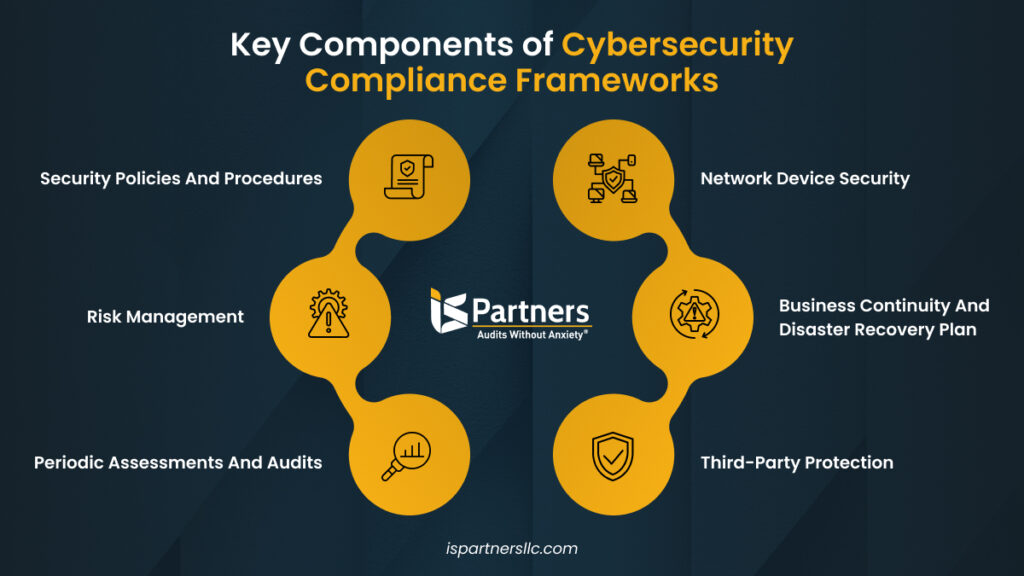
Overview of Cybersecurity Compliance
Definition of Cybersecurity Compliance
Cybersecurity compliance refers to the adherence to laws, regulations, and guidelines designed to protect sensitive information from cyber threats. Organizations must implement specific measures and controls to safeguard data, while ensuring that their practices align with established standards set forth by governing bodies.
For instance, companies handling personal or financial information often need to comply with regulations like GDPR or PCI DSS. The essence of compliance is not just to avoid penalties but to foster a culture of security and accountability throughout the organization.
Importance of Cybersecurity Compliance
The significance of cybersecurity compliance cannot be overstated, especially in today’s digital landscape. Here are a few reasons highlighting its importance:
- Data Protection: Compliance ensures that sensitive data is protected from breaches, safeguarding both the organization and its clients.
- Reputation Management: A compliant organization earns trust, enhancing its reputation in the market.
- Cost-Effectiveness: Preventing data breaches through compliance can save significant remediation costs later on.
Ultimately, navigating cybersecurity compliance is crucial not only for legal reasons but also for fostering a secure environment where businesses can thrive. Organizations that prioritize compliance are better positioned to face the evolving cyber threat landscape effectively.
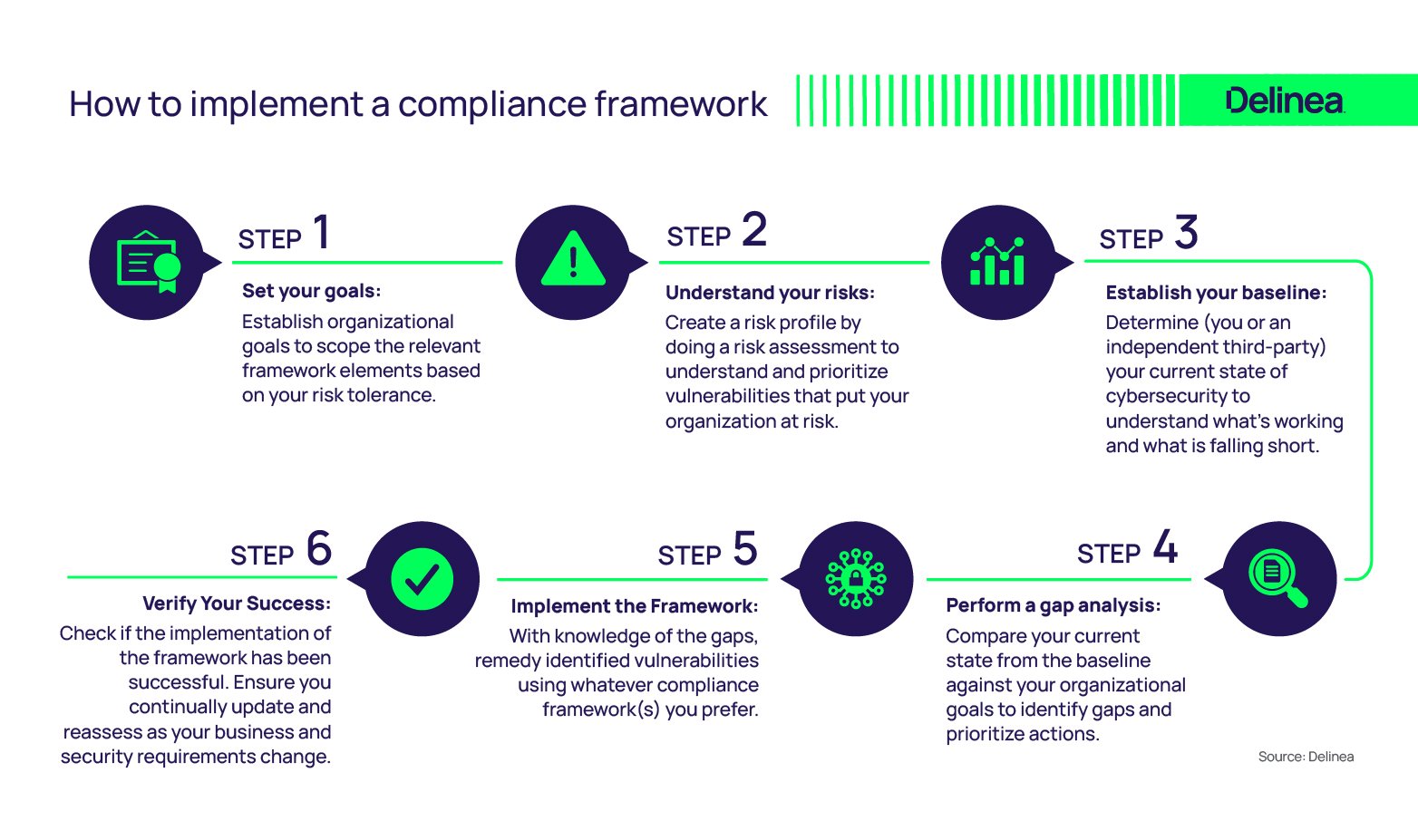
Regulatory Frameworks in Cybersecurity Compliance
General Data Protection Regulation (GDPR)
The General Data Protection Regulation (GDPR) is a cornerstone of data protection law in the European Union. Implemented in 2018, it aims to give individuals control over their personal data while holding organizations accountable for data privacy. Companies must ensure:
- Transparency: Clear communication with customers about how their data is used.
- Consent: Obtaining explicit permission before collecting personal data.
- Rights of Individuals: Allowing users to access, rectify, and erase their personal data.
Navigating GDPR may feel overwhelming, but the focus on respect for individual rights promotes trust and enhances customer relationships.
Health Insurance Portability and Accountability Act (HIPAA)
In the healthcare sector, HIPAA plays a vital role in protecting health information. Organizations must adopt rigorous security measures for safeguarding patient data, such as:
- Privacy Rule Compliance: Ensuring patient information is kept confidential.
- Security Standards: Implementing safeguards to ensure electronic storage and transmission security.
By adhering to HIPAA, healthcare providers not only avoid hefty penalties but also enhance patient confidence.
Payment Card Industry Data Security Standard (PCI DSS)
For businesses handling credit card transactions, PCI DSS serves as a critical framework. It sets requirements to safeguard cardholder data, including:
- Encryption: Protecting card information during transmission.
- Regular Security Testing: Conducting assessments to identify vulnerabilities.
Compliance with PCI DSS is essential for building trust with customers and mitigating fraud risks. Together, these regulatory frameworks offer a comprehensive approach to navigating cybersecurity compliance, ensuring organizations are well-equipped to protect sensitive data.

Common Challenges in Achieving Cybersecurity Compliance
Lack of Resources
One of the most significant hurdles organizations face in achieving cybersecurity compliance is the lack of resources. Many businesses, especially small to medium-sized ones, often operate with constrained budgets and limited personnel. This shortage can lead to:
- Inadequate Training: Staff may not receive the proper training needed to understand compliance requirements.
- Outdated Technology: Failing to invest in the latest security tools can expose organizations to vulnerabilities.
- Insufficient Analysis: Without enough personnel, conducting thorough risk assessments can become challenging.
Anecdotally, many organizations share that despite their commitment to compliance, the struggle often stems from simply not having enough bandwidth to meet regulatory demands effectively.
Rapidly Evolving Threat Landscape
Another pressing challenge is the constantly evolving threat landscape. Cybercriminals continuously adapt their techniques, which can outpace compliance measures. This situation can lead to:
- Emerging Threats: New types of malware or phishing schemes can emerge, making previously established security protocols obsolete.
- Compliance Fatigue: Organizations may become overwhelmed by the frequency of updates and feel unsure about which guidelines to prioritize.
To successfully navigate these challenges, organizations must regularly review their compliance strategies and remain agile in adapting to change. By proactively addressing these issues, organizations can create a more resilient cybersecurity posture.
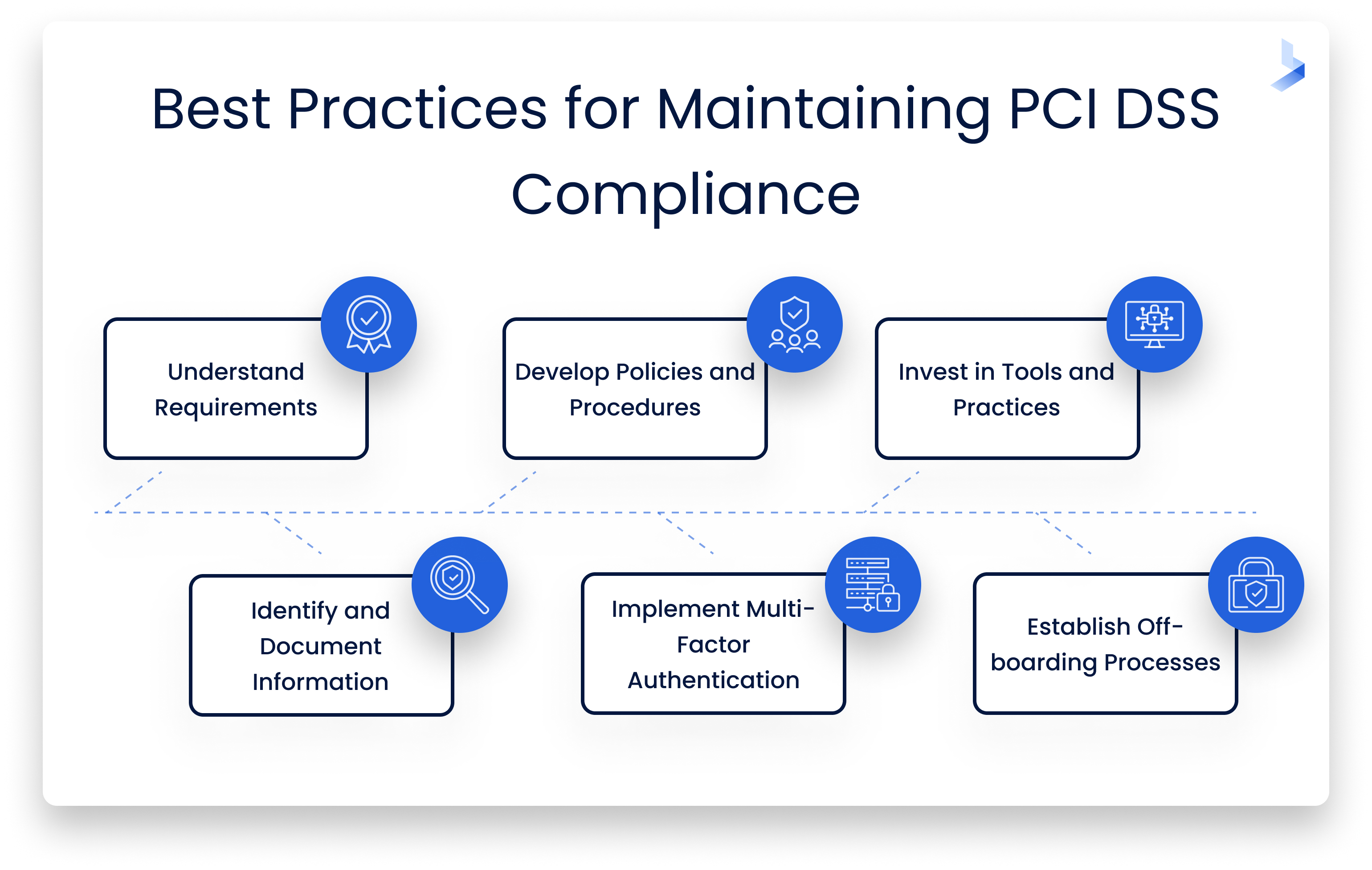
Strategies for Effective Cybersecurity Compliance
Conducting Risk Assessments
To effectively navigate cybersecurity compliance, organizations must start with thorough risk assessments. This process involves identifying potential vulnerabilities, evaluating threats, and measuring the potential impact on the organization. Here are some key steps:
- Identify Data Assets: Determine what sensitive information needs protection.
- Assess Threats: Consider various risk factors, such as insider threats and external cyber-attacks.
- Evaluate Processes: Analyze current policies and procedures to identify weaknesses.
Regular risk assessments help organizations prioritize resources and allocate efforts where they matter most.
Implementing Security Controls
Once risks are identified, it’s time to implement appropriate security controls. This can involve a mix of technology and processes, including:
- Access Controls: Limiting access to sensitive data based on roles.
- Encryption: Securing data in transit and at rest.
- Multi-Factor Authentication (MFA): Adding an extra layer of security for user accounts.
These measures not only help meet compliance requirements but also enhance the organization’s overall security posture.
Employee Training and Awareness Programs
Investing in employee training and awareness programs is crucial. Humans are often the weakest link in cybersecurity. To foster a culture of security, organizations should:
- Regular Training Sessions: Equip employees with knowledge about compliance regulations and security best practices.
- Phishing Simulations: Conduct tests to help employees recognize malicious communications.
By arming staff with the necessary tools and knowledge, organizations can significantly reduce their vulnerability while reinforcing their commitment to compliance in an environment that values security.

Compliance Audits and Assessments
Understanding Compliance Audits
Compliance audits play a vital role in ensuring that organizations adhere to established cybersecurity regulations. These audits involve systematic evaluations of an organization’s policies, procedures, and controls to determine compliance with relevant laws and standards. During audits, evaluators typically examine:
- Documentation: Policies and procedures to ensure they are up-to-date and effective.
- Implementation: Actual security measures in place and their effectiveness.
- Interviews: Engaging with staff to assess their understanding of compliance protocols.
The outcome of these audits can significantly impact an organization’s ability to maintain certification and avoid penalties.
Tips for Successful Compliance Assessments
To ensure a successful compliance assessment, organizations can adopt several best practices:
- Prepare Documentation Ahead: Maintain organized records of policies, training, and incident response.
- Involve Key Stakeholders: Engage various departments, including IT and legal, to build a robust compliance framework.
- Conduct Internal Audits: Regularly assess your own processes to identify gaps before the official audit.
By proactively addressing these aspects, organizations not only improve their compliance posture but also foster a culture of continuous improvement. Compliance audits should be viewed as opportunities for growth rather than mere checkboxes on a list. This mindset can create a more resilient and compliant organization over time.

Emerging Trends in Cybersecurity Compliance
Impact of Artificial Intelligence
As organizations strive to enhance their cybersecurity posture, the impact of artificial intelligence (AI) cannot be overlooked. AI-driven tools are revolutionizing how companies approach compliance. They offer advanced threat detection, automate repetitive tasks, and analyze vast data sets to identify vulnerabilities. For example, AI can:
- Enhance Threat Intelligence: Quickly analyze patterns of behavior to detect anomalies before they escalate.
- Automate Reporting: Streamline compliance documentation, allowing teams to focus on strategic initiatives rather than manual data entry.
By integrating AI into compliance strategies, organizations can not only improve their defenses but also increase efficiency, making it a game-changer in the cybersecurity landscape.
Focus on Supply Chain Security
Another emerging trend is the heightened focus on supply chain security. With increasing interconnectivity among businesses, vulnerabilities can arise from third-party providers. Organizations are now emphasizing:
- Vendor Risk Assessments: Conducting evaluations of third-party vendors to ensure they maintain adequate security standards.
- Continuous Monitoring: Implementing ongoing assessments to detect potential weaknesses in the supply chain.
Companies are recognizing that ensuring compliance doesn’t stop at their own door; it extends to their entire supply chain, making it imperative to collaborate closely with partners. By adopting these trends, organizations can build a more comprehensive and resilient compliance framework prepared to tackle the challenges of today’s digital world.
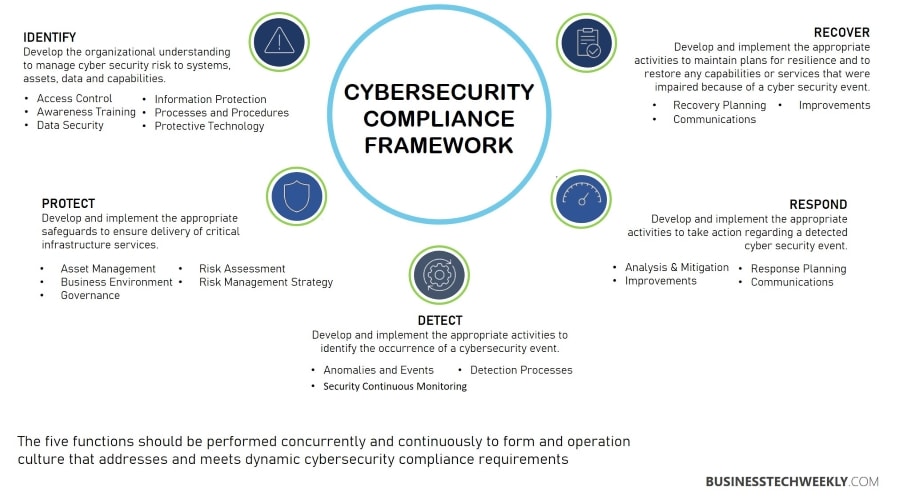
Case Studies and Examples of Cybersecurity Compliance Success Stories
Company A: Achieving Compliance in the Healthcare Industry
In the ever-sensitive healthcare environment, Company A successfully navigated the complexities of HIPAA compliance. Faced with challenges around protecting patient data, they initiated a comprehensive compliance program that included:
- Robust Risk Assessments: Regularly identifying vulnerabilities in their systems.
- Employee Training: Implementing a mandatory training program that educated staff about data protection and compliance protocols.
By meticulously documenting processes and investing in advanced security technologies, Company A not only achieved compliance but also built trust with their patients, leading to higher patient satisfaction ratings.
Company B: Implementing Effective Compliance Measures in the Financial Sector
Similarly, Company B, a financial institution, tackled the Payment Card Industry Data Security Standard (PCI DSS) requirements. Their approach involved:
- Strengthening Security Protocols: Enhancing firewalls and encryption methods to safeguard transactions.
- Continuous Auditing: Conducting regular internal assessments and inviting external audits to ensure ongoing compliance.
These measures paid off, as Company B reported a significant reduction in security breaches and associated costs. Their commitment to compliance not only fulfilled regulatory requirements but also solidified customer confidence, ultimately enhancing their market reputation. Both stories exemplify how a strategic focus on cybersecurity compliance can lead to significant organizational benefits across various industries.

Future Outlook and Recommendations
Predictions for the Future of Cybersecurity Compliance
Looking ahead, the landscape of cybersecurity compliance is poised for significant evolution. Key predictions include:
- Increased Regulation: As cyber threats grow in sophistication, governments are likely to introduce stricter regulations to safeguard sensitive data across industries.
- Integration of AI and Automation: The adoption of AI for real-time compliance monitoring will become more prevalent, enabling organizations to quickly identify and address vulnerabilities.
- Emphasis on Privacy: With growing public concern over data privacy, businesses will need to prioritize transparency and individual rights to maintain consumer trust.
These trends will reshape how organizations approach compliance, making it essential to stay ahead of the curve.
Recommended Practices for Sustaining Compliance
To thrive in this evolving environment, organizations should consider the following practices:
- Ongoing Education: Continuously train employees on compliance standards and emerging threats.
- Regular Audits and Assessments: Implement a routine schedule for internal audits to identify areas for improvement.
- Collaboration with Experts: Partner with cybersecurity specialists or consult with external auditors to ensure your compliance efforts are robust.
By adopting these recommendations, organizations can better position themselves for future challenges while fostering a culture of compliance that adapts to the ever-changing digital landscape.

