Introduction
Understanding Machine Learning in Cybersecurity
In today’s digital age, the integration of Machine Learning (ML) in cybersecurity is transforming how we protect sensitive information. Imagine personal data, like financial details or medical records, being targeted by cybercriminals. Machine learning algorithms analyze vast amounts of data to identify patterns and detect anomalies before they can lead to breaches. For instance, a typical organization might process millions of transactions daily; ML helps in flagging unusual patterns in these transactions, prompting immediate investigation.
Why Data Safeguarding is Essential in Cybersecurity
Data safeguarding has become the linchpin of cybersecurity strategies. As technology evolves, so do the tactics of cyber attackers. Here are a few reasons why prioritizing data protection is crucial:
- Protection Against Breaches: Safeguarding data reduces the risk of infiltration.
- Compliance with Regulations: Organizations must adhere to laws like GDPR to avoid heavy penalties.
- Trust and Reputation: Customers expect that their data is secure—trust is vital for business survival.
Incorporating machine learning into these efforts strengthens defenses and provides a proactive approach to protecting valuable data assets.

Fundamentals of Machine Learning
Definition of Machine Learning
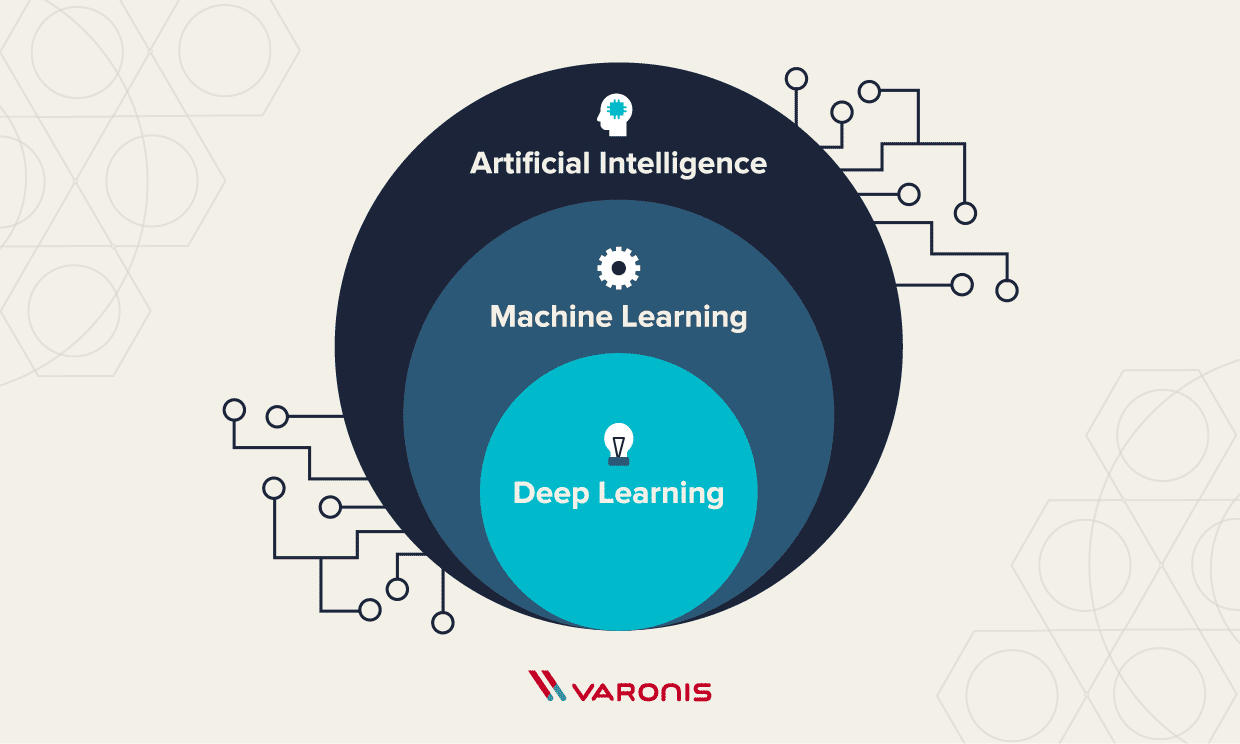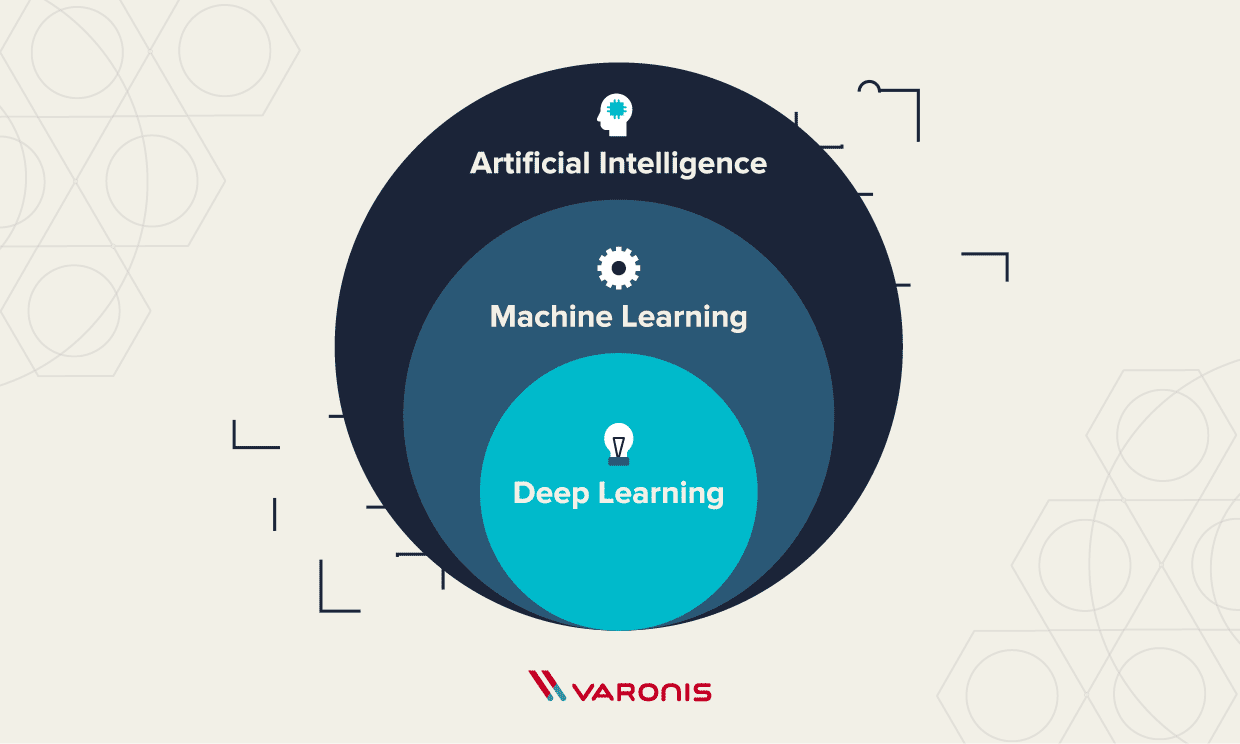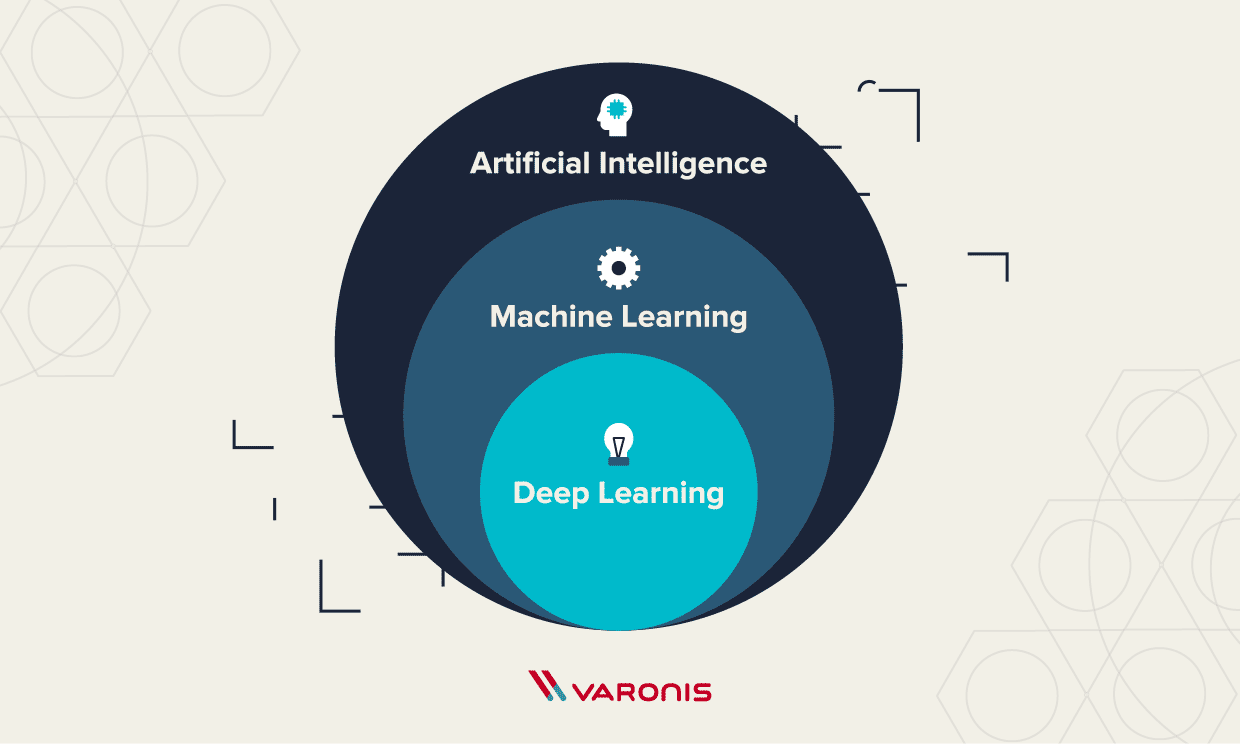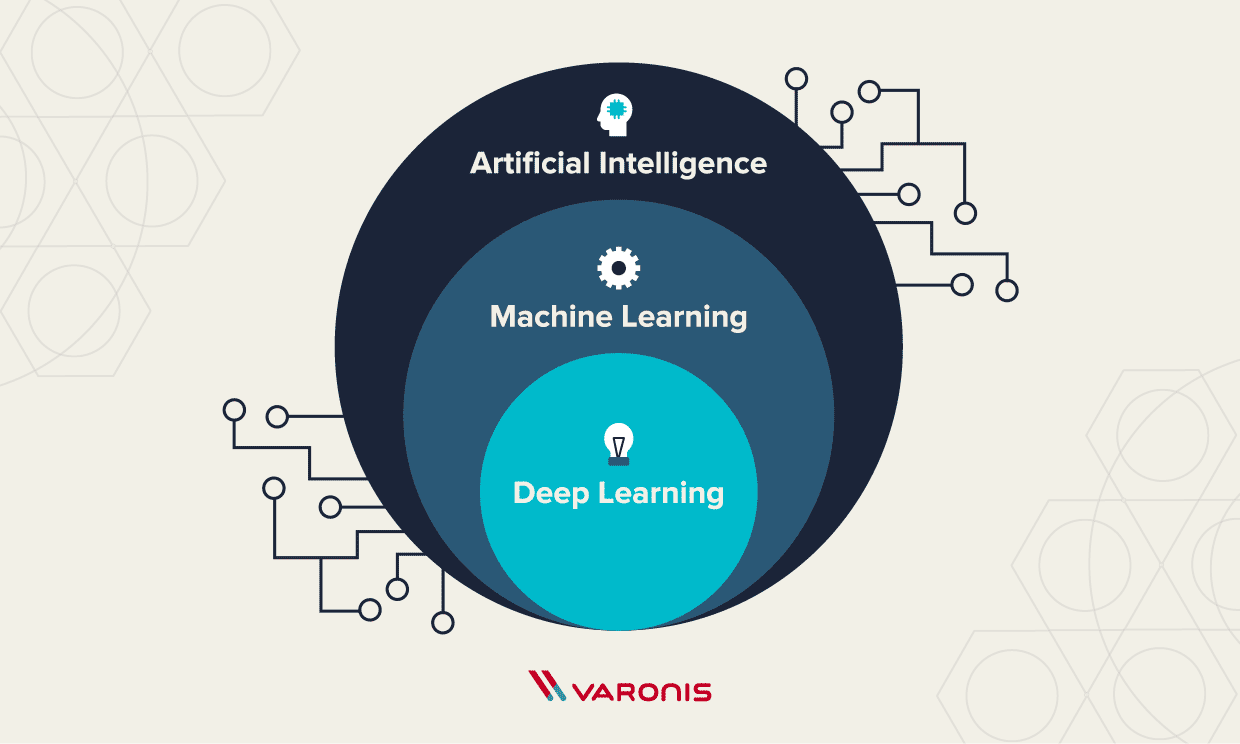
To grasp the impact of Machine Learning in cybersecurity, it’s essential to understand its definition. Machine Learning refers to a subset of artificial intelligence, where algorithms learn from data patterns. Instead of being explicitly programmed, these systems improve their performance over time through experience. Think of it as training a pet—consistent practice leads to better behavior and understanding.
Types of Machine Learning Algorithms
The diversity of Machine Learning algorithms enables various applications. Here are the primary types:
- Supervised Learning: Uses labeled data to train algorithms. For instance, a spam detection system uses emails marked as spam or not spam to learn.
- Unsupervised Learning: Works with unlabeled data, identifying structures or clusters within. Anomaly detection is a prime example.
- Reinforcement Learning: Introduces a reward-based system that motivates an algorithm to make optimal decisions over time.
Role of Machine Learning in Cybersecurity
In the context of cybersecurity, Machine Learning plays a critical role by providing adaptive and automated defenses. It analyzes real-time data from network traffic patterns to detect potential threats efficiently. For example, it can rapidly identify malware or phishing attempts, allowing organizations to respond swiftly and effectively. In a world of evolving cyber threats, leveraging ML is more vital than ever for robust security measures.
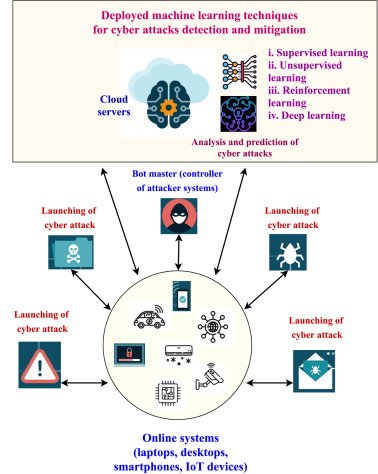
Applications of Machine Learning in Cybersecurity
Threat Detection and Intrusion Prevention
Building on the fundamentals of Machine Learning, its applications in cybersecurity are revolutionary. One of the primary uses is in threat detection and intrusion prevention. ML algorithms monitor network activity for unusual behaviors that may signal an attack. Imagine a digital security guard continuously analyzing visitor patterns; when something seems off—like an unusual login from a different country—it raises a red flag.
Anomaly Detection and Behavioral Analysis
Another critical application is anomaly detection and behavioral analysis. These systems establish a baseline of normal user behavior and can identify deviations swiftly. For instance, if an employee who typically accesses files during regular hours suddenly downloads large volumes of sensitive data at midnight, an alert is triggered. This approach not only helps in identifying potential insider threats but also protects against external attacks.
Risk Assessment and Vulnerability Management
Finally, Machine Learning enhances risk assessment and vulnerability management. It can analyze historical data to predict potential vulnerabilities and prioritize remediation efforts. By employing ML, organizations can allocate resources to the most critical areas, ensuring better protection. In this continually evolving landscape, these applications of Machine Learning enable companies to stay ahead of cyber threats effectively.

Machine Learning Techniques for Data Protection
Encryption and Data Masking
Transitioning from understanding the applications of Machine Learning, we delve into specific techniques that bolster data protection. One prominent technique is encryption, which transforms readable data into unreadable code. Machine Learning enhances this process by analyzing data patterns, informing users when particular encryption methods are most effective. Similarly, data masking involves altering sensitive information to protect it during processing or storage. For instance, a hospital may mask patient names in a dataset while maintaining the integrity of other medical information for analysis.
Access Control and Authorization Techniques
Access control and authorization techniques form another crucial layer of data protection. Machine Learning can analyze user behavior to dynamically adjust access rights. Imagine an employee trying to access sensitive data; if their typical access patterns change, ML algorithms can flag or deny access, ensuring that only appropriate personnel can view critical information.
Security Monitoring and Incident Response
Lastly, security monitoring and incident response thrive on Machine Learning’s analytical capabilities. These systems continuously evaluate security logs and user activities for irregularities. When potential threats arise, they trigger automated responses—like isolating affected systems—which significantly reduces response times. By integrating these machine learning techniques, organizations can create a fortified environment equipped to handle the ever-evolving landscape of cyber threats effectively.

Challenges and Limitations of Machine Learning in Cybersecurity
Data Privacy Concerns
While Machine Learning offers impressive solutions for cybersecurity, it comes with its own set of challenges and limitations. One significant issue is data privacy concerns. As these algorithms often require access to large datasets, organizations must ensure they don’t inadvertently expose sensitive information. Imagine a scenario where user data is used for model training without proper anonymization; this could lead to serious privacy breaches and regulatory non-compliance, risking both reputations and finances.
Adversarial Attacks
Another pressing challenge is the risk of adversarial attacks. Malicious actors may exploit vulnerabilities in machine learning models, creating deceptive inputs that can mislead algorithms. For example, an attacker could craft inputs designed to bypass an intrusion detection system, effectively evading security measures.
Overfitting and False Positives
Lastly, issues like overfitting and false positives can hamper the effectiveness of machine learning in cybersecurity. Overfitting occurs when a model learns noise rather than the actual signal, leading to poor performance on new data. Additionally, false positives—when legitimate actions are incorrectly flagged as threats—can overwhelm security teams and dilute focus. Balancing these challenges while leveraging machine learning is vital for crafting effective cybersecurity strategies.

Best Practices for Implementing Machine Learning in Cybersecurity
Data Quality and Feature Selection
Shifting from the limitations of Machine Learning in cybersecurity, it’s crucial to consider best practices for effective implementation. The first and foremost principle is ensuring high data quality and careful feature selection. Quality data drives accurate predictions, so organizations should invest in cleaning and preprocessing datasets. Consider an anecdote: a company may have tons of logs but if they contain irrelevant or duplicate entries, the ML model’s accuracy could suffer. Focused feature selection, where only the most relevant data points are used, can enhance model performance significantly.
Continuous Training and Model Evaluation
Continuous training and model evaluation are also vital. Cyber threats evolve rapidly, so models need regular updates to adapt to new attack vectors. Implement a robust feedback loop: regularly assess model performance using real-time data and tweak algorithms to improve accuracy. This practice prevents obsolescence and ensures relevance in a dynamic landscape.
Collaboration with Security Experts
Lastly, collaboration with security experts is essential. Engaging with professionals who understand both cybersecurity and machine learning can bridge gaps. They can offer insights into selecting the right algorithms and monitoring model outcomes effectively. By following these best practices, organizations can harness the full potential of machine learning to shield against cyber threats more effectively.

Real-world Examples of Machine Learning in Cybersecurity
Case Study 1: Malware Detection
Having explored best practices, it’s intriguing to look at how these principles translate into real-world applications. A prime example is malware detection. Major cybersecurity firms like Symantec utilize machine learning algorithms to identify and classify malware based on behavioral patterns rather than traditional signature-based methods. This means that even new, previously unseen malware can be detected by analyzing its behavior during execution. For instance, if a piece of software attempts to access sensitive system files without proper permissions, the system flags it as suspicious, allowing for swift action.
Case Study 2: Phishing Email Recognition
Another compelling case study is in phishing email recognition. Organizations such as Google employ machine learning models to analyze email characteristics, scrutinizing various features like sender reputation, language used, and email structure. By training these models on vast datasets of legitimate and phishing emails, they can filter out harmful messages effectively. One interesting outcome is that these models dramatically reduced the number of phishing emails reaching user inboxes, showcasing the transformative power of machine learning in enhancing cybersecurity measures. These real-world examples demonstrate how organizations can effectively leverage machine learning to protect against pervasive cyber threats.

understand the reasoning behind its alerts. Explainable AI aims to demystify these processes, allowing cybersecurity teams to comprehend the ‘why’ behind flagging certain behaviors or transactions. This transparency not only enhances trust in automated systems but also fosters better collaboration between AI and human decision-makers.
Integration with AI-driven Security Operations Centers
Another promising trend is the integration of Machine Learning with AI-driven Security Operations Centers (SOCs). These advanced centers utilize automated systems to analyze data, identify threats, and respond to incidents in real time. Imagine a scenario where a SOC uses Machine Learning algorithms to automatically correlate thousands of logs from various sources—this capability enhances efficiency and drastically reduces response times.
Furthermore, such integration facilitates proactive threat hunting, enabling organizations to detect vulnerabilities before they are exploited. As businesses increasingly embrace these future trends, the synergy between Machine Learning and cybersecurity will not only strengthen defenses but also help organizations navigate the complexities of the digital threat landscape more effectively.
Conclusion
Recap of Key Points
As we conclude our exploration of Machine Learning in cybersecurity, it’s essential to recap the key points discussed. We highlighted how Machine Learning transforms threat detection, with practical applications like malware detection and phishing recognition. Furthermore, we examined best practices, emphasizing the significance of data quality and ongoing model evaluation. The challenges of this technology, including data privacy concerns and the risk of adversarial attacks, remind us that while ML is powerful, it’s not without its hurdles.
Emphasizing the Importance of Machine Learning in Safeguarding Data
In today’s rapidly evolving cyber threat landscape, the importance of Machine Learning in safeguarding data cannot be overstated. By leveraging advanced algorithms, organizations can proactively defend against diverse cyber threats, ensuring the safety of sensitive information. As future trends like explainable AI and integration with AI-driven Security Operations Centers emerge, we can expect even more sophisticated protection mechanisms. Ultimately, embracing Machine Learning is not just a trend; it’s a vital step towards building a robust cybersecurity framework that stands resilient against future vulnerabilities, enabling organizations to thrive in an increasingly digital world.