
Introduction
Definition of Cybersecurity
In today’s interconnected world, cybersecurity stands as a critical pillar of digital integrity. It encompasses the practices and technologies designed to safeguard devices, networks, and sensitive information from cyber threats. Simply put, cybersecurity is about protecting your digital assets from unauthorized access, attacks, and damage. Imagine your personal data, financial details, and business secrets being exposed to malicious entities—cybersecurity aims to prevent such scenarios by ensuring confidentiality, integrity, and availability of information.
Significance of Cybersecurity in the Digital Era
With billions of people online and a staggering amount of data exchanged every second, the significance of cybersecurity has never been more pronounced. Consider these points:
- Rising Cyber Threats: As technology evolves, so do the tactics of cybercriminals. Phishing, ransomware, and data breaches are all too common.
- Trust and Reputation: Businesses that prioritize cybersecurity enhance their reputation and foster customer trust. When customers feel secure, they are more likely to engage.
- Regulatory Compliance: Numerous regulations, such as GDPR, mandate stringent data protection practices, making cybersecurity a legal necessity for organizations.
A personal anecdote highlights this importance: a friend once experienced a data breach, which not only led to financial losses but also strained relationships with clients. This incident underlined the critical role of cybersecurity in not just protecting data but also in maintaining a positive operational reputation. In this digital age, safeguarding digital information is paramount—it’s the difference between thriving and merely surviving.

Evolution of Cyber Threats
Historical Perspective
Understanding the evolution of cyber threats is crucial for grasping their current impact in our digital landscape. The history of cyber threats dates back to the early days of the internet, when the first worm, known as the Morris Worm, was released in 1988. It affected around 6,000 computers and remains a monumental event in cybersecurity history. During these early years, malicious activity was often the work of individual hackers looking for notoriety rather than financial gain.
Fast forward to the late 1990s and early 2000s, and the game began to change dramatically. The rise of e-commerce and online banking brought about a more organized approach to cybercrime. Cybercriminals began employing more sophisticated attacks, such as distributed denial-of-service (DDoS) attacks, that aimed to cripple websites and services.
Modern Cyber Threat Landscape
Today’s cyber threat landscape is both more complex and alarming. The motivations behind cyber attacks have shifted significantly—financial gain, data theft, and political reasons are now common catalysts. Consider this modern timeline of cyber threats:
- Ransomware Attacks: These have surged, with criminals encrypting user data and demanding payment for its release.
- Phishing Scams: As seen in many recent data breaches, these scams trick users into providing sensitive information unwittingly.
- Advanced Persistent Threats (APTs): These involve coordinated, long-term campaigns targeting organizations for espionage or data theft.
A vivid example is the 2020 SolarWinds attack, where a sophisticated supply-chain attack compromised multiple government agencies and corporations. This incident serves as a stark reminder of the increasing complexity of today’s cyber threats, highlighting the ever-urgent need for robust cybersecurity measures.

Importance of Cybersecurity Measures
Data Protection
Building on the understanding of evolving threats, it’s essential to emphasize the importance of cybersecurity measures, particularly in the realm of data protection. In a world where information is often referred to as the new currency, safeguarding sensitive data has become paramount. Just think of how much personal, financial, and operational information your organization holds—each piece forms the bedrock of your digital presence.
Effective cybersecurity measures can include:
- Encryption: This process converts data into a secure format, making it unreadable without the proper keys. It’s a crucial line of defense against unauthorized access.
- Regular Backups: Creating and maintaining backups of critical data ensures that, even in the event of ransomware or other destructive attacks, vital information can be restored quickly.
In my own experience as a business owner, implementing these measures allowed us to avert a potential crisis when we were targeted by a phishing attack. Our encrypted data and proper backup protocols enabled us to mitigate damages effectively.
Risk Mitigation
Alongside data protection, cybersecurity measures play a critical role in risk mitigation. Just as you would install smoke detectors to guard against fire hazards, investing in cybersecurity tools helps shield your organization against cyber threats.
Consider these practices:
- Firewalls: These act as barriers between trusted internal networks and untrusted outside networks, filtering out potential threats.
- Regular Security Audits: Conducting audits helps identify vulnerabilities and gaps, enabling proactive measures to fortify your defenses.
Ultimately, the proactive adoption of cybersecurity measures empowers organizations to minimize risks and ease concerns over potential data breaches. A strike against cybersecurity can lead to hefty financial losses, legal consequences, and irreversible reputational damage—further emphasizing why these measures are not just important but essential in today’s digital landscape.

Cybersecurity Technologies and Tools
Firewalls and Intrusion Detection Systems
Having laid the groundwork on the importance of cybersecurity measures, let’s dive into the technologies and tools that are pivotal in safeguarding our digital environments. Firewalls are often the first line of defense in any security strategy. They act as barriers that filter incoming and outgoing network traffic based on predetermined security rules. Imagine a bouncer at a nightclub, only allowing trusted guests inside while keeping unwanted visitors at bay.
In addition to firewalls, Intrusion Detection Systems (IDS) enhance security by monitoring network traffic for suspicious activity. When anomalies are identified, alerts are generated for prompt investigation. Some key features include:
- Real-time monitoring: Provides instantaneous insights into suspicious activities.
- Automated alerts: Notifies security teams to react swiftly.
I recall a time when our company experienced unauthorized access attempts. Thanks to our IDS, we were alerted immediately, which allowed us to take action before any real damage occurred.
Encryption and Multi-factor Authentication
As we explore further, encryption and multi-factor authentication play crucial roles in securing sensitive information. Encryption scrambles data into an unreadable format, accessible only to those with the right decryption key. This is particularly important for financial transactions and personal information storage. Here are some practical examples of encryption benefits:
- Secure online communications: Utilizes SSL/TLS protocols to protect data during transmission.
- Data-at-rest protection: Safeguards stored data on devices and servers.
Multi-factor authentication (MFA) takes security a step further by requiring users to verify their identity through two or more verification methods before granting access. This can include:
- Something you know (password)
- Something you have (a smartphone app)
- Something you are (biometric recognition)
During a recent security upgrade, implementing MFA significantly reduced unauthorized access attempts on our platforms. Overall, the combination of these technologies forms a robust defense against the modern landscape of cyber threats, making them indispensable tools in any comprehensive cybersecurity strategy.

Role of Regulations and Compliance
GDPR and Privacy Laws
Transitioning from essential technologies, the role of regulations and compliance is critical in shaping effective cybersecurity practices. One of the most influential regulations is the General Data Protection Regulation (GDPR), which came into force in 2018. This regulation is pivotal for any organization handling the personal data of EU residents, mandating robust data protection measures.
GDPR emphasizes the rights of individuals regarding their personal data, including the right to access, rectify, and erase that data. Compliance with GDPR can be daunting, but it offers several advantages:
- Enhanced Trust: Customers are more likely to engage with businesses that prioritize data protection.
- Financial Penalties Avoidance: Non-compliance can lead to fines of up to 4% of annual global revenue.
In my own experience, aligning our practices with GDPR not only increased customer trust but also streamlined our data management processes, creating a win-win situation.
Industry-specific Compliance Standards
Beyond GDPR, many industries have their own compliance standards that must be adhered to for effective cybersecurity. For instance, the Health Insurance Portability and Accountability Act (HIPAA) governs the protection of healthcare information, while the Payment Card Industry Data Security Standard (PCI DSS) outlines security requirements for payment card transactions.
Key components include:
- Regular Audits: Ensuring continuous compliance and identification of vulnerabilities.
- Employee Training: Educating staff on specific protocols related to their roles.
These industry-specific standards not only help organizations maintain regulatory compliance but also cultivate a culture of security awareness. In one example, a healthcare provider I worked with improved its security posture after undergoing a thorough HIPAA compliance audit, significantly reducing data breaches. Ultimately, embracing these regulations and standards is vital for organizations aiming to enhance their cybersecurity framework while protecting their stakeholders.

Cybersecurity in Business Operations
Safeguarding Online Transactions
Building on the discussion around regulations and compliance, it’s essential to examine how cybersecurity is woven into the fabric of business operations, particularly in safeguarding online transactions. In an age where e-commerce is booming, ensuring secure online transactions is not just a best practice; it’s a necessity.
When businesses accept payments online, they must implement robust security measures to protect customer data. Essential strategies include:
- Secure Sockets Layer (SSL) Certificates: These encrypt data during transmission, ensuring that sensitive information like credit card details remains private.
- Regular Security Audits: Performing audits on payment systems helps identify vulnerabilities that could be exploited by cybercriminals.
I recall a time when my startup faced potential payment fraud, but thanks to our implementation of SSL certificates, customer data remained secure. This incident underscored the importance of prioritizing secure online transactions to maintain customer trust.
Securing Sensitive Information
Beyond transaction security, the safeguarding of sensitive information is critical for day-to-day operations. Businesses frequently handle confidential data—be it employee records, intellectual property, or client information—and any breach can have catastrophic consequences.
Key practices to secure sensitive data include:
- Access Controls: Limiting access to sensitive data to only those who need it can significantly reduce exposure.
- Data Encryption: Encrypting stored data protects it from being accessed if unauthorized individuals gain entry to systems.
When our company adopted access control measures, we noticed a marked decline in data access incidents. The combination of securing online transactions and sensitive information is vital for building a resilient business. Organizations that prioritize these aspects empower themselves to thrive in a competitive landscape while ensuring customer confidence and compliance with regulations.
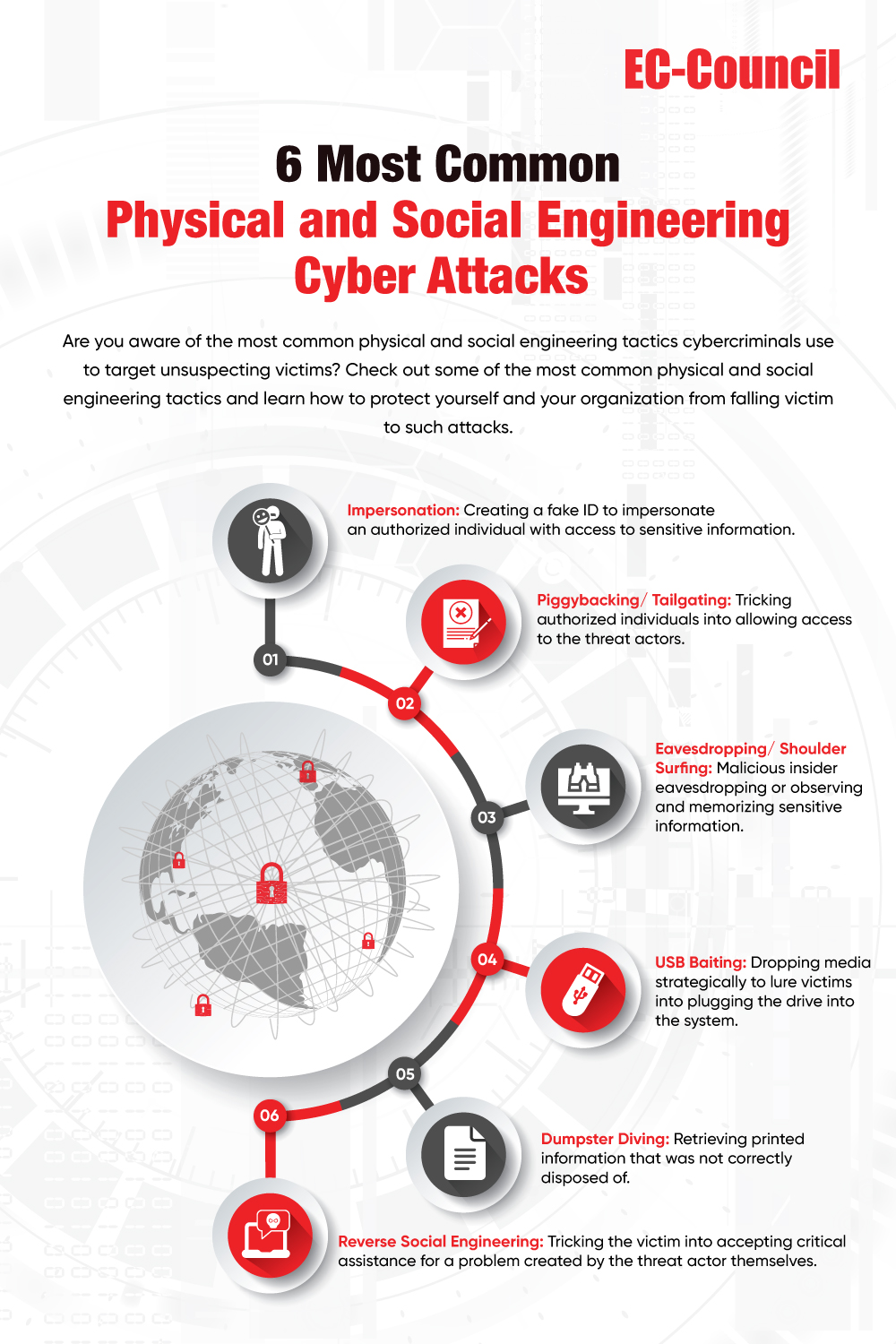
Cybersecurity Awareness and Training
Employee Education Programs
As we continue to explore the integral components of cybersecurity in business operations, it’s crucial to highlight the importance of cybersecurity awareness and training. Employee education programs play a central role in creating a security-conscious workplace culture. After all, the majority of security breaches stem from human error!
Implementing effective training programs can ensure employees recognize and respond to potential threats. Key elements of these programs include:
- Phishing Awareness: Teaching employees how to identify suspicious emails can drastically reduce the risk of account compromise.
- Secure Password Practices: Emphasizing the creation of strong passwords and the importance of regularly updating them can deter many unauthorized access attempts.
In one instance, our organization conducted a phishing simulation to gauge employee awareness. The results were eye-opening; many unsuspecting individuals clicked on fake links. Following the training, though, we noted a significant reduction in click rates during actual phishing attempts.
Cybersecurity Incident Response Plans
Alongside ongoing education, having a well-defined cybersecurity incident response plan is vital. Such plans detail the steps an organization should take in the event of a cyber incident, ensuring a swift and structured approach to mitigating damage.
Key components of an effective incident response plan include:
- Identification: Quickly recognizing whether an incident is occurring.
- Containment: Taking immediate action to limit further damage.
- Communication: Keeping stakeholders informed and managing public relations.
When our company faced a potential breach, having a pre-established incident response plan allowed us to act quickly, minimizing the impact while bolstering our reputation. Cybersecurity isn’t just about technology—it’s also about empowering employees and having a robust response strategy. By investing in awareness training and structured response plans, organizations can fortify their defenses and navigate the increasingly complex cyber landscape with confidence.

Future Trends in Cybersecurity
Artificial Intelligence in Cyber Defense
Continuing from the significance of employee education and incident response plans, it’s fascinating to explore future trends in cybersecurity that are reshaping the landscape. One area gaining tremendous traction is the use of Artificial Intelligence (AI) in cyber defense. AI technologies are transforming how organizations detect and respond to cyber threats.
AI can enhance security in several ways:
- Real-time Monitoring: AI algorithms analyze vast amounts of data to identify unusual patterns indicative of potential cyber threats.
- Automated Responses: AI can initiate predefined actions when an anomaly is detected, significantly reducing response times.
I remember attending a cybersecurity conference where a speaker highlighted a case where AI identified a phishing attack in real-time, saving an organization from substantial data loss. The rapid advancements in AI show its potential to act as a formidable ally in the fight against cybercrime.
IoT Security Challenges
On the other hand, as technologies advance, the rise of the Internet of Things (IoT) introduces new challenges. IoT devices are often less secure and can serve as easy entry points for cybercriminals.
Here are some pressing IoT security challenges:
- Lack of Standardization: Many IoT devices do not adhere to comprehensive security protocols, creating vulnerabilities.
- Data Privacy: With numerous devices collecting personal data, ensuring that this information is stored and transmitted securely becomes increasingly complex.
A recent experience with smart home devices highlighted this issue: a well-known security flaw was discovered in popular IoT gadgets, reminding us all that convenience often comes at the cost of security. As we look ahead, organizations must prioritize addressing these challenges while leveraging advancements like AI to enhance their cybersecurity frameworks. The future undoubtedly holds a myriad of challenges and opportunities that will shape our approach to protecting digital assets.

Conclusion
Recap of Cybersecurity Importance
Wrapping up our exploration of essential cybersecurity practices, it’s important to emphasize just how critical cybersecurity is in today’s digital age. From safeguarding sensitive data and online transactions to fostering a culture of awareness within organizations, effective cybersecurity is not just a checkbox—it’s a fundamental component of operational integrity.
Every business, regardless of size, faces unique challenges, yet the need for solid cybersecurity measures remains universal:
- Enhancing Customer Trust: Demonstrating strong cybersecurity practices can set your business apart.
- Protecting Against Financial Loss: The cost of a breach often exceeds the investments made in prevention.
- Compliance with Regulations: Adhering to laws like GDPR not only avoids fines but strengthens customer relationships.
Call to Action for Strengthening Cyber Defenses
Now, more than ever, it’s imperative for organizations to take proactive steps in strengthening their cyber defenses. This includes:
- Investing in Training: Equip employees with the knowledge they need to recognize potential threats.
- Implementing Robust Technologies: Utilize advanced cybersecurity solutions such as AI and encryption.
- Regularly Reviewing Security Protocols: Make audits and assessments a consistent practice.
A personal anecdote from a previous role emphasizes this: after significant investments in training and technology upgrades, our organization experienced a marked decline in security incidents. The steps taken today can make all the difference tomorrow. Embracing a proactive stance toward cybersecurity will enable organizations to navigate the complexities of the digital landscape confidently and resiliently. Let’s take action now for a safer digital future!

