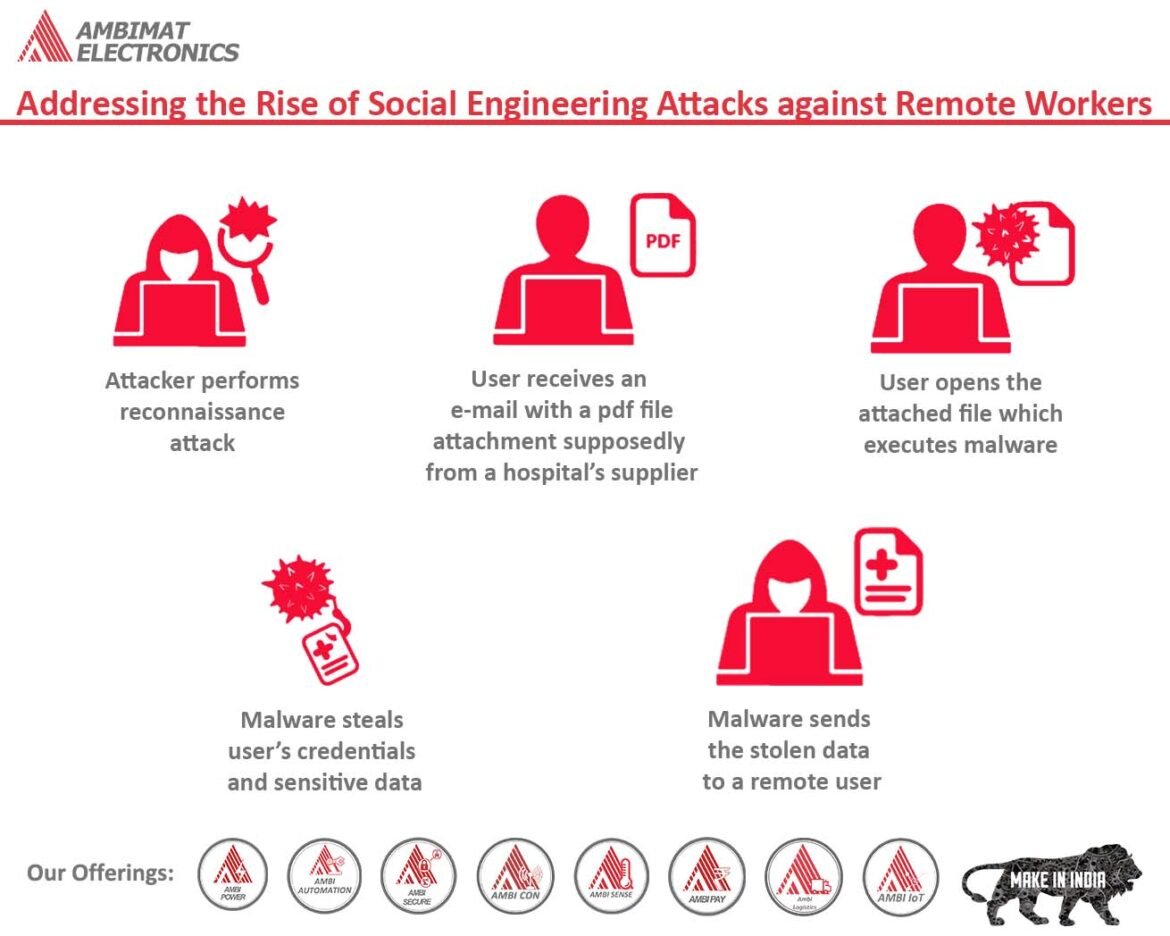
Introduction
Understanding Social Engineering Attacks
In today’s fast-paced digital world, social engineering attacks have emerged as a prominent threat, exploiting human psychology rather than technical vulnerabilities. These attacks manipulate individuals into divulging confidential information, such as passwords, financial data, or sensitive company secrets. Rather than relying on brute-force methods, attackers deceive their targets through various tactics, including impersonation, misinformation, and emotional manipulation.
Consider this: a simple email that appears to be from your company’s IT department, asking for password verification, could lead to devastating consequences if clicked without a second thought. These scenarios unfold daily, affecting businesses of all sizes.
Overview of Business Vulnerabilities to Social Engineering
Businesses face significant vulnerabilities to social engineering because:
- Employees are often the weakest link; even the most secure systems can falter when human error occurs.
- Organizations frequently overlook the importance of training, thereby leaving staff unprepared to recognize and respond to social engineering attempts.
- The rapid evolution of technology means that even traditional methods of safeguarding information can become obsolete.
Understanding these vulnerabilities is key to fortifying defenses against these cunning attacks.

Types of Social Engineering Attacks
Phishing Attacks
Phishing attacks are among the most common types of social engineering attacks, designed to trick individuals into revealing personal information. Attackers often use forged emails or fake websites that mimic legitimate ones. Picture receiving an email that looks just like it came from your bank but has a slight misspelling in the address. This could lead you to believe it’s real and accidentally provide your login credentials.
Pretexting
Pretexting involves creating a fabricated scenario to obtain information. For instance, an attacker might impersonate a co-worker and claim they need help with a project. By establishing a false narrative, they can coax sensitive information from unsuspecting employees.
- Characteristics of Pretexting:
- Use of fake identities
- Engaging in conversation to build rapport
- Crafting plausible stories
Baiting
Baiting is another insidious tactic, where attackers entice victims by offering something appealing, like free software or downloads. An employee might inadvertently install malware by clicking on a seemingly harmless link.
- Common baiting techniques:
- USB drives left in public places
- Attractive offers in unsolicited emails
Understanding these attack types is crucial for businesses to create stronger defenses against the vulnerabilities they present.

Impact of Social Engineering Attacks on Businesses
Financial Losses
The financial implications of social engineering attacks can be staggering. Businesses may directly lose money through fraud, or they might face indirect costs due to recovery efforts. Imagine a company that falls victim to a phishing scheme—transferring funds to an impersonated vendor might lead to a hefty loss that could cripple smaller organizations.
- Key financial impacts:
- Immediate fraud losses
- Investigation and recovery costs
- Increased insurance premiums
Reputational Damage
Beyond the financial aspects, the reputational damage can be long-lasting. Clients and customers expect their sensitive information to be protected. If a business suffers a social engineering attack, trust erodes quickly. For example, if a tech company is breached, their customers may reconsider their loyalty, leading to a loss of future business.
- Consequences of reputational harm:
- Loss of customer trust
- Decline in market share
- Difficulty attracting new clients
Legal Consequences
The legal implications of social engineering attacks are another critical aspect for businesses to consider. Many organizations are bound by regulations safeguarding data privacy. If a breach occurs, they may face lawsuits or hefty fines. The fallout can be extensive, involving compliance audits and stricter regulatory oversight.
Addressing these impacts is vital for any business aiming to mitigate the repercussions of social engineering attacks effectively.
Common Tactics Used in Social Engineering Attacks
Manipulation of Trust
One of the core tactics used in social engineering attacks is the manipulation of trust. Attackers often leverage relationships and authority to bypass normal security measures. Imagine receiving a call from someone who introduces themselves as an IT administrator. They might sound genuine and authoritative, convincing the employee to share sensitive information under the guise of a routine check. This tactic preys on the innate tendency to trust those in positions of authority.
- Examples of trust manipulation:
- Impersonation of trusted figures
- Using official-looking communication
- Creating a sense of urgency to prompt quick action
Exploitation of Human Psychology
Exploitation of human psychology is another crucial aspect of social engineering tactics. Attackers understand emotional triggers and often use them to their advantage. For example, they may evoke fear by threatening account suspension if immediate action is not taken. This emotional manipulation can cloud judgment and lead people to act without careful consideration.
- Psychological tactics include:
- Fear-based messaging
- Appeals to curiosity (e.g., “Click to see your bonus!”)
- Reciprocity, where attackers offer something small to elicit a bigger favor
Recognizing these tactics is vital for everyone, as it forms the cornerstone of effective defenses against social engineering attacks.

Case Studies: Real-Life Examples of Social Engineering Attacks
Attack on Tech Company X
One notable case involved Tech Company X, which fell victim to a sophisticated phishing scheme. Employees received an email that appeared to come from their managing director, requesting urgent updates to internal software. Trusting the seemingly legitimate communication, several employees clicked on the provided link and entered their credentials.
- Key takeaways:
- Result: Compromised sensitive data and unauthorized access to internal systems.
- Impact: Financial losses included recovery costs and regulatory fines.
This attack serves as a reminder of the importance of verification, even when communication appears to be from a trusted source.
Breach at Financial Institution Y
In another striking example, Financial Institution Y experienced a massive breach initiated by a pretexting scheme. An attacker posed as a vendor, craftily building rapport with the customer service team over several weeks. Eventually, the attacker requested updates to client information, which led to unauthorized access to accounts.
- Outcomes:
- Result: Loss of customer finances and personal information.
- Impact: A significant erosion of trust among clients, leading to lost business.
These case studies illustrate how critical vigilance and robust training are in preventing social engineering attacks in any organization. Understanding the tactics used can empower businesses to strengthen their defenses.

Prevention and Mitigation Strategies
Employee Training and Awareness Programs
One of the most effective strategies for preventing social engineering attacks is through comprehensive employee training and awareness programs. Regular training fosters an environment of vigilance, equipping staff with the skills to identify and respond to potential threats.
Consider implementing interactive training sessions, where employees analyze real-world phishing emails and practice recognizing red flags. For example, a scenario-based training session could involve role-playing, allowing employees to experience firsthand the tactics used by attackers.
- Key components of effective training include:
- Understanding common social engineering techniques
- Recognizing the signs of phishing and other scams
- Encouraging employees to report suspicious activities
Implementation of Multi-Factor Authentication
In addition to training, the implementation of multi-factor authentication (MFA) significantly enhances security. By requiring multiple forms of verification, such as a password and a temporary code sent to a personal device, businesses can create an additional barrier against unauthorized access.
- Benefits of MFA:
- Reduces the risk of credential theft
- Limits exposure even if passwords are compromised
- Provides peace of mind to employees and customers alike
Together, these strategies form a robust defense against social engineering, making it harder for attackers to succeed in their endeavors. By investing in training and advanced security measures, businesses can significantly mitigate risks.

Regulatory Framework and Compliance Requirements
GDPR and Data Protection
As social engineering attacks rise, regulatory frameworks like the General Data Protection Regulation (GDPR) play a crucial role in dictating how organizations manage sensitive information. For businesses operating within or dealing with EU citizens, GDPR compliance isn’t just a best practice—it’s a legal obligation.
This regulation mandates stringent data protection measures, compelling companies to ensure the privacy and security of personal data. Under the GDPR, organizations must demonstrate transparency about data handling practices and report breaches promptly.
- Key GDPR provisions include:
- Right to access personal data
- Obligation to report data breaches within 72 hours
- Requirement for clear consent mechanisms
Industry-Specific Regulations
In addition to GDPR, various industries have their own compliance requirements that address social engineering risks. For instance, healthcare organizations must adhere to HIPAA regulations, which stipulate strict guidelines for the protection of patient information.
- Examples of industry-specific regulations:
- PCI DSS for payment card data security
- FINRA for financial institutions
- SOX for publicly traded companies
Understanding and adhering to these regulations can significantly enhance an organization’s defenses against social engineering attacks, ultimately fostering a culture of security and trust. By staying compliant, businesses not only protect themselves from legal repercussions but also reinforce their commitment to safeguarding sensitive information.
The Future of Social Engineering Attacks
Emerging Trends
As businesses evolve and technology advances, so too do the techniques employed by social engineers. Emerging trends indicate that attackers are becoming increasingly sophisticated, exploiting current events and societal shifts to manipulate their targets. For instance, during global crises like the COVID-19 pandemic, many phishing attacks were crafted around health and safety themes, preying on individuals’ fears and uncertainties.
- Notable emerging trends include:
- Exploitation of remote work environments to gain access
- Increased use of social media to gather personal information
- Targeting employees during high-stress periods, such as layoffs or mergers
Technological Advancements in Attack Techniques
Technological advancements have also given rise to more complex social engineering attacks. With tools that can simulate realistic voice calls or deepfake technology, attackers can create highly convincing scenarios that blur the lines between reality and deception.
- Examples of these advancements:
- AI-driven chatbots that impersonate customer service representatives
- Deepfake videos that can mislead individuals into providing sensitive information
- Automation tools that enable simultaneous phishing campaigns
As these trends and technologies develop, businesses must stay vigilant and adapt their security strategies. Recognizing the evolving landscape of social engineering will be crucial for effectively defending against these increasingly sophisticated attacks in the future.