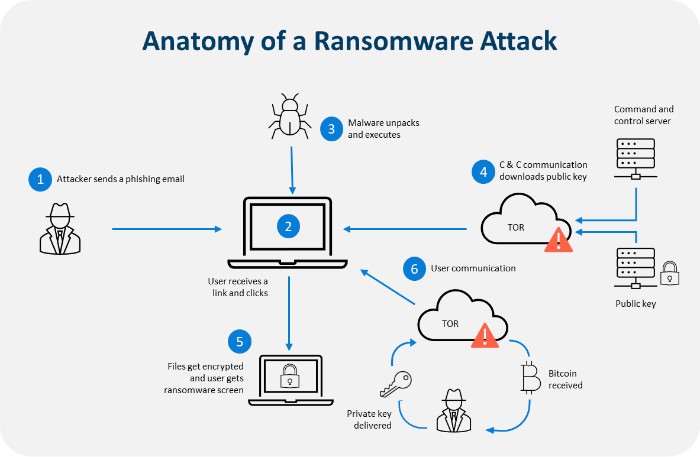
Introduction
Definition of Ransomware
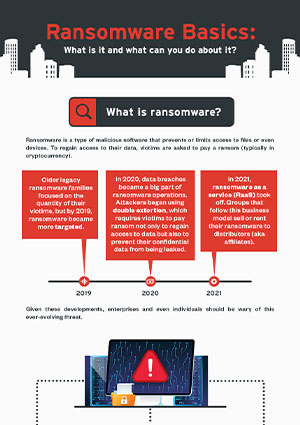
Ransomware is a malicious software designed to block access to a computer system or files until a sum of money, or a ransom, is paid. Essentially, it encrypts the victim’s data and demands payment for the decryption key. This type of cyberattack is not only costly but also incredibly disruptive.
Impact of Ransomware Attacks
The impact of ransomware attacks can be staggering, affecting individuals and organizations alike.
- Financial Loss: Businesses may face hefty ransom demands, and the cost of data recovery can skyrocket.
- Operational Downtime: Organizations often find themselves incapacitated, unable to operate while dealing with the aftermath.
- Emotional Toll: Victims of ransomware can experience stress, anxiety, and a sense of violation as their personal and sensitive data is compromised.
The growing frequency of these attacks illustrates the need for increased awareness and preventive measures to combat this escalating threat.

Evolution of Ransomware
Historical Background
The history of ransomware dates back to the late 1980s with the infamous “PC Cyborg” virus, which encrypted files on a user’s computer. Victims received a ransom demand via postal mail! Fast forward to the 2000s and beyond, ransomware has evolved, becoming more sophisticated and widespread, making it a significant threat to both individuals and organizations.
Modern Tactics and Techniques
Today’s ransomware attack methodologies are more refined and insidious. Attackers harness various tactics to breach systems, including:
- Advanced Encryption: Using robust algorithms to encrypt files, making decryption without a key virtually impossible.
- Targeted Attacks: Focusing on specific industries, like healthcare and finance, to maximize impact and financial gain.
- Ransomware-as-a-Service (RaaS): Cybercriminals now rent out ransomware tools to other criminals, creating a booming underground market.
Understanding the evolution of ransomware is crucial for developing effective countermeasures and safeguarding sensitive information against this relentless threat.

Consequences of Ransomware Attacks
Financial Implications
The financial fallout from ransomware attacks can be devastating. Organizations often face substantial costs, which may include:
- Ransom Payments: Many victims feel pressured to pay the ransom to restore access to their data, which can range anywhere from thousands to millions of dollars.
- Recovery Expenses: Costs for IT support, system repairs, and data recovery can accumulate quickly.
- Loss of Revenue: Downtime during a ransomware attack can lead to missed opportunities and sales, significantly impacting profits.
Reputational Damage
Beyond immediate financial concerns, the reputational damage from a ransomware incident can linger for years. Customers may lose trust in a brand after a data breach, as privacy and security become paramount in today’s digital age.
- Customer Loyalty: Brands that fall victim may struggle to retain clients or attract new ones due to negative perceptions.
- Legal Consequences: Companies may face lawsuits or regulatory penalties if they are found negligent in protecting customer data.
The consequences of ransomware attacks are far-reaching, highlighting the importance of vigilance and proactive measures in safeguarding valuable assets.
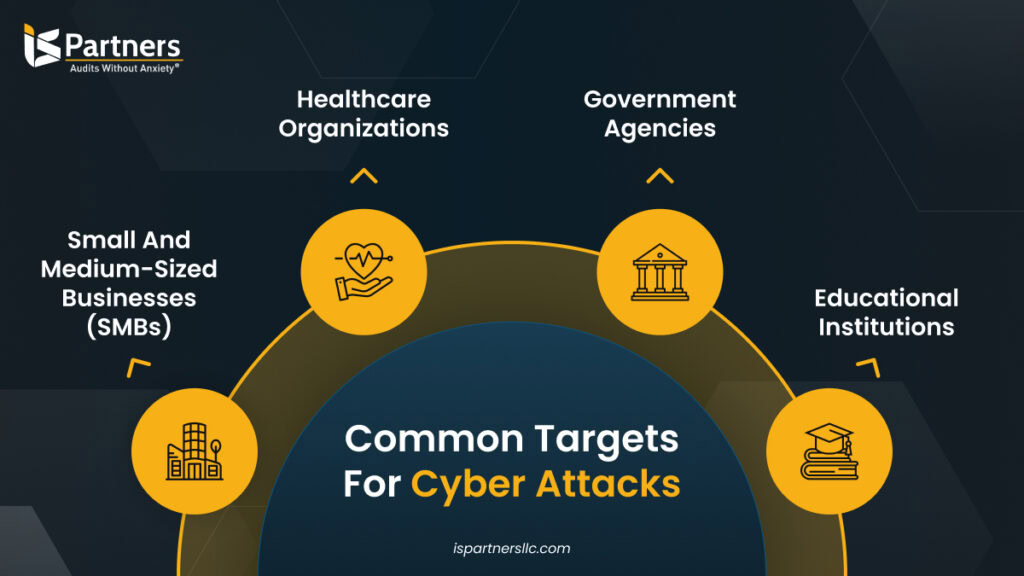
Common Targets and Vulnerabilities
Industries at Risk
Ransomware attacks do not discriminate; however, certain industries are particularly vulnerable due to the nature of their operations. Some of the most affected sectors include:
- Healthcare: Hospitals and clinics house sensitive patient data, making them prime targets for attackers seeking to exploit confidentiality.
- Education: Schools and universities often lack robust cyber defenses and store large volumes of personal data.
- Financial Services: With high-value transactions and sensitive information, banks and financial institutions are consistently in the crosshairs of cybercriminals.
Security Weaknesses Exploited by Ransomware
Cybercriminals exploit various security weaknesses to breach systems:
- Outdated Software: Failing to keep software and systems up-to-date creates vulnerabilities.
- Weak Passwords: Poor password practices leave doorways for malicious access.
- Inadequate Backup Protocols: Without effective backup systems, organizations may have no choice but to pay ransom demands to retrieve their data.
Recognizing these common targets and vulnerabilities is essential for businesses to enhance their security measures and reduce the risk of falling victim to ransomware attacks.
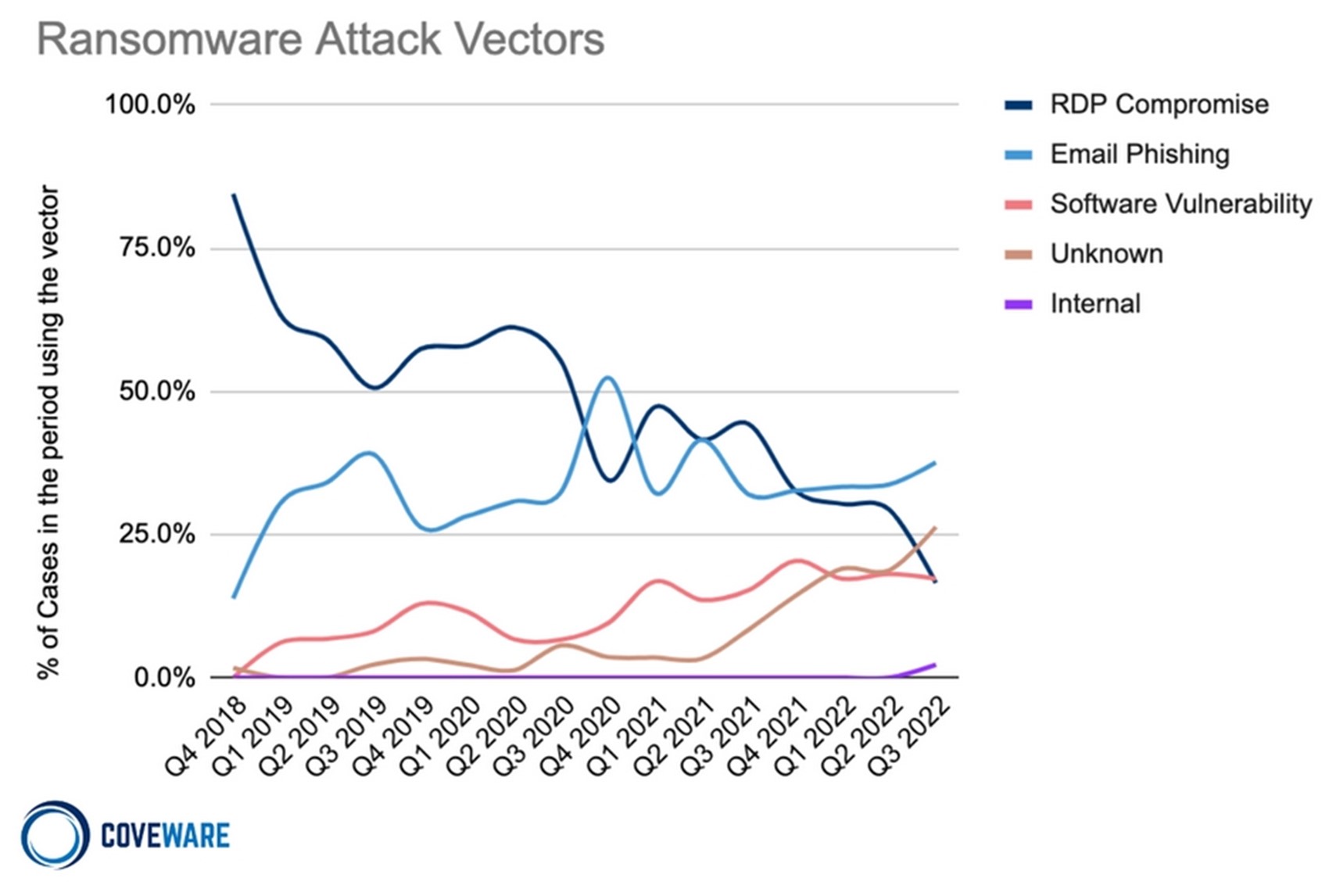
Ransomware Delivery Methods
Phishing Emails
One of the most common delivery methods for ransomware is through phishing emails. These deceptive messages often appear legitimate, tricking recipients into opening attachments or clicking harmful links. Here’s how phishing attacks typically unfold:
- Social Engineering: Attackers craft emails that mimic official communications from trusted organizations, such as banks or IT departments.
- Malicious Attachments: Once opened, an attachment may execute ransomware, locking files on the user’s device.
For instance, a friend of mine once received an email that looked to be from her bank, requesting account verification. Thankfully, she hesitated and researched before clicking!
Malicious Websites
Another alarming avenue for delivering ransomware is via malicious websites. Users may inadvertently land on these sites through:
- Redirects: Clicking on a seemingly innocuous link can lead to a compromised site designed to exploit security flaws.
- Drive-By Downloads: Merely visiting a malicious site can trigger downloads aimed at infiltrating a user’s system.
Understanding these delivery methods is crucial for individuals and organizations to protect themselves from the escalating threat of ransomware. Awareness and caution can be powerful allies in preventing infection.
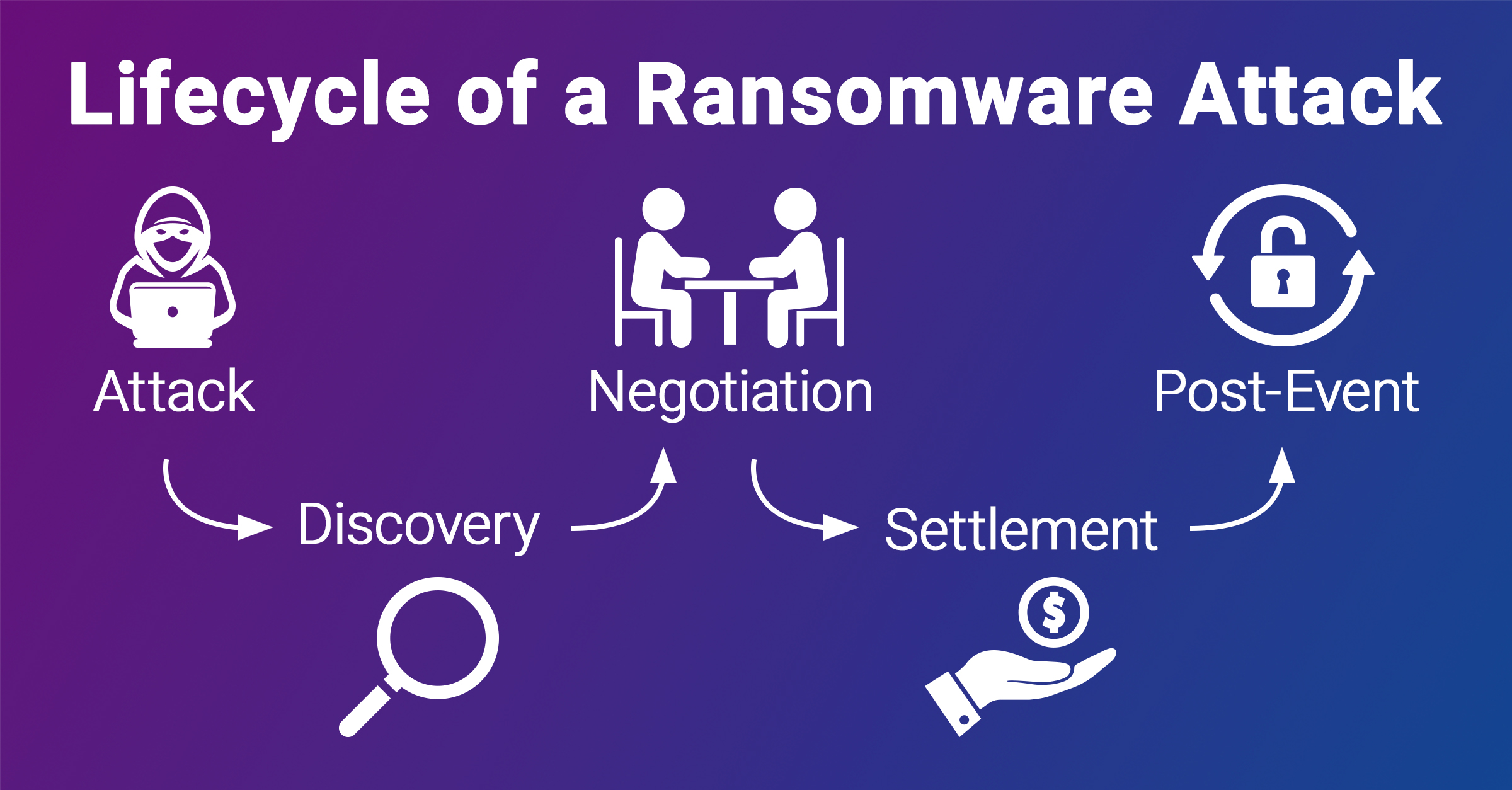
Ransomware Negotiation and Payments
Legal and Ethical Considerations
When faced with a ransomware attack, organizations often grapple with complex legal and ethical issues surrounding payment. For example, paying the ransom might seem like a quick fix, but it can also lead to questions about:
- Legal Liability: Depending on local laws, paying a ransom could potentially implicate a company in supporting criminal activity.
- Ethical Dilemmas: Should organizations encourage further attacks by paying ransoms? Many argue that it sets a dangerous precedent for cybercriminals.
It’s a murky situation; for instance, a well-known healthcare facility paid a ransom to regain patient data, sparking outrage from the community and prompting discussions on responsibility.
Risks Associated with Payment
Payments come with their own set of risks. Organizations that opt to pay the ransom may face:
- No Guarantee: Paying does not guarantee recovery of data or that the attackers won’t strike again.
- Regulatory Scrutiny: Companies paying ransom may attract attention from regulatory bodies investigating compliance and data protection practices.
Thus, negotiations and potential payments in ransomware scenarios require careful consideration and strategic planning to navigate the repercussions that may follow.

Prevention and Mitigation Strategies
Backup and Recovery Practices
One critical strategy for preventing ransomware damage lies in robust backup and recovery practices. Regularly backed-up data serves as a safety net against attacks. Here are some key practices to consider:
- Automated Backups: Use automated systems to ensure backups are created frequently, minimizing data loss.
- Offsite Storage: Store backups in a secure location away from the primary system to protect against simultaneous attacks.
- Testing Recovery Plans: Regularly test your recovery process to ensure that data can be restored effectively when needed.
For instance, a colleague in the tech industry shared how their company avoided disaster after a ransomware attack because they had implemented strict backup protocols.
Employee Training and Awareness
Equally important is the training and awareness of employees. Human error often serves as the weakest link in cybersecurity defenses. Implementing ongoing training can help:
- Recognize Phishing Attempts: Provide resources and real-world examples to help employees spot suspicious emails and activities.
- Promote Safe Browsing Habits: Teach staff about the dangers of clicking on unknown links or downloading unverified attachments.
- Encourage Reporting: Foster an environment where employees feel comfortable reporting potential security threats without fear of repercussions.
By investing in preventive measures like these, organizations can significantly reduce their vulnerability to ransomware attacks and enhance their overall cybersecurity posture.

Legal and Regulatory Frameworks
Compliance Requirements
Navigating the legal landscape following a ransomware attack involves adhering to various compliance requirements that ensure data protection and security. Different industries have distinct regulations, including:
- GDPR (General Data Protection Regulation): This European regulation mandates strict data protection measures and imposes fines for non-compliance.
- HIPAA (Health Insurance Portability and Accountability Act): Organizations handling healthcare data must comply with rigorous standards to protect sensitive information.
For example, a friend working in a healthcare organization once shared how stringent HIPAA regulations compelled them to strengthen their data security protocols and training programs significantly.
Reporting Obligations
In the aftermath of a ransomware incident, businesses may have specific reporting obligations. These Duties include:
- Notifying Affected Parties: Organizations are often required to inform individuals whose data may have been compromised.
- Reporting to Authorities: Certain jurisdictions mandate that breaches are reported to regulatory agencies within a defined timeframe.
Staying informed about these legal and regulatory frameworks is essential for organizations, ensuring they remain compliant and ready to respond effectively to both ransomware threats and the aftermath of any breaches. This not only mitigates potential legal repercussions but also reflects a commitment to transparency and accountability in cybersecurity practices.

Future Trends in Ransomware
Emerging Threats
As ransomware continues to evolve, new and emerging threats are surfacing. Cybercriminals are devising innovative strategies that pose significant risks, such as:
- Targeting Cloud Services: With more businesses migrating to the cloud, attackers are increasingly focusing on these platforms, exploiting vulnerabilities within cloud configurations.
- Ransomware and Data Leaks: Some attackers are now combining ransomware with data exfiltration, threatening to leak sensitive information if their demands aren’t met.
For instance, a case I heard about involved a company that didn’t only lose access to its files but also faced potential public embarrassment due to leaked customer data.
Technological Advancements
On the flip side, advancements in technology also play a critical role in combating ransomware. As cyber threats grow more sophisticated, so do the defensive tools available:
- Artificial Intelligence (AI): AI-driven solutions can help detect and respond to threats more rapidly, protecting systems before damage occurs.
- Improved Encryption Protocols: Enhanced encryption will ensure that sensitive data remains secure, even if attackers gain access.
By staying informed about these future trends, organizations can better prepare themselves not only to defend against impending ransomware threats but also to anticipate the necessary adjustments needed in their cybersecurity strategies. The battle against ransomware is ongoing, and preparation is key to staying one step ahead.
Conclusion
Summary of Key Points
In summary, the growing threat of ransomware underscores the urgent need for comprehensive cybersecurity strategies. We explored how ransomware has evolved from simple viruses to sophisticated attacks, targeting various industries and exploiting vulnerabilities. Key strategies for prevention include:
- Robust backup and recovery practices
- Continuous employee training and awareness
- Adherence to legal compliance and reporting requirements
As organizations navigate this complex landscape, understanding these aspects can significantly mitigate risks.
Call to Action
It’s time for all stakeholders—business leaders, IT professionals, and employees—to take a proactive stance against ransomware. Start implementing the recommended strategies today, and foster a culture of cybersecurity within your organization. Remember, it’s not just about defending against attacks; it’s about preparing for the future. Together, we can combat this growing threat and protect our valuable data and digital assets. Stay informed, stay vigilant!

