ultimately improving their security posture.

Types of Threat Intelligence Data
Indicators of Compromise (IoCs)
Indicators of Compromise (IoCs) are critical data points that signal potential malicious activities. These can include specific IP addresses, file hashes, domain names, and patterns that indicate a security breach. By consistently monitoring IoCs, organizations can detect breaches early and prevent further damage.
Tactics, Techniques, and Procedures (TTPs)
Tactics, Techniques, and Procedures (TTPs) offer a deeper understanding of how attackers operate. TTPs describe:
- Tactics: The overarching goal of the attack (e.g., data theft).
- Techniques: The methods used to achieve those tactics (e.g., spear phishing).
- Procedures: Detailed steps follow to carry out an attack.
Understanding TTPs helps organizations anticipate and counteract attacks.
Threat Actor Profiles
Threat actor profiles encompass valuable intelligence about who is attacking. This includes their motivations, preferred methods, and previous activities. By constructing these profiles, organizations can better tailor their defenses.
Vulnerabilities and Exploits
Tracking vulnerabilities and exploits enables organizations to close security gaps before they can be leveraged by attackers. Regular updates on software weaknesses and real-time alerts regarding exploit attempts help maintain a robust security posture. For example, consider a scenario where an organization learns about a newly discovered vulnerability in their software; by acting swiftly, they can patch it before it becomes a target.
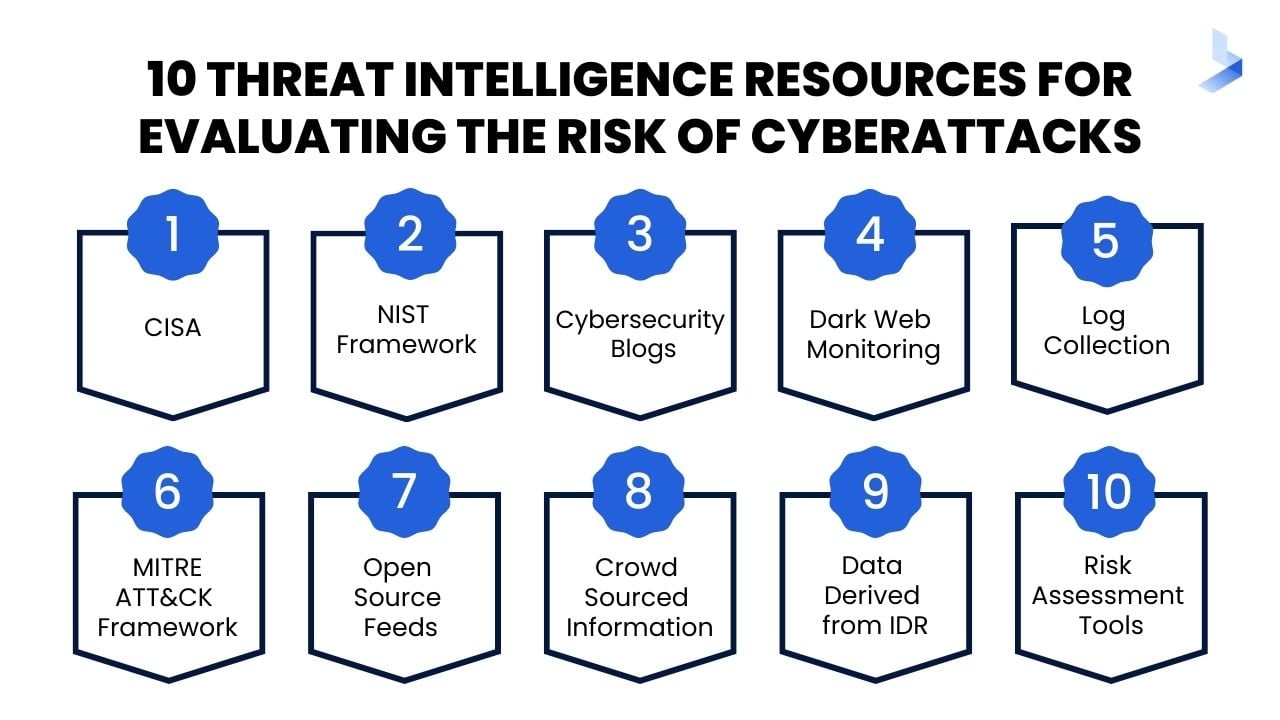
Benefits of Using Threat Intelligence Platforms
Proactive Threat Detection and Response
One of the standout benefits of threat intelligence platforms is their ability to enable proactive threat detection and response. With timely data at their fingertips, organizations can identify potential threats before they escalate into full-blown attacks.
- Real-Time Alerts: Instant notifications about emerging threats allow for immediate action.
- Contextual Information: Understanding the severity and context of a threat helps prioritize responses.
Enhancing Incident Response Capabilities
Threat intelligence platforms also bolster an organization’s incident response capabilities. They provide a structured approach to handling incidents, reducing reaction time.
For example, a financial firm that employs a TIP may discover a targeted attack on customer data. With a predefined response plan based on threat intelligence, they can swiftly neutralize the threat and minimize impact.
Improving Decision-Making and Risk Management
Finally, integrating threat intelligence into decision-making processes enhances overall risk management. Organizations can make informed choices regarding their security investments and prioritize critical vulnerabilities.
- Data-Driven Strategies: Utilizing threat intelligence informs policies and procedures.
- Resource Allocation: Understanding threat landscapes ensures resources are focused where they are most needed.
By harnessing these benefits, businesses can create a robust cybersecurity framework that adapts to an ever-evolving threat environment.
Key Features to Look for in Threat Intelligence Platforms
Data Sources and Integration
When evaluating threat intelligence platforms, the variety and quality of data sources are paramount. A robust platform should integrate seamlessly with various security tools and databases.
- Diverse Sources: Look for platforms that pull data from global threat feeds, open-source intelligence, and industry-specific databases.
- Interoperability: Ensure the platform can connect with existing systems, such as SIEM or firewall solutions, to enrich security data.
Analysis and Contextualization Capabilities
Effective threat intelligence goes beyond raw data; it’s about interpretation. Platforms must have strong analysis and contextualization features to transform data into actionable insights.
- Threat Categorization: The ability to categorize threats based on urgency and relevance is crucial.
- Contextual Analysis: Understanding the “why” behind a threat helps in crafting a suitable response.
Automation and Collaboration Tools
The modern cybersecurity landscape demands efficiency, which is where automation and collaboration tools shine. Automated threat detection mechanisms reduce manual workload and speed up response times.
For instance, consider a security team overwhelmed by alerts. With automated workflows that categorize and prioritize threats, they can focus on the most pressing issues. Additionally, collaboration tools facilitate information sharing between departments, ensuring everyone is aligned on security measures.
By prioritizing these key features, organizations can select a threat intelligence platform that not only meets their needs today but also adapts to future challenges.
Implementing Threat Intelligence Platforms Effectively
Developing a Threat Intelligence Strategy
To implement a threat intelligence platform successfully, organizations must start by developing a comprehensive threat intelligence strategy. This roadmap should:
- Identify Goals: Clearly define what you wish to achieve, whether it’s improved detection or informed risk management.
- Assess Resources: Evaluate existing resources and capabilities. This ensures alignment with the strategy.
Integration with Existing Security Infrastructure
Next, integrating the threat intelligence platform with existing security infrastructure is paramount.
- Seamless Connections: Ensure that the platform communicates effectively with tools like SIEM systems, firewalls, and endpoint protection.
- Data Flow: Establish a smooth data flow for optimum real-time analysis and response.
Training and Skill Development
Finally, investing in training and skill development for your team is critical. Regular workshops and training sessions ensure that team members understand the tools and can leverage threat intelligence effectively.
For instance, a recent training session at an organization led to enhanced incident response capabilities, highlighting the importance of knowledgeable personnel in maximizing the effectiveness of a threat intelligence platform.
By focusing on these areas, organizations can ensure that their threat intelligence implementations yield significant returns on investment and bolster their overall security posture.

Challenges and Considerations
Data Quality and Reliability
While implementing threat intelligence platforms brings numerous benefits, challenges do arise, particularly regarding data quality and reliability. Organizations must ensure that the data they collect is accurate and relevant. High-quality data leads to:
- Informed Decisions: Reliable data helps in making sound security decisions.
- Reduced False Positives: Enhancing efficiency by minimizing irrelevant alerts.
For instance, a company relying on outdated threat feeds may find itself misallocating resources due to incorrect data interpretations.
Resource Constraints
Resource constraints also pose significant challenges. Many organizations, especially smaller enterprises, may struggle with the budget and personnel needed to effectively utilize a threat intelligence platform.
Organizations should consider:
- Resource Allocation: Investing wisely in automation can alleviate some of the burdens on staff.
- Outsourcing Options: Applying managed services or outsourcing certain functions can provide flexibility.
Legal and Ethical Considerations
Finally, navigating legal and ethical considerations is crucial. Organizations should be aware of data privacy laws and protocols to avoid potential legal pitfalls.
- Data Handling Policies: Establish clear policies regarding data use and sharing.
- Transparency: Being transparent about threat intelligence practices can foster trust among stakeholders.
By anticipating these challenges, organizations can better prepare themselves, ensuring that their threat intelligence efforts are not only effective but also responsible and sustainable.
Case Studies: Real-World Examples of Threat Intelligence Platform Success
Company A: Mitigating Advanced Persistent Threats (APTs)
Company A, a financial institution, faced a series of Advanced Persistent Threats (APTs) targeting their critical infrastructure. By implementing a sophisticated threat intelligence platform, they gained comprehensive visibility into potential threats.
- Enhanced Detection: The platform’s ability to analyze TTPs allowed the security team to identify attack vectors early.
- Rapid Response: Consequently, they established a proactive response framework that mitigated the APTs before they could inflict substantial harm.
As a result, Company A significantly reduced threat exposure and fortified its defenses against future attacks.
Organization B: Thwarting Phishing Campaigns
In another instance, Organization B, a technology firm, encountered rising phishing attacks aimed at stealing sensitive customer information. By deploying a threat intelligence platform, they could:
- Identify IoCs: Recognize suspicious domains and email patterns in real-time.
- Educate Employees: Conduct targeted training sessions based on discovered threats, reinforcing employee awareness.
The proactive measures taken allowed Organization B to thwart multiple phishing attempts, safeguarding personnel and customer data. These case studies illustrate how effectively harnessed threat intelligence can transform an organization’s cybersecurity posture.

Future Trends in Threat Intelligence Platforms
Machine Learning and Artificial Intelligence (AI) Applications
As we look to the future, the integration of Machine Learning (ML) and Artificial Intelligence (AI) into threat intelligence platforms is set to revolutionize cybersecurity practices. These technologies can analyze vast amounts of data, identify patterns, and detect anomalies with remarkable speed and accuracy.
- Automated Threat Detection: Predictive analytics can significantly enhance proactive measures.
- Adaptive Learning: AI models that evolve with new data will stay ahead of emerging threats.
Emerging Threat Intelligence Sharing Models
Emerging models for threat intelligence sharing are also gaining traction. Collaboration among organizations will play a crucial role in combating cyber threats effectively.
- Community-Based Platforms: Sharing insights within industry-specific groups can bolster collective defenses.
- Public-Private Partnerships: Enhanced collaboration between government entities and private sectors can lead to greater threat visibility.
Regulatory Impacts on Threat Intelligence Practices
Regulatory impacts will shape the landscape of threat intelligence practices. As governments enact stricter data protection laws, organizations will need to adopt compliant threat intelligence strategies.
- Data Privacy: Adhering to laws such as GDPR will require platforms to implement meticulous data handling processes.
- Transparency Requirements: Companies will need to communicate their threat intelligence efforts to stakeholders clearly.
By understanding these trends, organizations can proactively adapt their cybersecurity strategies, ensuring they remain resilient against the ever-evolving threat landscape.