Overview of Payment Card Industry Data Security Standard (PCI DSS)
History and Purpose of PCI DSS
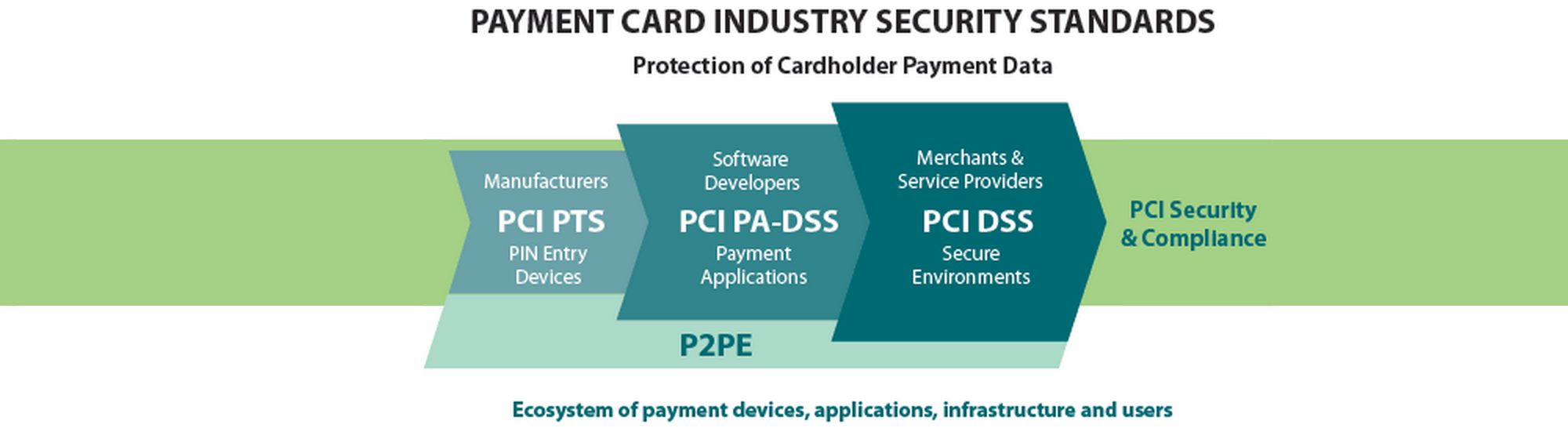
The Payment Card Industry Data Security Standard, or PCI DSS, emerged in the early 2000s in response to increasing security breaches within the payment card industry. Originally developed by major credit card companies like Visa and MasterCard, its primary purpose is to create a unified standard for protecting cardholder information.
Key goals of PCI DSS include:
- Ensuring the secure handling of payment card data.
- Minimizing risks of data breaches.
- Promoting trust among consumers regarding their financial transactions.
Entities Affected by PCI DSS
PCI DSS affects a wide range of entities involved in payment transactions, including:
- Merchants (both large and small)
- Payment processors
- Service providers
Any entity that stores, processes, or transmits cardholder information is subject to PCI DSS compliance.
Compliance Requirements
To maintain compliance, organizations must adhere to a set of requirements outlined in the PCI DSS framework. These include:
- Establishing a secure network.
- Protecting cardholder data.
- Regularly monitoring and testing networks.
By implementing these requirements, organizations not only comply with PCI DSS but also help in securing payment data effectively, showcasing their commitment to data security as highlighted on our blog, TECHFACK.

Understanding Payment Data Security
Types of Payment Data
When discussing payment data security, it’s essential to recognize the different types of payment data that require protection. Common forms include:
- Cardholder data: This includes the cardholder’s name, card number, expiration date, and CVV (Card Verification Value).
- Transactional data: Information related to purchases, such as the date, amount, and merchant details.
- Authentication data: Elements like PINs and passwords that help verify user identity during transactions.
Understanding these categories is crucial for anyone involved in payment processing.
Risks Associated with Payment Data Breaches
The risks of payment data breaches can be severe, affecting both individuals and organizations. Some noteworthy risks include:
- Financial loss: Businesses can face hefty fines and significant revenue decline due to loss of customer trust.
- Identity theft: Breaches often lead to victims suffering from fraud and other related crimes.
A personal experience with a data breach can serve as a reminder of why securing payment data is vital.
Impact of Non-Compliance
The repercussions of failing to comply with PCI DSS can be daunting. Organizations may face:
- Heavy fines: Typically ranging from $5,000 to $100,000 per month, depending on the level of non-compliance.
- Increased scrutiny: Regulatory bodies may impose stricter oversight.
Investing in payment data security isn’t just about compliance; it’s about safeguarding customer trust and avoiding potential fallout. This draws attention to the urgent need for effective strategies in securing payment data, something frequently emphasized on our blog, TECHFACK.

PCI DSS Compliance Framework
12 Requirements of PCI DSS
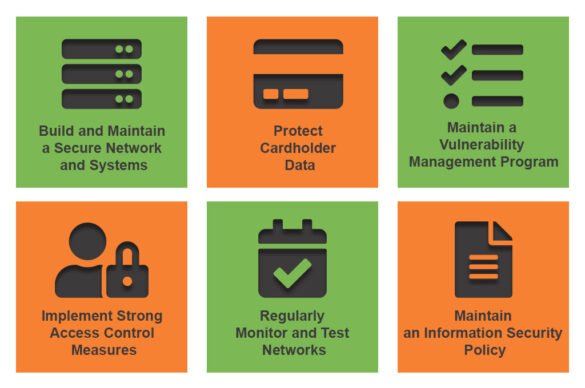
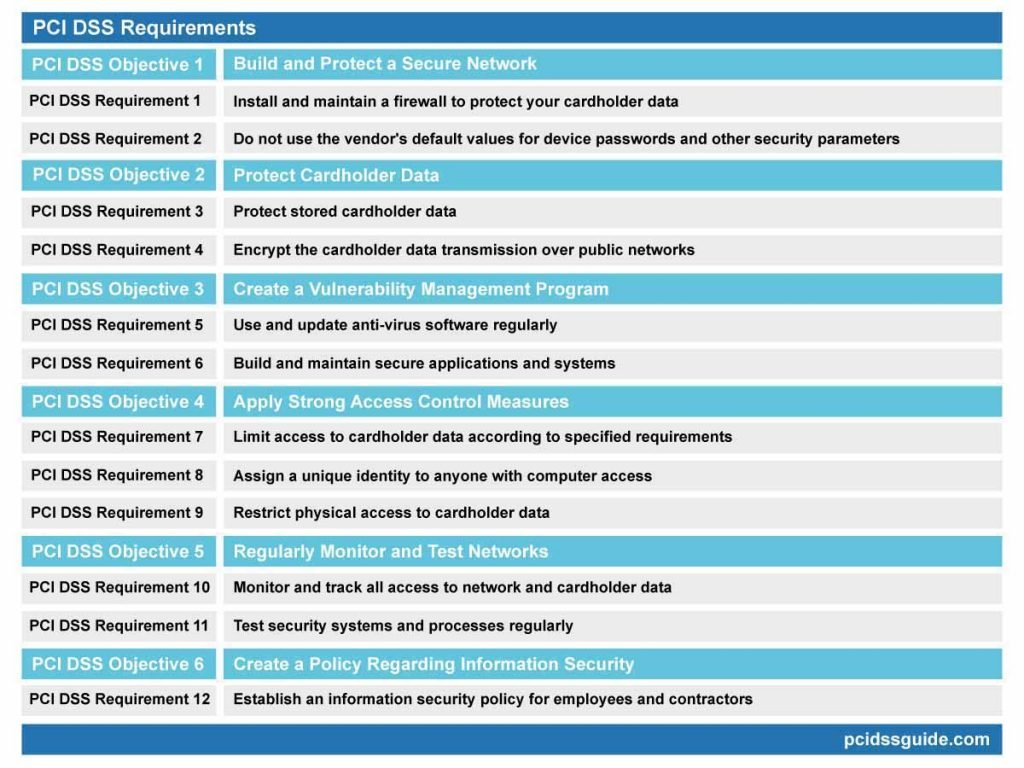
The PCI DSS compliance framework consists of 12 essential requirements designed to enhance payment security. These requirements cover everything from network security to data protection, ensuring a comprehensive approach to safeguarding cardholder information.
Build and Maintain a Secure Network
One of the foundational steps is to build and maintain a secure network. This includes implementing firewalls to protect cardholder data and ensuring that the default passwords on network devices are changed.
Protect Cardholder Data
It’s essential to encrypt cardholder data both in transit and at rest. For instance, using strong encryption protocols ensures that even if data is intercepted, it remains unreadable without the proper keys.
Maintain a Vulnerability Management Program
An effective vulnerability management program is critical. Regularly updating software and systems and conducting vulnerability assessments can significantly reduce the risk of exploitation.
Implement Strong Access Control Measures
Access control measures must be robust. Businesses should restrict access to cardholder data on a need-to-know basis and assign unique IDs to each person with computer access.
Regularly Monitor and Test Networks
Ongoing monitoring and testing of networks is vital. Conducting penetration tests can help identify weaknesses before they become security breaches.
Maintain an Information Security Policy
Finally, maintaining a well-defined information security policy ensures that all employees understand their roles in protecting cardholder data. This collective responsibility is key in fostering a culture of security, as frequently discussed on our blog, TECHFACK.

PCI DSS Compliance Validation
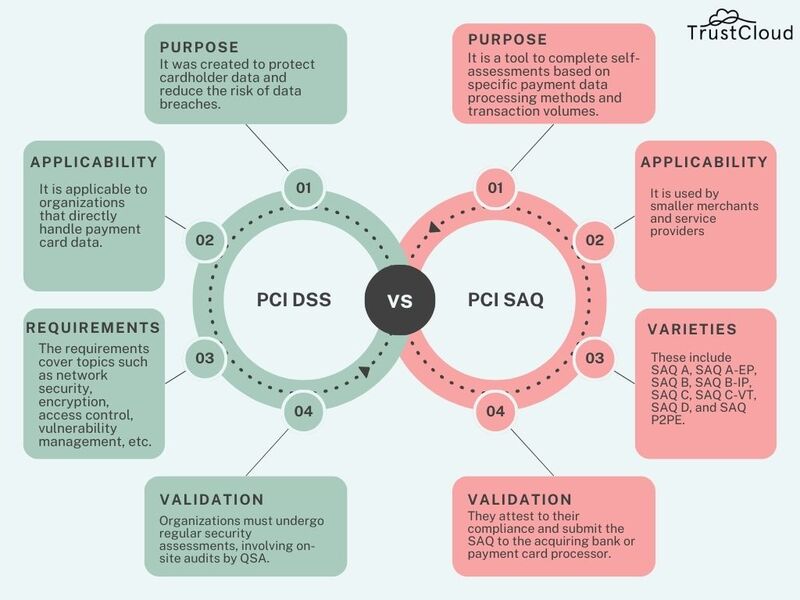
Self-Assessment Questionnaires (SAQs)
A crucial aspect of PCI DSS compliance validation is the use of Self-Assessment Questionnaires (SAQs). These SAQs enable organizations to assess their own compliance by answering a series of questions tailored to their payment processing activities. Depending on the volume of transactions processed, businesses can choose from various SAQ types, ensuring the assessment aligns with their specific situation.
For example:
- SAQ A: Ideal for merchants that do not store cardholder data.
- SAQ D: Geared towards larger organizations with more complex processing environments.
Penetration Testing and Vulnerability Scans
Regular penetration testing and vulnerability scans are also vital to validate compliance. Penetration testing helps identify any exploitable vulnerabilities before they can be acted upon by malicious entities. Organizations may hire third-party experts to simulate attacks, providing a clearer picture of their defenses.
Additionally, vulnerability scans assess the overall security of networks and must be conducted quarterly.
On-Site Audits by Qualified Security Assessors (QSAs)
For organizations processing large volumes of transactions, on-site audits by Qualified Security Assessors (QSAs) become necessary. These professionals rigorously evaluate compliance levels and provide recommendations. During one such audit, a colleague shared how invaluable the insights gained were, leading to broader organizational changes that enhanced overall security.
By following these validation steps, businesses reinforce their commitment to payment security, a key topic discussed on our blog, TECHFACK.
Challenges and Common Pitfalls in PCI DSS Compliance
Misconceptions About Compliance
As organizations navigate PCI DSS compliance, misconceptions often lead them astray. One common myth is that achieving compliance is a one-time event rather than an ongoing process. For instance, a business might believe that once they pass an audit, they can relax their security measures. In reality, continuous monitoring and updates are necessary to adapt to new threats.
Budget Constraints and Resource Limitations
Budget constraints and limited resources can also hinder compliance efforts. Many small to medium-sized businesses struggle to allocate adequate funds for security initiatives. This predicament often leads to subpar solutions. For example, a friend once shared how their company cut corners on necessary security tools, which eventually exposed them to a data breach.
Evolving Threat Landscape
The ever-evolving threat landscape presents another significant challenge. Cybercriminals constantly develop new and sophisticated techniques to exploit vulnerabilities. Organizations must stay vigilant and proactive, regularly updating their security measures to counter these threats.
By recognizing these challenges, businesses can create a more effective approach to PCI DSS compliance. Our blog, TECHFACK, often emphasizes the need for continuous adaptation in securing payment data.

Benefits of PCI DSS Compliance
Enhanced Data Security
One of the most significant benefits of PCI DSS compliance is enhanced data security. By adhering to the stringent requirements outlined in the standard, organizations can create a fortified shield around cardholder data. For example, a colleague shared how implementing encryption protocols not only secured their data but also gave them peace of mind knowing they had taken crucial steps to protect themselves against breaches.
Customer Trust and Reputation
Another vital advantage is the boost in customer trust and reputation. In today’s conscientious market, consumers are increasingly aware of the importance of data protection. By demonstrating compliance, businesses signal that they take security seriously, thereby attracting more customers. Positive word-of-mouth from satisfied customers can significantly enhance a company’s reputation.
Cost Savings in the Long Run
Lastly, investing in PCI DSS compliance can lead to substantial cost savings in the long run. While upfront costs may seem daunting, the potential costs of a data breach—fines, legal fees, and loss of business—far outweigh these initial investments. Companies often find that improved security leads to fewer incidents and decreased insurance premiums over time.
In essence, the transition toward PCI DSS compliance is not merely a regulatory obligation; it’s a smart business strategy discussed frequently on our blog, TECHFACK.

Case Studies and Examples
Successful Implementation Stories
Examining successful implementation stories can be incredibly inspiring. For instance, a mid-sized retail company recently transformed its payment security by adopting PCI DSS practices. They established a robust firewall, implemented encryption techniques, and conducted regular employee training. The results were impressive—after their compliance journey, they reported a 40% decrease in incidents related to payment fraud. This real-world experience illustrates the tangible benefits of committing to PCI DSS standards.
Lessons Learned from Data Breaches
Conversely, the lessons learned from notable data breaches underscore the critical importance of maintaining strong security measures. Take a well-known hospitality chain that faced a massive breach exposing millions of payment card details. The aftermath revealed that they had neglected regular vulnerability testing and employee security training. As a result, they spent millions on fines, legal fees, and remediation efforts.
These cautionary tales emphasize the necessity for proactive compliance and constant vigilance. By analyzing both success stories and cautionary tales, businesses can better appreciate the implications of PCI DSS compliance—which is frequently highlighted on our blog, TECHFACK.
Future Trends in Payment Data Security
Emerging Technologies in Data Protection
As technology evolves, so does the landscape of payment data security. Exciting innovations are emerging that promise to revolutionize how businesses protect sensitive information. For example, the rise of Artificial Intelligence (AI) is transforming fraud detection. AI algorithms can analyze transaction patterns in real-time, allowing organizations to spot anomalies and prevent fraudulent activities before they occur. A friend in the tech industry shared how integrating AI helped their company reduce false positives by 30%, streamlining their operations significantly.
Another technology gaining traction is tokenization, where sensitive data is replaced with unique identifiers or tokens. This minimizes the stored data vulnerabilities, ensuring that even if a breach occurs, the attackers gain little from the compromised tokens.
Regulatory Updates and Global Implications
In addition to technology, regulatory updates will shape the future of payment data security. As global commerce expands, so do the complexities of compliance. Organizations will need to navigate various regulations emerging from regions like the European Union with GDPR and different regional standards. This evolving regulatory landscape can bring challenges, but also opportunities for organizations willing to adapt.
Staying informed and agile becomes crucial in this dynamic environment—a topic we often explore on our blog, TECHFACK. Embracing both emerging technologies and regulatory changes will be key to securing payment data in the future.

Conclusion and Key Takeaways
Importance of Securing Payment Data
As we wrap up our exploration of payment data security, it becomes abundantly clear that securing payment data is not just a compliance issue—it’s a fundamental business necessity. With the increasing frequency of data breaches, safeguarding sensitive information should be a priority for organizations of all sizes. A colleague of mine once emphasized that protecting cardholder data builds customer trust, which is invaluable in a competitive market.
Key points to remember include:
- The direct correlation between secure payment data and customer loyalty.
- The potential financial ramifications—breaches can be far costlier than preventive measures.
Continuous Improvement in Data Security Practices
Finally, continuous improvement in data security practices is essential. Adopting a proactive approach to security means regularly updating protocols, participating in training, and keeping abreast of new technologies. Organizations should embrace the evolving landscape of payment security, committing to regular assessments and upgrades.
By fostering a culture of security awareness, businesses underscore their commitment to protecting not just their own interests, but also those of their loyal customers. This idea resonates throughout our discussions on TECHFACK, highlighting that proactive measures are the key to a secure future in payment data security.