Understanding Cyber Hygiene
Definition of Cyber Hygiene
At its core, cyber hygiene refers to a set of practices, tools, and habits that help individuals and organizations maintain the health and security of their digital systems. In a world that increasingly relies on technology, ensuring that sensitive information isn’t compromised is crucial. Think of cyber hygiene as the equivalent of washing your hands regularly; it’s about preventing problems before they occur.
Key components of cyber hygiene include:
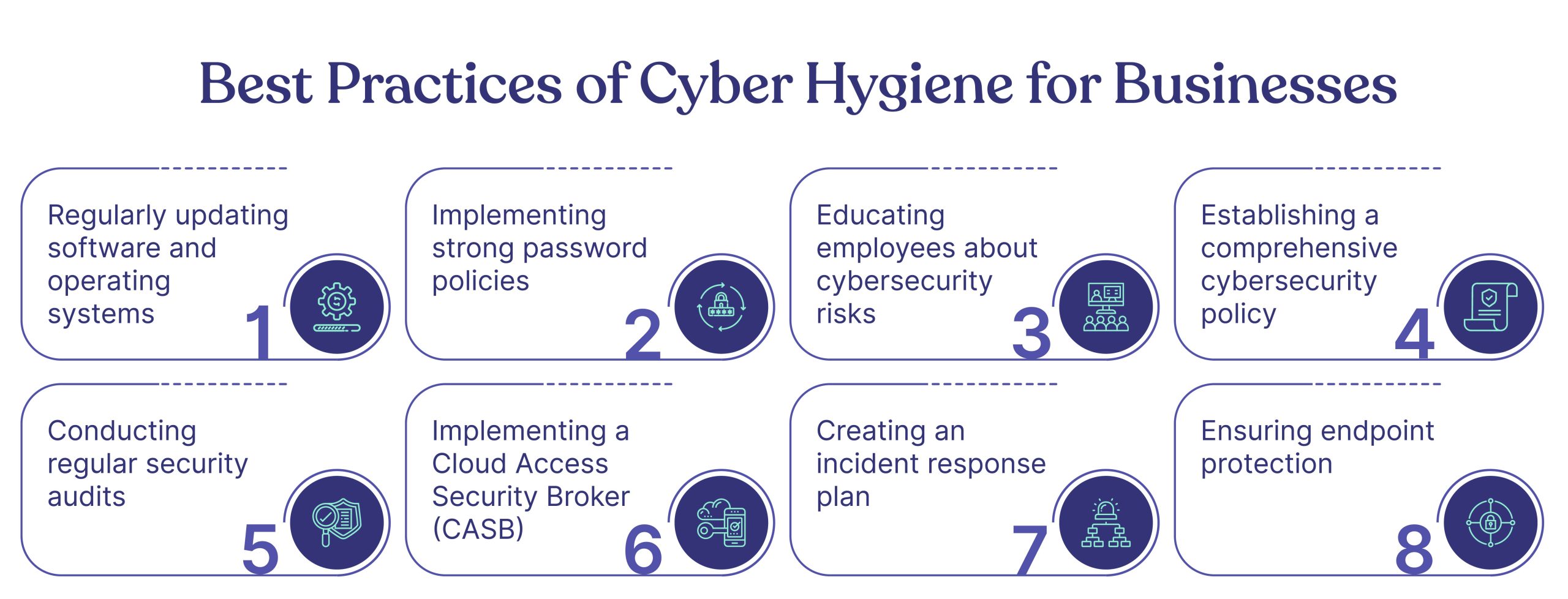
- Regularly updating software and systems
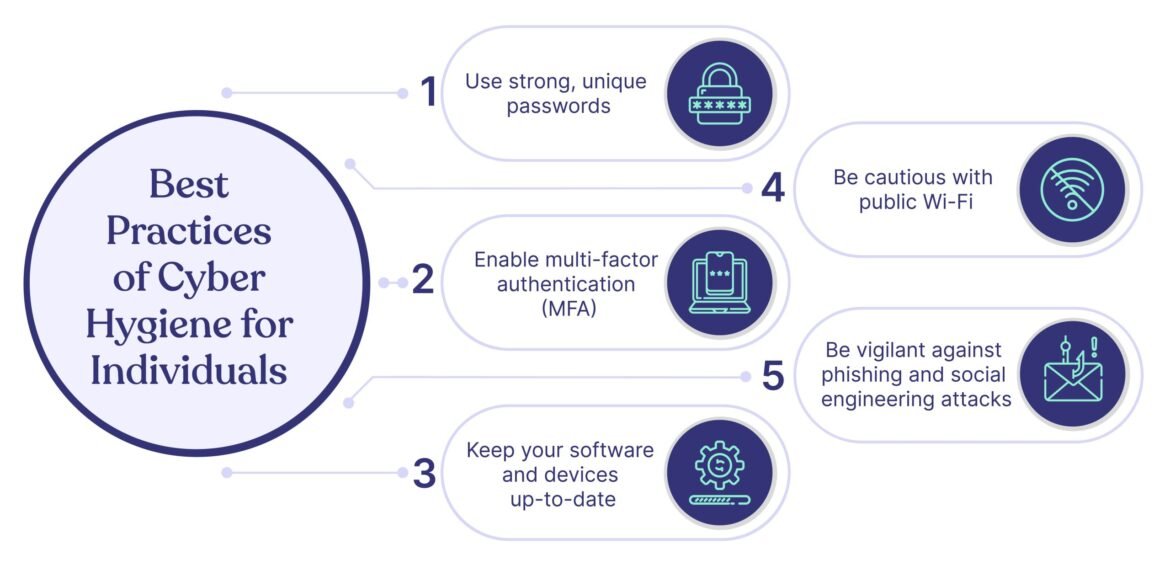
- Using strong, unique passwords
- Backing up important data
- Maintaining a secure network environment
Significance of Cyber Hygiene in the Digital Age
In today’s digital age, where breaches and attacks have become alarmingly common, maintaining cyber hygiene is more significant than ever. The interconnected nature of our devices means that a single vulnerability can lead to widespread exposure.
Consider the example of a small business that neglected its software updates. This oversight resulted in a data breach that not only compromised client information but also damaged the company’s reputation, leading to a loss of customer trust.
Implementing top strategies for maintaining cyber hygiene can significantly reduce the risk of cyber threats. Here are some compelling reasons why cyber hygiene is essential:
- Protection Against Data Breaches: Staying ahead of vulnerabilities minimizes the risk of unauthorized access.
- Compliance with Regulations: Many industries require adherence to specific cyber hygiene practices to safeguard consumer data.
- Enhanced Business Continuity: Ensuring the integrity of IT systems can help businesses recover swiftly from disruptions.
In wrapping up this section, it is clear that neglecting cyber hygiene is not an option. Just as routine check-ups are essential for personal health, proactive measures in cyber hygiene are crucial for safeguarding digital assets. This foundation sets the stage for exploring best practices that reinforce cyber hygiene effectively in the next sections of our discussion.

Cyber Hygiene Best Practices
Regular Software Updates
One of the most fundamental practices for maintaining good cyber hygiene is keeping software regularly updated. Many might see those update reminders as annoyances, but they play a crucial role in security. Software updates often contain patches that fix vulnerabilities exploited by cybercriminals.
For instance, a well-known company suffered a data breach when it failed to update its key software, allowing hackers to exploit an outdated system. This could have been avoided with timely updates.
Here are a few tips to ensure proper update management:
- Enable automatic updates whenever possible.
- Schedule regular reminders to check for updates manually.
- Keep track of which software requires regular checks, like operating systems, browsers, and antivirus programs.
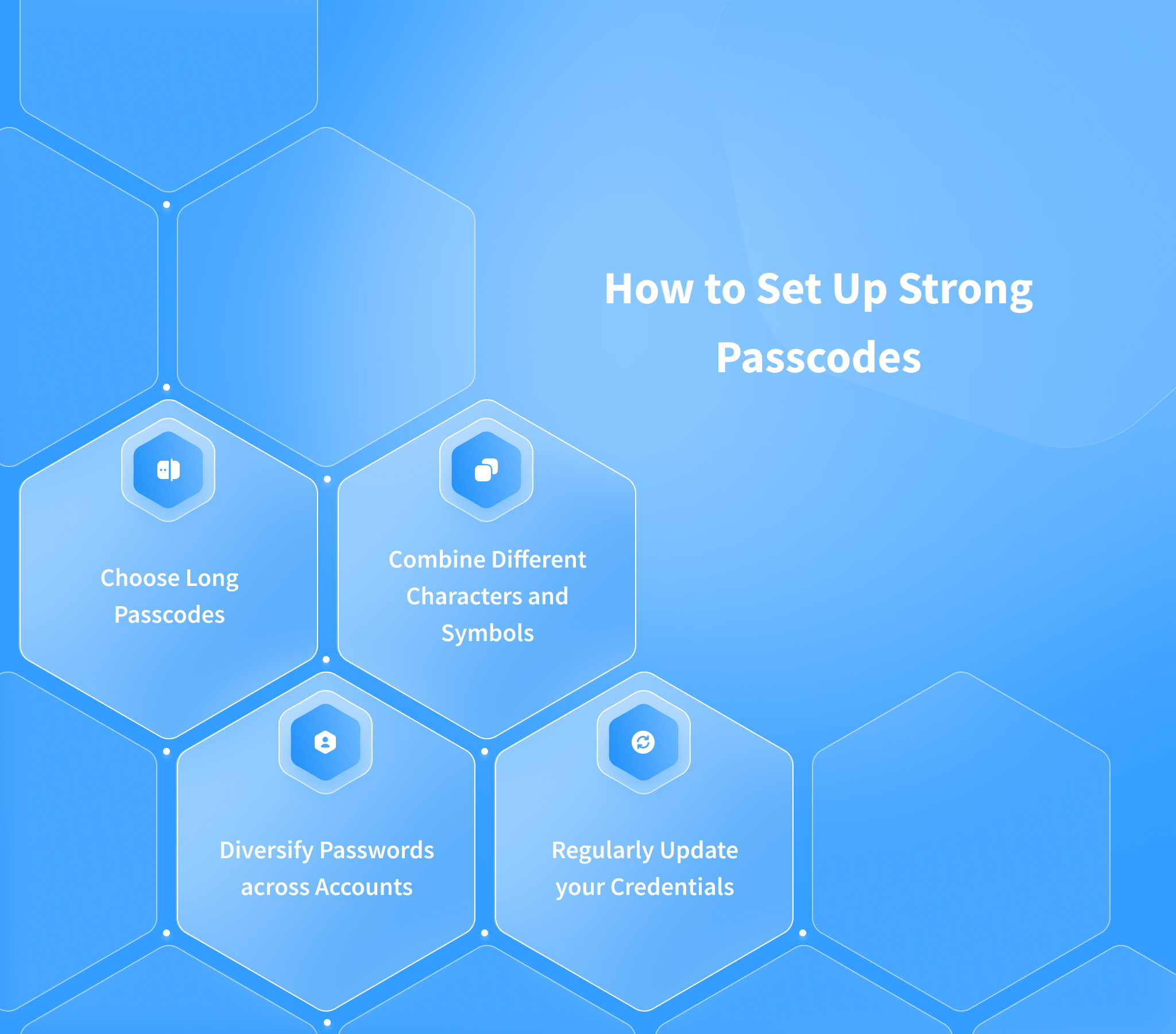
Strong Password Management
Next up is the importance of strong password management. With numerous online accounts, it’s easy to reuse passwords, but this is a dangerous habit. A strong password should typically contain a mix of uppercase letters, lowercase letters, numbers, and special characters, at least 12 characters in length.
Consider using a password manager, which can help:
- Generate complex passwords.
- Store and encrypt those passwords securely.
- Automatically fill them in on websites, making your life easier.
Secure Network Configurations
Lastly, securing network configurations is critical to cyber hygiene. An unsecured network can act as an open door for cybercriminals. Ensure that your Wi-Fi network is protected with WPA3 security, which is more robust than previous encryption standards.
To further bolster your network security, consider the following:
- Change default passwords on routers and devices.
- Enable network encryption.
- Regularly check connected devices for any unauthorized access.
By implementing these best practices, individuals and organizations can greatly enhance their cyber hygiene. In the next section, we will discuss how employee training and awareness play a pivotal role in reinforcing these cybersecurity measures.

Employee Training and Awareness
Importance of Educating Employees
Following effective cyber hygiene best practices is crucial, but equally important is the education of employees in an organization. Human error remains one of the leading causes of security breaches. No matter how tight the technological controls are, a single mistake can open the floodgates for cybercriminals.
For instance, consider a scenario where an employee accidentally clicks on a phishing link in an email that appears legitimate. This simple action could inadvertently grant hackers access to sensitive data. This is why it’s essential to foster a culture of cybersecurity awareness among all employees.
Key aspects to focus on include:
- Recognizing phishing attempts and scams.
- Understanding the importance of secure password practices.
- Learning how to report suspicious activities promptly.
Educated employees become your first line of defense against cyber incidents, so investing time in their training is vital.
Implementing Effective Cybersecurity Awareness Programs
To elevate the concept of employee training, organizations should implement robust cybersecurity awareness programs. These programs should be engaging and relatable to encourage participation.
Here are some effective components of successful programs:
- Interactive Workshops: Host regular workshops where employees can practice identifying phishing emails and participating in exercises on password security.
- Simulation Exercises: Conduct simulated phishing campaigns to test employees’ responsiveness. This can help highlight vulnerabilities and areas for improvement.
- Regular Updates and Refresher Courses: Cyber threats evolve, so keeping the training material updated and providing refresher courses ensures employees stay informed about the latest trends and threats.
Incorporating these elements into a comprehensive training program transforms employees into vigilant cybersecurity allies. As we move forward, the emphasis on data backup and recovery strategies becomes crucial to safeguarding valuable information in the event of a breach.

Data Backup and Recovery Strategies
Importance of Data Backups
As we’ve discussed the significance of employee training and awareness, another critical aspect of cyber hygiene that cannot be overlooked is data backup. Imagine the panic of losing important files or sensitive data due to a ransomware attack or a hardware failure. Data backups are your safety net in such scenarios, ensuring that you can recover essential information without significant disruption.
In today’s fast-paced digital landscape, the importance of regular data backups can be underscored by considering the following:
- Protection Against Data Loss: Backups safeguard your data from accidental deletion, corruption, or theft.
- Maintaining Business Continuity: Quick restoration of data enables organizations to continue operations, minimizing downtime.
- Compliance and Security: Many industries require data retention and backup protocols to meet regulatory standards.
It’s not merely a ‘nice to have’; it’s a necessity in this era of cyber threats.
Developing a Data Recovery Plan
Having backups in place is only part of the equation; you also need a robust data recovery plan. This plan provides a clear strategy for retrieving lost data effectively and efficiently.
Key elements to consider when developing your data recovery plan include:
- Identify Critical Data: Determine which data is essential and prioritize its protection and recovery.
- Test Your Backup System: Regularly test your backups to ensure that you can restore data smoothly.
- Define Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO): RTO defines how quickly you need to recover data after a loss, while RPO determines how much data you can afford to lose, guiding your backup frequency and strategy.
By codifying these strategies into a structured data recovery plan, businesses can significantly mitigate risks associated with data loss. With this foundation in place, the next focus will shift towards utilizing multi-factor authentication as an essential layer of security.
Utilizing Multi-factor Authentication
Why Multi-factor Authentication is Essential
Building on the foundation of a solid data recovery plan, the next step in enhancing cyber hygiene involves utilizing multi-factor authentication (MFA). In today’s world, relying solely on passwords can be idyllic yet perilous. Passwords can be hacked, stolen, or easily guessed. Here’s where MFA steps in as a game changer.
Multi-factor authentication adds an additional layer of security by requiring users to provide two or more verification factors to gain access to an account. This could include:
- Something you know (password)
- Something you have (a mobile device or hardware token)
- Something you are (biometric verification like fingerprints)
Implementing MFA offers significant advantages:
- Increased Security: Even if a password is compromised, attackers would still need the second factor to access sensitive information.
- Reduced Risk of Fraud: It decreases the chances of unauthorized access, especially for financial accounts or sensitive corporate data.
- Enhanced Customer Trust: Users feel more secure when they know there are multiple layers protecting their information.
Implementing Multi-factor Authentication Across Platforms
Now that we understand the importance of MFA, let’s dive into how to implement it across various platforms.
Here are practical steps to incorporate MFA effectively:
- Choose the Right Authentication Method: Depending on the sensitivity of the data and user convenience, select methods like SMS codes, authentication apps, or hardware tokens.
- Educate Employees: Provide training on the importance of MFA and how to set it up. Employees must understand its nuances to appreciate its value fully.
- Enable MFA on All Platforms: Implement MFA on critical systems, including email accounts, cloud services, and internal networks. Every additional layer counts!
Incorporating these steps not only enhances security but also empowers users with control over their accounts. As we continue to strengthen their defenses, our next discussion will focus on monitoring and assessing cybersecurity measures effectively to keep threats at bay.

Monitoring and Assessing Cybersecurity Measures
Regular Security Audits
After implementing robust security measures like multi-factor authentication, it’s crucial to continuously monitor and assess those cybersecurity measures. One of the most effective ways to do this is through regular security audits. These audits act like health check-ups for your cybersecurity posture, ensuring that all systems are running smoothly and identifying potential weaknesses before they can be exploited.
Imagine conducting a quarterly audit that reveals a vulnerable software version still in use, which might have been overlooked in regular updates. By identifying this issue early, organizations can address it proactively, preventing a potential security breach. Here are essential steps in conducting effective security audits:
- Schedule Regular Audits: Make this a recurring event; quarterly or bi-annually works well based on organizational needs.
- Use Comprehensive Checklists: Create a checklist that covers all aspects of your cybersecurity measures, including hardware, software, policies, and user behaviors.
- Engage Third-party Experts: Sometimes, it helps to bring in outside professionals to provide a fresh perspective on potential vulnerabilities.
Incident Response Planning
While regular audits help identify weaknesses, having a robust incident response plan is equally important. Any organization can face a cybersecurity incident; what matters is how you respond. An effective incident response plan helps mitigate risks and reduce damage.
Key activities in incident response planning include:
- Developing Clear Protocols: Outline the steps employees should take when they suspect a breach. Who should they notify? What immediate actions should be taken?
- Conducting Drills: Simulate real-world scenarios to test the effectiveness of your incident response plan. This helps familiarize employees with their roles during an actual emergency.
- Regularly Review and Update: Cyber threats evolve quickly, so it’s vital to keep your incident response plan current.
By integrating regular security audits and having a well-thought-out incident response plan, organizations can significantly enhance their cybersecurity posture. Moving forward, we’ll discuss the importance of engaging in secure online behavior, another essential line of defense in today’s digital landscape.

Engaging in Secure Online Behavior
Avoiding Phishing Scams
Transitioning from the importance of monitoring and assessing cybersecurity measures, let’s delve into the realm of secure online behavior. One of the most critical aspects of staying safe online is avoiding phishing scams. Phishing attacks have become increasingly sophisticated, making it harder for even the most vigilant users to spot them.
Consider a scenario where an employee receives an email from what appears to be a well-known bank, requesting account verification. If they click the link and enter their sensitive information, they might unknowingly expose themselves to fraud. To avoid falling victim to these scams, keep the following tips in mind:
- Examine Email Addresses Carefully: Look for small discrepancies in the sender’s address that indicate it’s suspicious.
- Don’t Click Unverified Links: Instead of clicking links in unsolicited emails, navigate to the website directly through a browser.
- Verify with the Source: If in doubt, contact the company directly using official communication methods to confirm the legitimacy of the request.
Exercise Caution with Downloads and Links
Another essential component of secure online behavior is exercising caution with downloads and links. Many users might not realize that malicious software can be hiding behind innocent-looking files or links.
Here are some best practices to follow:
- Use Trusted Sources: Only download software or files from reputable websites and avoid random links shared via social media or email.
- Check File Extensions: Be wary of executable files (like .exe, .scr) disguised as documents or images.
- Utilize Antivirus Software: Regularly update and run antivirus programs to scan downloaded files before opening them.
Incorporating these behaviors into your daily online interactions not only helps protect individual users but also fortifies an organization’s security as a whole. As we continue this journey towards robust cyber hygiene, next, we will explore the benefits of collaborating with cybersecurity experts to reinforce defenses further.

Collaboration with Cybersecurity Experts
Seeking Professional Consultation
As we wrap up our discussion on engaging in secure online behavior, it’s vital to highlight the significance of collaborating with cybersecurity experts. In an evolving digital landscape filled with complex threats, seeking professional consultation can significantly bolster an organization’s security posture.
Imagine being a small business overwhelmed by the myriad of cybersecurity options available—firewalls, encryption, or intrusion detection systems. Navigating this landscape alone can be daunting. That’s where cybersecurity consultants shine. They offer expert insights that can help identify potential vulnerabilities within your organization.
When seeking professional consultation, consider the following:
- Assess Specific Needs: Determine what areas your organization requires assistance with—incident response, risk assessment, or compliance with regulations.
- Look for Credentials: Ensure the experts you engage with have the necessary certifications and expertise, such as Certified Information Systems Security Professional (CISSP).
- Collaborate on Solutions: Work with them to develop tailored solutions that fit your organization’s unique requirements.
Cybersecurity Partnerships for Enhanced Protection
Beyond individual consultations, forming strategic partnerships with cybersecurity firms can offer a comprehensive approach to security. These collaborations provide continuous access to advanced resources, knowledge, and technology, creating a formidable defense against cyber threats.
Consider these advantages of establishing cybersecurity partnerships:
- Access to Specialized Tools: Partnering with cybersecurity experts can give you access to the latest tools and technologies that might be cost-prohibitive to acquire independently.
- Ongoing Support and Monitoring: Many firms offer managed services, providing regular monitoring and assessment to detect threats proactively.
- Shared Knowledge and Training: Building these partnerships often involves knowledge exchange, ensuring your team stays updated on the latest cyber threats and defense techniques.
In conclusion, engaging with cybersecurity experts through consultation and partnerships is a proactive step towards a robust security strategy. Together, we can fortify defenses, ensuring organizations remain one step ahead against the threats lurking in the digital world. As we wrap up, it’s clear that implementing a thorough approach to cyber hygiene is essential in safeguarding valuable information and fostering organizational resilience.