Overview of Cybersecurity Threats
Definition of Cybersecurity Threats
In today’s digital age, cybersecurity threats have taken on numerous forms, each designed to exploit vulnerabilities in systems and networks. Simply put, a cybersecurity threat is any potential event or action that could harm or compromise the integrity, confidentiality, or availability of information systems or the data they hold. These threats can stem from various sources, including malicious actors, natural disasters, or even unintentional human error.
To better understand the landscape of cybersecurity threats, consider the common categories they fall into:
- Malware: Malicious software variants designed to disrupt, damage, or gain unauthorized access to computer systems.
- Phishing: Deceptive communication techniques aimed at tricking users into revealing sensitive information.
- Ransomware: A type of malware that locks users out of their files or systems until a ransom is paid.
Recognizing these threats is the first step in protecting oneself and the organization.
Importance of Cybersecurity Awareness
With these threats looming, the importance of cybersecurity awareness becomes paramount. It’s not just about having the latest software or firewalls; it’s about fostering an organizational culture that prioritizes security. For instance, consider the experience of a small business owner who fell victim to a phishing scam. Despite having security measures in place, the lack of employee training led to a successful breach—resulting in stolen funds and sensitive data.
To bolster awareness:
- Regular Training: Conduct workshops focused on identifying potential threats.
- Simulated Attacks: Run mock phishing exercises to prepare employees for real scenarios.
- Communication: Encourage open dialogue about security concerns within teams.
By staying informed and proactive, individuals and organizations can significantly reduce their risk of falling prey to these ever-evolving cybersecurity threats.
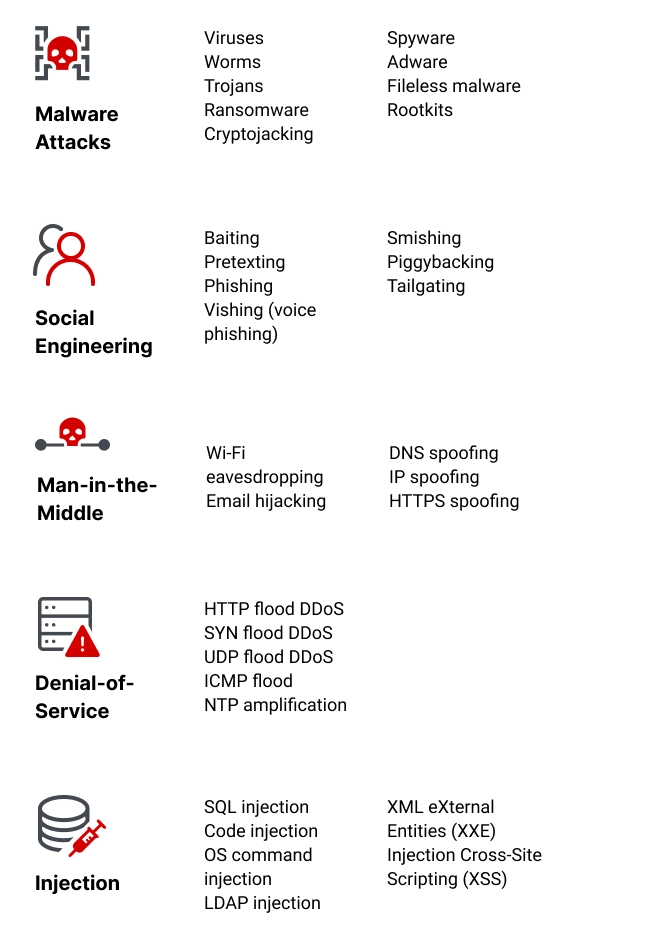
Common Types of Cybersecurity Threats
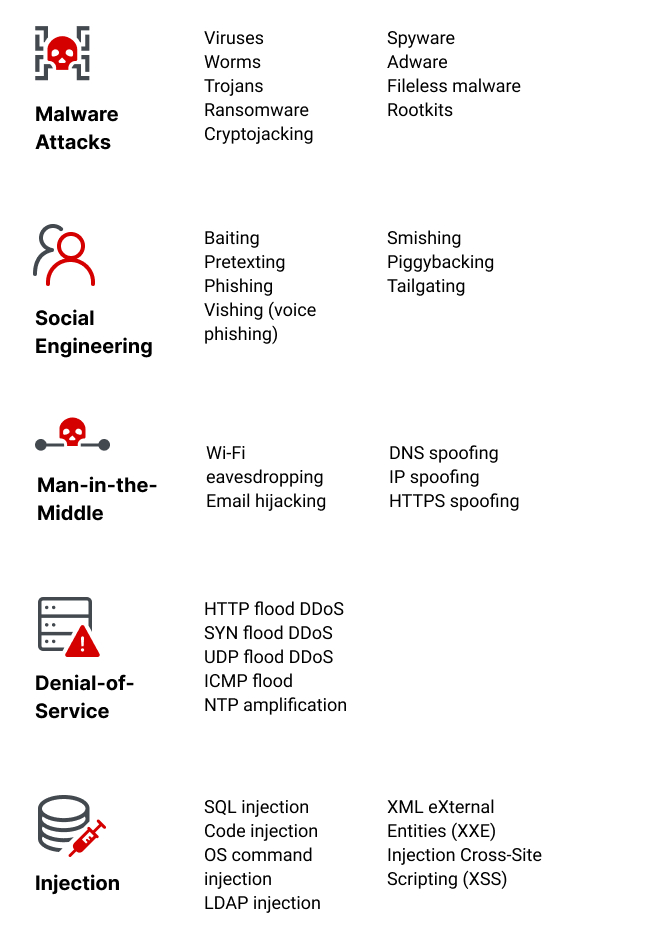
Malware
One of the most prevalent forms of cybersecurity threats is malware, which encompasses a range of malicious software programs intended to disrupt, damage, or gain unauthorized access to computer systems. Examples include viruses, worms, trojans, and spyware. Just last year, a friend of mine accidentally downloaded a trojan horse from what appeared to be a legitimate website, leading to a complete system breach. It’s a harsh reminder of how easily malware can infiltrate our devices.
Phishing
Moving on to phishing, this deceptive technique preys on human psychology. Cybercriminals often impersonate trusted sources, sending emails that look remarkably real, but are designed to trick individuals into divulging personal information. For instance, in one instance, I received an email that claimed to be from my bank, urging me to update my password through a provided link. Thankfully, I recognized it as a scam. To safeguard against phishing:
- Always check email addresses for discrepancies.
- Look for grammatical errors in messages.
- Never click on suspicious links.
Ransomware
Ransomware poses a severe threat, encrypting files or locking users out of their systems until a ransom is paid. Organizations of all sizes are targets, as both small businesses and large corporations have faced crippling attacks. A notable case was the WannaCry ransomware attack, which affected thousands of computers worldwide in 2017.
DDoS Attacks
Distributed Denial of Service (DDoS) attacks flood a network with traffic, overwhelming resources and causing service downtime. This not only disrupts operations but can also lead to significant financial losses.
Insider Threats
Lastly, insider threats often arise from within an organization—either through malicious intent or negligence. Employees may leak sensitive information or fall prey to phishing attacks themselves. Regular internal audits and training can help mitigate such risks.
Understanding these common threats is vital for anyone looking to safeguard their digital landscape effectively.
Advanced Cybersecurity Threats
As we delve deeper into the realm of cybersecurity, it’s crucial to understand advanced threats that go beyond the basics. These sophisticated attacks can bypass standard security measures, posing significant risks to organizations.
Advanced Persistent Threats (APTs)
One of the most insidious forms of threat is the Advanced Persistent Threat (APT). APTs involve prolonged and targeted cyberattacks where an intruder gains access to a network and remains undetected for an extended period. For instance, many APTs are state-sponsored, aiming to steal sensitive data or spy on operations. A notable case was the 2014 breach of the U.S. Office of Personnel Management, where attackers infiltrated the system for months before being discovered.
To combat APTs, organizations should:
- Implement network segmentation to limit access.
- Employ continuous monitoring systems.
- Conduct regular security audits.
Zero-Day Exploits
Next, we have zero-day exploits—vulnerabilities in software that are unknown to the vendor. As the name suggests, developers have zero days to patch these vulnerabilities once they are discovered by hackers. A famous example is the Stuxnet worm, which targeted Iranian nuclear facilities, exploiting several zero-day vulnerabilities.
To protect against these attacks, keeping software up to date is critical. Organizations must prioritize:
- Regularly patching software.
- Monitoring for unusual activity.
Social Engineering Attacks
Finally, let’s discuss social engineering attacks. Unlike other types of threats that focus on technological vulnerabilities, social engineering manipulates human psychology. Attackers often use tactics like pretexting or baiting to trick individuals into sharing sensitive information. A personal anecdote illustrates this well; during a team meeting, an employee received a phone call from someone impersonating IT support, mistakenly believing they were helping.
To guard against social engineering, it’s vital to foster a culture of skepticism and awareness through:
- Regular training sessions on recognizing manipulation tactics.
- Encouraging employees to verify identities before sharing information.
Being aware of these advanced threats is essential for any organization looking to bolster its cybersecurity defenses effectively.
Impact of Cybersecurity Threats
Understanding the advanced cybersecurity threats is just one side of the coin; the impact of these threats can be devastating for organizations and individuals alike. When a breach occurs, the ramifications ripple through finances, reputation, and legal standings.
Financial Losses
First and foremost are the financial losses that accompany cybersecurity incidents. These can stem from various sources, including:
- Direct costs: Expenses related to investigating breaches, restoring systems, and implementing more stringent security measures.
- Downtime: The longer your systems are compromised, the more potential revenue you lose from operations. In 2021, it was reported that companies could lose upwards of $300,000 per hour during a ransomware attack!
A friend of mine who owns a small retail business faced a cyberattack that resulted in significant downtime during the holiday season. The loss was not just in terms of immediate revenue but also in missed customer goodwill.
Reputational Damage
Next, consider the reputational damage that occurs when a company suffers a breach. Customers expect their personal information to be safe, and any compromise can lead to a significant trust deficit.
- Customer retention: After a data breach, surveys show that around 60% of consumers are likely to stop doing business with affected companies.
- Negative publicity: Media coverage surrounding breaches can linger, permanently affecting public perception.
For example, after the Equifax breach in 2017, their reputation plummeted, affecting customer trust for years.
Legal Consequences
Lastly, legal consequences are an essential aspect of the impact. Organizations may face lawsuits from affected individuals, regulatory fines, and increased scrutiny from governing bodies.
- Compliance failures: Data protection laws, like GDPR or HIPAA, can result in hefty penalties for non-compliance.
- Litigation costs: The fallout from a breach can lead to costly litigation, diverting resources away from core business functions.
Navigating the aftermath of cybersecurity threats requires a solid understanding of these impacts, emphasizing the necessity of proactive security measures. By recognizing the stakes involved, organizations can better prepare themselves to fortify their defenses.

Preventing Cybersecurity Threats
Having discussed the significant impacts of cybersecurity threats, it’s imperative to shift our focus to prevention strategies. Implementing effective measures can significantly reduce risks and safeguard sensitive information.
Strong Password Practices
First on the list is practicing strong password hygiene. Weak passwords are often the first vulnerability hackers exploit. To enhance security:
- Use complex passwords: Combine uppercase letters, lowercase letters, numbers, and symbols.
- Avoid common phrases: Steer clear of easily guessable information like birthdays or names.
- Implement multi-factor authentication (MFA): This adds an extra layer of defense, requiring users to provide a second form of verification beyond just the password.
I once learned the hard way about password importance when my email was hacked due to a simple password. Now, I use a password manager to generate and store complex passwords securely.
Regular Software Updates
Next, don’t underestimate the power of regular software updates. Outdated programs often harbor vulnerabilities that cybercriminals eagerly exploit. Make it a practice to:
- Enable automatic updates: This ensures that your software is always equipped with the latest security patches.
- Monitor for updates: Regularly check for updates on less frequently used software as well.
Employee Training
Furthermore, employee training is essential. Even the most advanced security measures can falter when human error is involved. Focus on:
- Conducting regular security awareness training: Empowering employees with knowledge about cybersecurity threats keeps them alert.
- Simulating phishing attacks: This gives employees a practical understanding of how to recognize and react to such threats.
Effective Network Security Measures
Finally, implementing robust network security measures is crucial. This includes:
- Firewalls: Protect networks by controlling incoming and outgoing traffic.
- Intrusion detection systems: Monitor network activity for suspicious behavior.
- Regular audits: Assess the network’s security health to identify and rectify vulnerabilities.
By taking these preventative steps, organizations can build a solid foundation against cybersecurity threats, ultimately keeping sensitive data secure and intact. In our tech-driven world, proactive measures are not just advisable; they are imperative.

Responding to Cybersecurity Threats
Having explored preventative measures against cybersecurity threats, it’s equally crucial to understand how to respond effectively when such threats do materialize. Quick and efficient response can help mitigate damage and restore normal operations.
Incident Response Plan
Central to a robust response framework is an Incident Response Plan (IRP). This plan outlines the steps to take when a cybersecurity incident occurs, ensuring everyone knows their roles and responsibilities. A well-crafted IRP should include:
- Identification: Detecting and confirming the occurrence of a security incident.
- Containment: Isolating affected systems to prevent further damage.
- Eradication: Removing the threat from the environment.
During a previous role, my team faced a potential data breach. Our clear IRP allowed us to act swiftly, containing the issue before it escalated. This experience reinforced the importance of rehearsing incident responses regularly.
Data Recovery Procedures
Following containment, having effective data recovery procedures is vital. The goal is to restore systems and data to normal functioning as quickly as possible. Key considerations should include:
- Backups: Ensure regular backups are conducted and stored securely, ideally off-site.
- Testing: Regularly test recovery processes to confirm that data integrity is maintained.
I remember an incident where our organization faced a ransomware attack that temporarily locked access to critical files. Thankfully, our backups were well-managed, allowing us to restore lost data with minimal disruption.
Reporting Cybersecurity Incidents
Lastly, reporting cybersecurity incidents both internally and externally is essential. It’s important to create transparency and maintain communication throughout the organization, as well as comply with legal obligations. This process might involve:
- Internal notifications: Informing relevant departments and leadership about the incident.
- External reporting: Adhering to regulatory requirements by informing authorities and affected stakeholders if personal data is involved.
Having a structured approach to responding to cybersecurity threats can significantly reduce recovery time and ensure that lessons learned are integrated into future practices. By recognizing the importance of response preparations, organizations can navigate these challenging situations with confidence.
Future Trends in Cybersecurity Threats
As we move forward in an increasingly digital world, it’s essential to keep our gaze on emerging trends in cybersecurity threats. By understanding what lies ahead, organizations can better prepare and adapt their security strategies.
AI and Machine Learning Threats
One of the most significant trends is the rise of threats associated with artificial intelligence (AI) and machine learning. While these technologies have greatly enhanced cybersecurity measures, they can also be exploited by attackers.
- Automated attacks: Cybercriminals can use AI to launch sophisticated, automated attacks that adapt to existing defenses in real-time. It’s like playing chess against a computer that learns from every move you make.
- Deepfakes: With advancements in AI, deepfake technology can create real-looking videos or audio, potentially leading to misinformation campaigns or scams.
A recent incident I encountered involved an executive receiving an audio message that sounded exactly like a colleague requesting sensitive information, highlighting the growing risks of deepfake technology.
IoT Security Challenges
Next, the proliferation of Internet of Things (IoT) devices presents unique security challenges. With increasingly connected devices, the attack surface expands, making it easier for hackers to gain entry into a network.
To address IoT security risks, consider:
- Weak default passwords: Many IoT devices come with easy-to-guess default passwords that users neglect to change.
- Lack of updates: Many devices do not receive regular firmware updates, leading to unpatched security vulnerabilities.
A friend’s home was breached through an unsecured smart thermostat, demonstrating the importance of securing all connected devices.
Quantum Computing Risks
Lastly, quantum computing poses a future threat to traditional cryptography. As quantum computers become more powerful, the encryption methods that protect sensitive information today may be rendered obsolete.
To prepare for this shift:
- Explore post-quantum cryptography: Researchers are actively developing new cryptographic methods that can withstand quantum computing attacks.
- Stay informed: Keeping pace with quantum advancements will help organizations understand potential vulnerabilities.
As we face these evolving trends in cybersecurity threats, it’s vital for organizations to stay proactive and consistent in their approach. By embracing emerging technologies responsibly and investing in robust security measures, we can navigate the complexities of the digital future effectively.

Conclusion
As we wrap up our exploration of cybersecurity, it’s essential to revisit the key points that underscore the importance of this ever-evolving field. From understanding the different types of cybersecurity threats to examining their potential impacts and preventive measures, the need for vigilance is clearer than ever.
Recap of Key Points
Throughout this journey, we have uncovered various aspects of cybersecurity, including:
- Common Threats: We discussed malware, phishing, ransomware, DDoS attacks, and insider threats, all of which pose significant risks.
- Advanced Threats: We branched into advanced persistent threats (APTs), zero-day exploits, and social engineering tactics that challenge even the most secured environments.
- Impact: The financial losses, reputational damage, and legal consequences of cybersecurity breaches remind us of the stakes involved.
- Prevention and Response: From implementing strong password practices and regular software updates to creating incident response plans and data recovery procedures, these strategies are crucial for maintaining security.
Importance of Proactive Cybersecurity Measures
In an age where cyber threats are not only becoming more sophisticated but also more frequent, adopting proactive cybersecurity measures is vital. Organizations and individuals alike must cultivate a culture of security awareness, recognizing that everyone plays a part in maintaining robust defenses.
- Invest in training: Regular employee training ensures that everyone is informed and vigilant.
- Stay updated: Keeping systems and knowledge current makes it far more challenging for attackers to succeed.
- Adapt and evolve: As threats change, our strategies must evolve alongside them.
My own experience in addressing a cybersecurity breach taught me the value of being prepared. It’s not simply about preventing attacks; it’s about fostering a mindset geared towards resilience and recovery. By viewing cybersecurity as an ongoing practice rather than a checklist, we can better navigate the complexities of the digital landscape and safeguard our valuable data for the future.