Overview of Cyber Attacks
Defining Cyber Attacks
In today’s digitized world, a cyber attack refers to any malicious activity aimed at damaging, disrupting, or gaining unauthorized access to computer systems, networks, or devices. These attacks can range from simple hacks by juvenile enthusiasts to sophisticated operations backed by organized crime or even nation-states.
Imagine waking up to find that your company’s sensitive data has been compromised overnight and your website is down due to a persistent attack. This scenario is increasingly common, and it underscores the importance of understanding what cyber attacks are and the motives behind them.
Common Objectives of Cyber Attacks
Understanding the objectives of cyber attacks can help individuals and organizations better prepare for and defend against them. Here are some prevalent motives:
- Financial Gain: Many attacks seek direct profit through theft of personal or financial information, ransomware, or selling stolen data on the dark web.
- Data Theft: Intellectual property or sensitive corporate data is a goldmine for competitors and criminal entities alike.
- Disruption of Services: Some attacks aim to incapacitate organizations, causing downtime that leads to a loss of trust and productivity. Think of large-scale Distributed Denial of Service (DDoS) attacks that can incapacitate service providers.
- Political or Social Motives: Cyber attacks can also be politically charged, intended to cause harm to a nation’s infrastructure or to promote social agendas.
- Revenge or Personal Vendettas: Sometimes, disgruntled employees or ex-partners target organizations to settle scores.
By recognizing these objectives, organizations can adopt a more proactive approach to cybersecurity, as can be further explored in the detailed sections of this discussion. The journey to understanding the anatomy of a cyber attack is crucial in this era of increasing technological vulnerability.

Types of Cyber Attacks
Malware Attacks
Malware, short for malicious software, is one of the most insidious types of cyber attacks. It encompasses a wide range of harmful software designed to disrupt, damage, or gain unauthorized access to systems. Examples include viruses, worms, Trojan horses, and ransomware.
A personal experience comes to mind: when a friend’s computer fell victim to ransomware, their data was effectively held hostage until a ransom was paid. Thankfully, they had backups, but not everyone’s story ends so positively. Here’s a quick look at some common types of malware:
- Viruses: These self-replicating programs attach themselves to clean files and spread throughout a computer system.
- Worms: Unlike viruses, worms can spread without human interaction, exploiting vulnerabilities to access networks.
- Spyware: This discreetly monitors user activity, often collecting sensitive information without consent.
Phishing Attacks
Phishing is the art of deception, mainly carried out through emails or messages designed to trick individuals into revealing sensitive information. Imagine receiving a seemingly authentic email from your bank, prompting you to “verify your account.” It’s unsettling how easily one could fall for such a trap.
Here’s how phishing typically works:
- An attacker creates a fake website resembling a legitimate one.
- The victim receives a message with a link to this site, often creating a sense of urgency.
- Upon login, the attacker collects the victim’s credentials.
DDoS Attacks
Distributed Denial of Service (DDoS) attacks flood a target’s server with traffic, rendering it incapable of responding to legitimate requests. This is not just an annoyance—it can cripple businesses, as seen in the case of a local gaming company that went offline for hours due to such an attack during peak hours.
DDoS attacks can be categorized as follows:
- Volumetric Attacks: Overload the bandwidth with excessive traffic.
- Protocol Attacks: Target server resources, exploiting weaknesses enabling a larger traffic generation.
- Application Layer Attacks: Focus on specific applications to crash or slow down services.
As organizations face these evolving threats, understanding the types of cyber attacks can help in building robust defenses against them. The battle against cyber threats is ongoing, and being informed is the first line of defense.
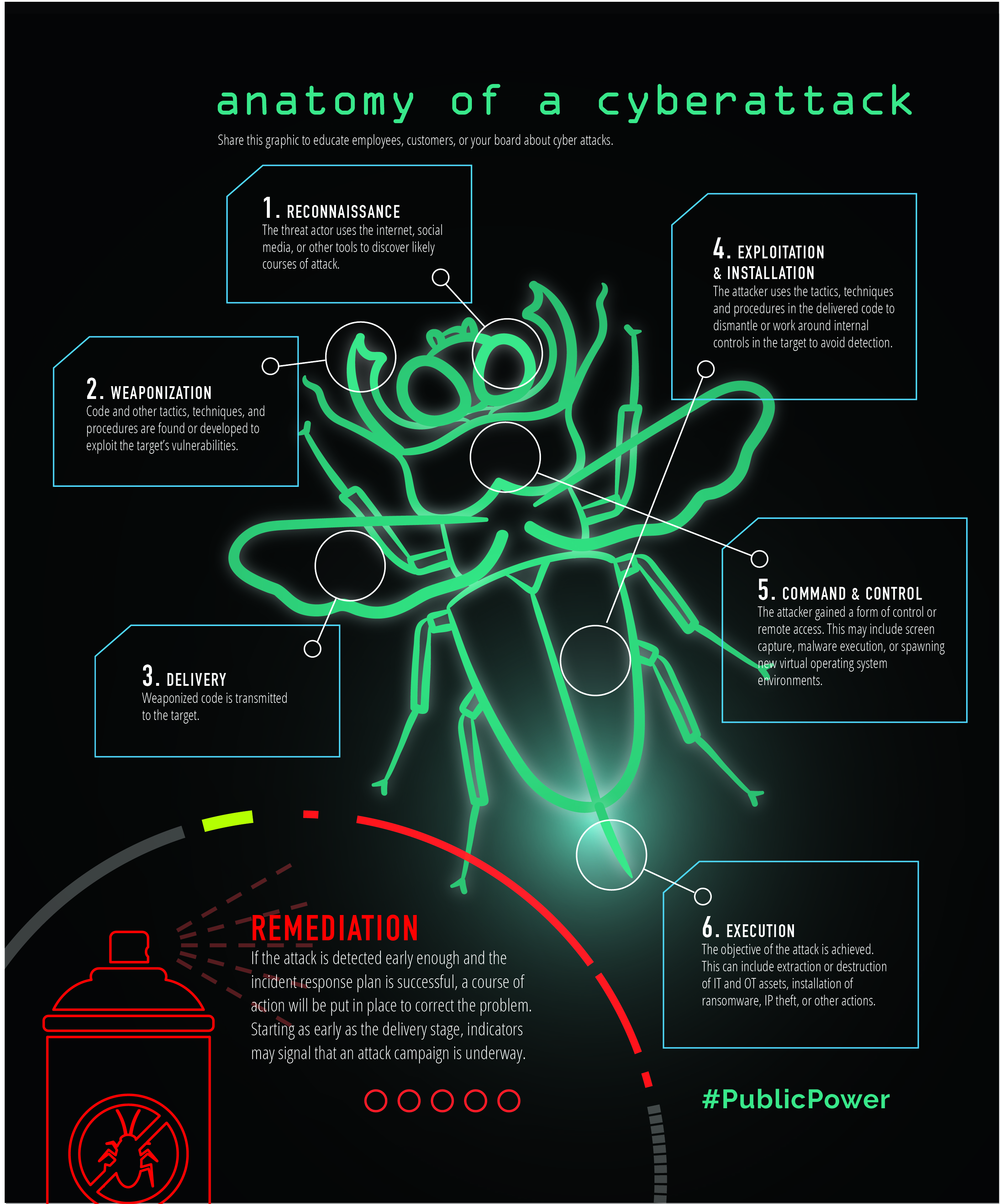
Stages of a Cyber Attack
Understanding the stages of a cyber attack is crucial for organizations to protect themselves effectively. Cyber attacks typically unfold in a series of phases, each building on the last. Let’s delve into these stages to get a clearer picture.
Reconnaissance
The first stage of any cyber attack is reconnaissance, where attackers gather intelligence about their target. This could involve browsing websites, using social media to acquire information, or employing tools to scan the network for vulnerabilities.
For instance, think about how one might casually observe a rival’s tactics in a sports game. Attackers utilize similar strategies to learn about potential weaknesses.
Intrusion
Once enough information has been collected, the next phase is intrusion. Here, attackers gain unauthorized access to the network. This can occur through various means such as exploiting weak passwords or using social engineering techniques to trick an employee into granting access.
Imagine a scenario where an unsuspecting employee clicks on a malicious link, unwittingly granting entry to a hacker.
Exploitation
After breaking into the system, attackers move on to exploitation. At this point, they leverage the access gained to extract sensitive information or deploy malware.
- Data Theft: Sensitive data such as customer information or financial records could be stolen.
- Ransomware Deployment: A common tactic where files are encrypted, and a ransom is demanded for their release.
Elevation of Privileges
In this stage, attackers seek to gain higher access privileges, allowing them to navigate deeper into the network undetected. By exploiting existing user accounts or vulnerabilities, they can control systems that hold valuable data.
Obfuscation
Finally, attackers often engage in obfuscation. This involves hiding their tracks to avoid detection. They might erase logs or deploy tactics that make their actions appear benign. Just like a magician distracts an audience while performing a trick, hackers are skilled at disguising their malicious activities.
By recognizing these stages of a cyber attack, organizations can enhance their defenses and response strategies, ultimately reducing the chances of falling victim to these escalating threats. The evolving landscape of cyber threats highlights the importance of vigilance and preparedness in safeguarding sensitive data.
Vulnerabilities Exploited in Cyber Attacks
As we delve deeper into the anatomy of a cyber attack, it’s essential to understand the vulnerabilities that attackers exploit. These vulnerabilities become the gateways through which malicious actors infiltrate systems and networks. Let’s explore three primary categories: software vulnerabilities, human factor vulnerabilities, and network vulnerabilities.
Software Vulnerabilities
Software vulnerabilities are flaws or weaknesses in applications that can be manipulated by attackers. These vulnerabilities often stem from:
- Unpatched Software: Failing to regularly update software can leave systems exposed to known exploits.
- Flawed Code: Poorly written code may present loopholes that hackers can leverage.
A notable example is the Equifax data breach in 2017, where an unpatched software vulnerability allowed hackers to access personal information of millions. This incident highlights the critical need for timely software updates and thorough testing.
Human Factor Vulnerabilities
While technology plays a significant role in security, human behavior is frequently the soft underbelly of cybersecurity. Human factor vulnerabilities include:
- Social Engineering: Attackers often exploit human psychology to trick individuals into providing sensitive information. A classic example is pretexting, where an attacker poses as a trusted figure to extract information.
- Negligence: Employees might neglect basic security protocols, such as using weak passwords or leaving their screens unattended.
For instance, companies that invest in cybersecurity training witness significantly reduced incidents of social engineering scams.
Network Vulnerabilities
Network vulnerabilities arise from misconfigurations or weaknesses in network design that can be exploited by cybercriminals. Key issues include:
- Weak Firewall Configurations: Firewalls that are improperly configured may allow unauthorized access.
- Unsecured Wi-Fi Networks: Open networks provide easy access points for attackers.
A real-world scenario involved a coffee shop with an unsecured Wi-Fi network, where customers were using their devices to access sensitive information. Attackers were able to intercept data traffic, leading to identity theft for some unsuspecting patrons.
By recognizing and addressing these vulnerabilities—software, human, and network—organizations can bolster their defenses against cyber attacks. Understanding these potential weak points is vital in building a resilient cybersecurity framework that protects against evolving threats.
Impact of Cyber Attacks
Having explored the vulnerabilities exploited in cyber attacks, it’s imperative to understand their far-reaching impacts. Cyber attacks can wreak havoc on organizations, influencing various aspects of their operations, from finances to reputation. Let’s dive into three significant consequences: financial losses, reputational damage, and legal and compliance ramifications.
Financial Losses
Financial losses are often the first and most apparent consequence of a cyber attack. These can stem from:
- Direct Theft: In cases of ransomware or direct hacking, funds can be stolen from accounts or held for ransom.
- Downtime Costs: When systems are compromised, the resulting downtime can severely impact revenue streams. A well-known example is the 2017 WannaCry ransomware attack, which caused billions in losses across industries globally.
- Recovery Expenses: Organizations may incur substantial costs to restore systems, conduct forensic investigations, and bolster security post-attack.
In fact, studies suggest that the average cost of a data breach can exceed millions, making it critical for organizations to prioritize cybersecurity.
Reputational Damage
The reputational damage following a cyber attack can linger long after the incident is resolved. Customers and partners may lose trust, leading to:
- Customer Attrition: Clients may reconsider their associations with affected companies, choosing competitors perceived as safer.
- Negative Press: Bad publicity can amplify the damage, as news spreads about the attack. For instance, companies like Target and Yahoo experienced significant public relations challenges in the wake of their breaches.
Rebuilding a tarnished reputation takes time and effort, and many organizations find it challenging to regain lost consumer confidence.
Legal and Compliance Ramifications
Moreover, organizations must grapple with legal and compliance ramifications post-attack. They could face:
- Fines and Penalties: Regulatory bodies may impose fines for failing to protect consumer data adequately. For instance, the General Data Protection Regulation (GDPR) introduced hefty fines for data breaches in the EU.
- Litigations: Affected individuals or entities may file lawsuits against organizations, seeking damages for negligence.
In summary, the impact of cyber attacks extends far beyond immediate damages, encompassing financial strain, reputational fallout, and legal challenges. Organizations must remain vigilant and proactive in their cybersecurity efforts to mitigate these potential consequences and ensure long-term success. The stakes in the realm of cyber safety are high, serving as a pressing reminder to prioritize security protocols.

Cyber Attack Prevention and Mitigation
With the profound impacts that cyber attacks can have on organizations, it becomes critical to focus on prevention and mitigation strategies. By adopting robust cybersecurity measures, businesses can significantly reduce their vulnerability and enhance their resilience. Let’s look at three key areas to prioritize: implementing strong security measures, conducting regular security audits, and training employees on cybersecurity best practices.
Implementing Strong Security Measures
One of the foundational pillars of cyber attack prevention is deploying strong security measures. This involves:
- Firewalls and Intrusion Detection Systems: Establishing firewalls helps block unauthorized access, while intrusion detection systems alert administrators about potential threats.
- Data Encryption: Encrypting sensitive information ensures that even if data is intercepted, it remains unintelligible to cybercriminals.
- Multi-Factor Authentication (MFA): Adding an extra layer of security, MFA requires users to provide two or more verification factors to access systems, significantly reducing the risk of unauthorized access.
When a local bank implemented MFA, they reported a noticeable decline in attempted data breaches—an effective testament to proactive measures.
Conducting Regular Security Audits
Regular security audits are crucial in identifying potential vulnerabilities before they can be exploited. These audits should include:
- Penetration Testing: Simulating attacks on the network helps identify weaknesses.
- Vulnerability Assessments: Regular evaluations of software and hardware security are essential to ensure strong defenses are maintained.
For example, companies that perform bi-annual security audits not only discover and fix flaws but also build a culture of continual improvement in cybersecurity.
Training Employees on Cybersecurity Best Practices
Finally, employees play a pivotal role in maintaining robust cybersecurity. Comprehensive training on best practices is essential. Key topics should include:
- Phishing Awareness: Educating employees on identifying phishing attempts can prevent potential breaches.
- Password Security: Reinforcing the importance of strong password usage and management can safeguard sensitive information.
- Reporting Suspicious Activity: Encouraging prompt reporting of unusual incidents creates a proactive atmosphere.
A former colleague once recounted how an informal lunch-and-learn session significantly raised awareness among her team, helping them spot phishing emails that had nearly compromised sensitive company data.
By focusing on these critical areas—strong security measures, regular audits, and employee training—organizations can fortify their defenses against cyber threats, protecting their assets and reputation. In a world where cyber threats are ever-evolving, these proactive strategies are essential for navigating the challenges of the digital landscape.

