Understanding Cybersecurity for Small Businesses
Overview of Cybersecurity
Cybersecurity revolves around the practices and technologies designed to safeguard systems, networks, and data from digital attacks. With the advancement of technology, cyber threats have also evolved, making it essential for businesses, especially small ones, to be well-equipped. Think of cybersecurity as a lock on your door. It not only keeps intruders out but also ensures peace of mind.
Why Cybersecurity is Important for Small Businesses
For small businesses, the importance of cybersecurity cannot be overstated. Many may feel they are too small to attract cybercriminals, yet statistics say otherwise.
- Data Protection: Small businesses often handle sensitive customer and employee data, which can be a tempting target.
- Reputation Management: A data breach can severely harm a brand’s reputation, leading to a loss of trust.
- Financial Security: Cyber attacks can lead to direct financial loss, and recovery can be costly.
Personal experience at TECHFACK has shown that even a minor breach can disrupt operations for days. Investing in cybersecurity is not just a precaution; it’s a necessity for long-term sustainability.
Identifying Cybersecurity Threats
Common Cyber Threats Faced by Small Businesses
As small businesses navigate the digital landscape, it’s crucial to understand the common cyber threats that lurk around every corner. These include:
- Phishing Attacks: Cybercriminals often masquerade as trustworthy entities to trick employees into sharing sensitive information.
- Malware: Malicious software can infiltrate systems, causing harm and data loss.
- Ransomware: This insidious type of malware locks users out of their data until a ransom is paid.
At TECHFACK, we encountered a phishing attempt that targeted our email accounts, highlighting just how easily a team can be compromised.
Risks Associated with Cyber Attacks
The risks of cyber attacks extend beyond immediate data loss. They can have long-lasting repercussions:
- Financial Loss: Beyond the ransom or recovery costs, the financial impact can include lost revenue during downtime.
- Legal Consequences: Failing to protect customer data can lead to legal liabilities, including hefty fines.
- Operational Disruption: Cyber incidents can halt business activities, affecting productivity and customer satisfaction.
Understanding these threats helps small businesses stay vigilant and proactive in their cybersecurity efforts.

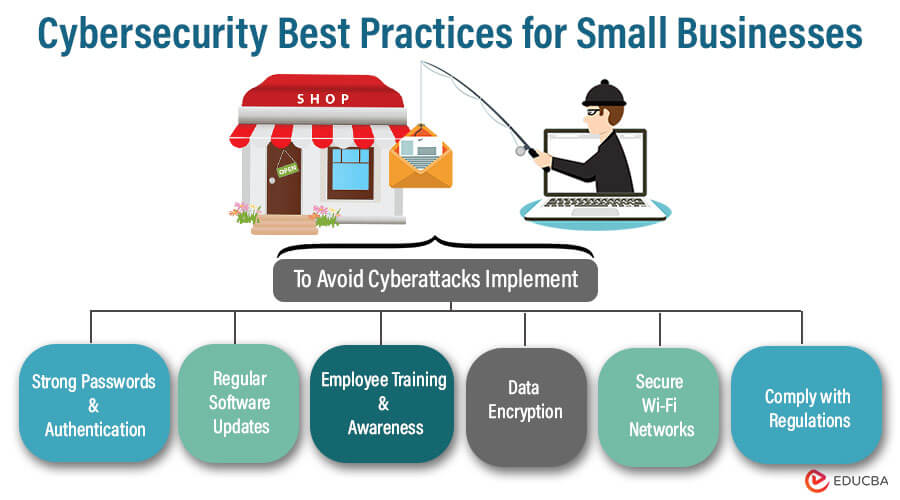
Implementing Cybersecurity Measures
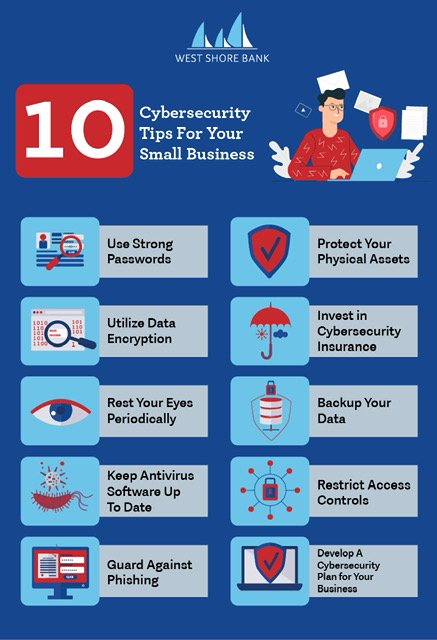
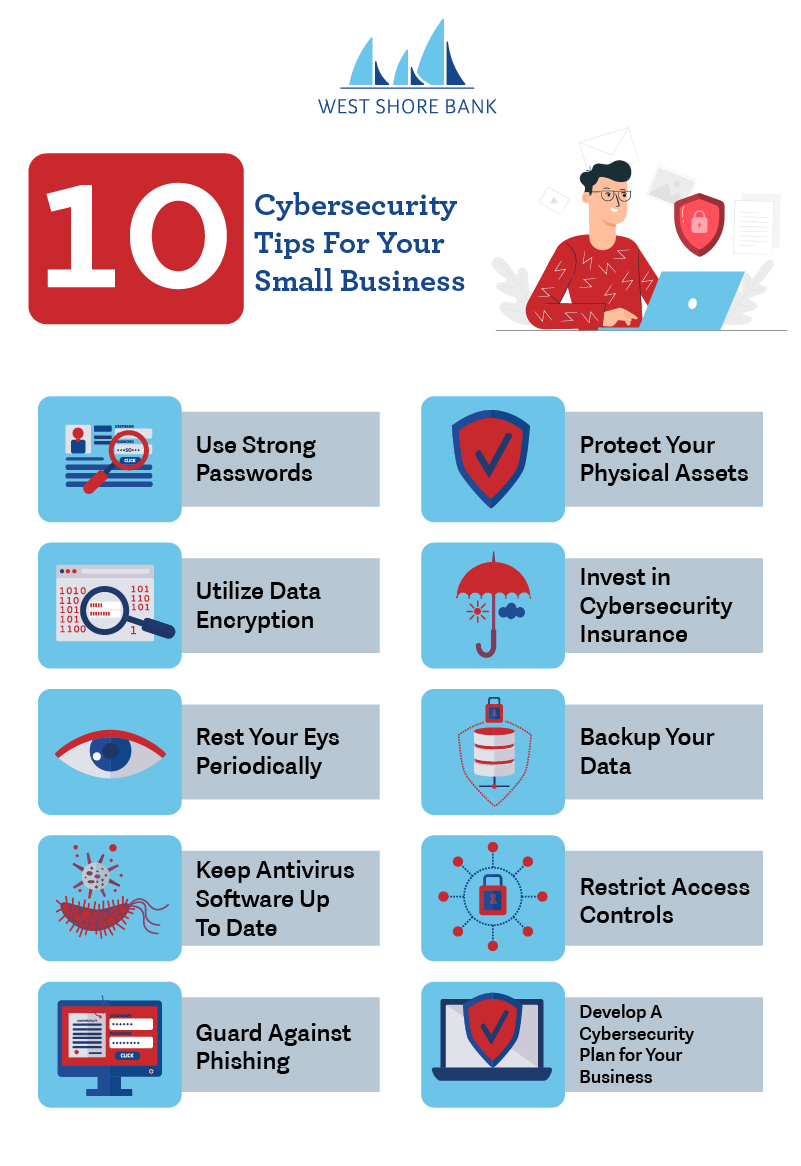
Creating Strong Passwords
Now that we’ve identified common cyber threats and their associated risks, it’s time to adopt effective cybersecurity measures. One fundamental step is creating strong passwords. A strong password should be:
- At least 12 characters long
- A mix of upper and lowercase letters, numbers, and special characters
- Unique—never reuse passwords across different accounts
I remember a colleague at TECHFACK who had a simple password and faced a breach. It was a wake-up call for all of us!
Regularly Updating Software and Systems
Equally important is the practice of regularly updating software and systems. Updates often include security patches designed to combat newly discovered vulnerabilities.
- Set automatic updates whenever possible to stay ahead of threats.
- Keep an inventory of all software and devices to ensure nothing is overlooked.
This not only strengthens defenses but also enhances performance.
Backing Up Data Securely
Finally, regular data backups are crucial. In the event of a cyber attack, having a secure backup allows for swift recovery:
- Frequency: Backup data daily or weekly, depending on your business needs.
- Storage Method: Use both cloud storage and physical drives for redundancy.
At TECHFACK, we’ve made a habit of backing up our data weekly, helping us breathe easier knowing that our work is protected should the unthinkable happen.

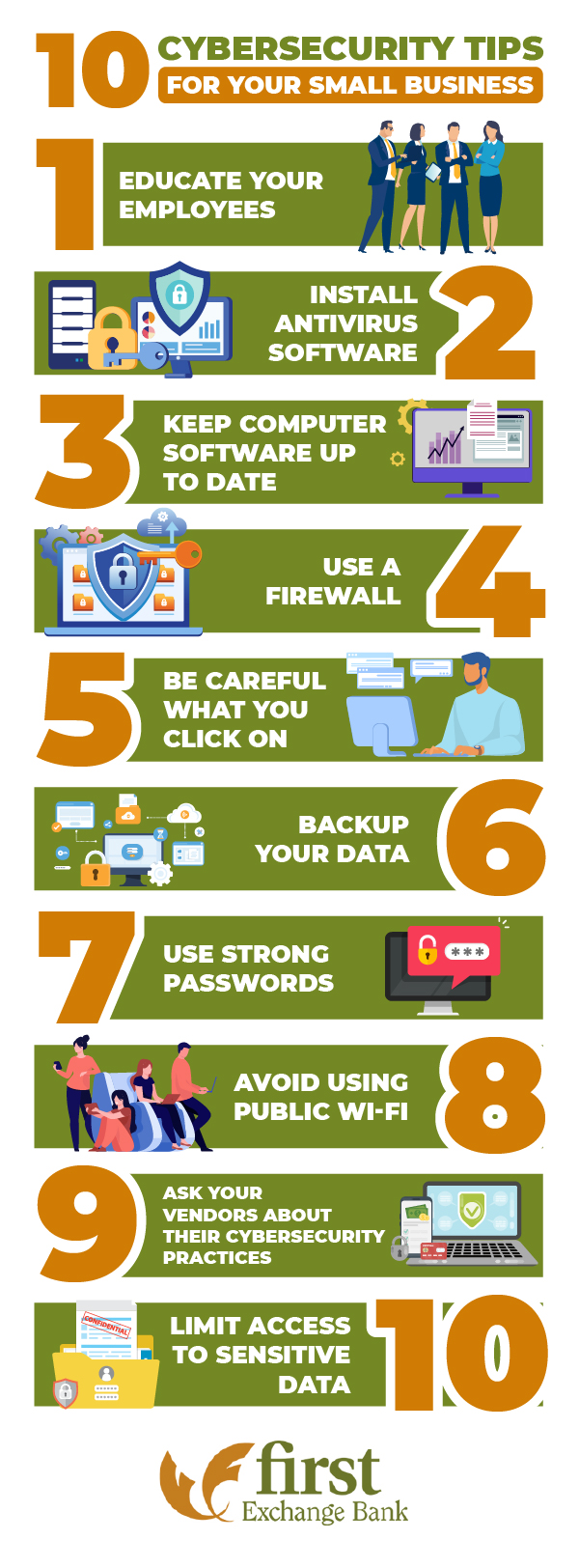
Educating Employees on Cybersecurity
Importance of Employee Training
With robust cybersecurity measures in place, the next critical component is educating employees on security best practices. Training helps everyone recognize that cybersecurity is not just the IT department’s responsibility; it’s a collective effort.
- Regular training sessions can cover topics such as:
- Identifying phishing emails
- Safeguarding personal devices
- Reporting suspicious activities
At TECHFACK, we experienced a situation where an employee identified a phishing attempt during training, preventing a potential breach. That speaks volumes about the value of proper education!
How to Promote a Cybersecurity Culture in the Workplace
Fostering a cybersecurity culture in the workplace involves creating an environment where security is prioritized. Here are some strategies:
- Open Communication: Encourage employees to share concerns without fear of repercussions.
- Gamification: Use games or competitions to make learning fun and engaging.
- Regular Updates: Share the latest threats and tips through newsletters or meetings.
By embedding cybersecurity practices into the company culture, employees become vigilant guardians of sensitive information, creating a safer workspace for everyone.

Securing Networks and Devices
Secure Wi-Fi Networks
Continuing our journey towards comprehensive cybersecurity, securing networks and devices is essential. The first step is ensuring your Wi-Fi networks are secure. Unprotected networks can serve as gateways for cybercriminals. Here’s how to fortify your Wi-Fi:
- Change the default SSID: Use a unique name that doesn’t reveal personal information.
- Use WPA3 security: The latest encryption standard offers enhanced protection.
- Create a guest network: Limit access for visitors to keep your main network secure.
At TECHFACK, after implementing these changes, we noticed a significant decrease in unauthorized access attempts.
Use of Firewalls and Antivirus Software
Another crucial element in securing your network is utilizing firewalls and antivirus software.
- Firewalls: They act as barriers that monitor and control incoming and outgoing network traffic. A good quality firewall can prevent unauthorized access to your network.
- Antivirus Software: Regularly updated antivirus software scans for and removes malware before it can cause harm.
Together, these measures bolster your defenses and maintain a robust cybersecurity posture, ensuring that your systems and data remain safe from potential intrusions.
Responding to Security Incidents
Developing an Incident Response Plan
As we delve deeper into cybersecurity, it’s crucial to be prepared for the unexpected—security incidents. Developing a solid incident response plan is the first step in that preparation. An effective plan should include:
- Roles and Responsibilities: Designate a response team with clear responsibilities.
- Communication Channels: Establish protocols for notifying stakeholders both internally and externally.
- Response Procedures: Outline specific steps to take when a breach is detected, including evidence preservation.
At TECHFACK, having a structured plan in place allowed us to react promptly during a minor incident, minimizing disruption.
Steps to Take When a Security Breach Occurs
When a security breach does happen, swift action can mitigate damage. Here are key steps to follow:
- Identify the Extent of the Breach: Determine what systems or data were compromised.
- Contain the Incident: Isolate affected systems to prevent further damage.
- Eradicate the Threat: Remove any malicious software or unauthorized access points.
- Notify Affected Parties: Keep customers and stakeholders informed about the incident.
- Review and Revise: After managing the situation, review your incident response plan and adjust it based on what was learned.
By acting quickly and decisively, businesses can recover more smoothly from security breaches, reinforcing the importance of thorough preparation.
Monitoring and Auditing Cybersecurity Measures
Importance of Regular Monitoring
As we pivot towards ensuring long-term cybersecurity resilience, regular monitoring of your systems is paramount. Without consistent oversight, vulnerabilities can go unnoticed. Regular monitoring helps to:
- Detect unusual activity in real-time, allowing for quicker responses.
- Identify potential weak points in your cybersecurity setup.
- Ensure compliance with established security policies.
For instance, at TECHFACK, we noticed irregular traffic patterns through monitoring, which prompted us to investigate further and strengthen our defenses without any compromise.
Conducting Security Audits
Beyond monitoring, conducting regular security audits is essential for a comprehensive approach to cybersecurity. Think of audits as health check-ups for your cybersecurity framework:
- Evaluate Policies: Review existing security policies to ensure they align with current threats.
- Assess Controls: Test the effectiveness of your security measures and identify areas for improvement.
- Document Findings: Keep a record of audit results and use them to guide future enhancements.
By incorporating these practices, businesses can continuously refine their cybersecurity strategy, cementing a strong defense against ever-evolving threats. This proactive approach not only protects sensitive data but also fosters a culture of security awareness among employees.

Compliance with Regulations
Understanding Legal Requirements
As we continue building a robust cybersecurity fortress, compliance with regulations is a cornerstone that shouldn’t be overlooked. Understanding legal requirements concerning data privacy and protection can be overwhelming, but it is crucial. Key regulations to consider include:
- GDPR (General Data Protection Regulation): Affects businesses dealing with European Union citizens, emphasizing data protection.
- HIPAA (Health Insurance Portability and Accountability Act): Sets standards for handling sensitive patient information in the healthcare sector.
- CCPA (California Consumer Privacy Act): Grants California residents more control over their personal data.
At TECHFACK, we ensure our practices align with these laws, fostering trust with customers.
Ensuring Compliance with Data Protection Laws
Ensuring compliance with data protection laws involves more than just understanding them—it requires taking actionable steps. Here’s how to get started:
- Conduct Regular Trainings: Equip employees with knowledge about compliance and data handling protocols.
- Develop Clear Policies: Create clear privacy policies that explain data collection and usage to customers.
- Regularly Review Procedures: Make it a habit to review and update your compliance measures with evolving regulations.
By prioritizing compliance, businesses not only avoid legal repercussions but also enhance their reputation in an increasingly data-conscious world. This commitment ultimately paves the way for stronger customer relationships and sustained business growth.

Investing in Professional Cybersecurity Services
Benefits of Outsourcing Cybersecurity
Transitioning from compliance to enhancing security measures, investing in professional cybersecurity services can be a game changer. Outsourcing your cybersecurity needs brings several advantages, such as:
- Expertise: Gain access to specialized knowledge and skills that may not be available in-house.
- Cost-Effectiveness: Reduce expenses related to hiring, training, and maintaining a full-time cybersecurity team.
- 24/7 Monitoring: Many service providers offer round-the-clock surveillance, ensuring threats are addressed promptly.
At TECHFACK, partnering with an external cybersecurity firm enhanced our defenses tremendously, allowing us to focus more on core business operations.
Selecting the Right Cybersecurity Service Provider
Choosing the right cybersecurity service provider is crucial for maximizing benefits. Here are some tips to guide your selection:
- Assess Experience: Look for providers with a proven track record in your industry.
- Check Certifications: Ensure they hold relevant certifications, such as CISSP or CISM, that demonstrate expertise.
- Read Reviews: Customer testimonials can provide insight into their reliability and effectiveness.
Taking the time to find the right partner not only protects your assets but can also lead to a more resilient business model, safeguarding your future in an ever-evolving cybersecurity landscape.

Conclusion and Recap of Top Cybersecurity Practices for Small Businesses
As we wrap up this comprehensive guide on cybersecurity, it’s clear that small businesses face unique challenges yet have numerous strategies at their disposal to enhance their security posture. It’s not just about implementing technical solutions but fostering a culture of security and awareness within the organization.
Recap of Top Cybersecurity Practices
Here’s a quick recap of the essential practices discussed:
- Create Strong Passwords: Use complex and unique passwords for each account.
- Regularly Update Software: Keep systems current to protect against vulnerabilities.
- Educate Employees: Invest in ongoing training and awareness programs.
- Conduct Regular Audits: Monitor systems and policies for compliance and effectiveness.
- Outsource Expertise: Consider professional cybersecurity services for specialized support.
At TECHFACK, embracing these practices has made a significant difference in our security resilience. By adopting these strategies, small businesses can navigate the digital landscape with confidence and focus on growth, knowing their assets and data are better protected.