
Understanding Cybersecurity Compliance Audits
Definition and Purpose of Cybersecurity Compliance Audits
Cybersecurity compliance audits are systematic evaluations designed to assess whether an organization adheres to various security standards and regulations. These audits serve a crucial purpose in today’s fast-paced digital landscape, ensuring that sensitive data remains protected against breaches and vulnerabilities. Think of it as a health check-up for your organization’s cybersecurity posture.
The primary objectives of these audits include:
- Identifying Weaknesses: Spotting gaps in your security measures before they can be exploited.
- Ensuring Compliance: Verifying that applicable laws and industry standards are being followed.
- Enhancing Trust: Building confidence among customers and stakeholders that their data is secure.
Regulatory Frameworks and Standards
Organizations often navigate a complex web of regulations and standards when preparing for compliance audits. Some of the most prominent include:
- ISO/IEC 27001: A global standard for managing information security.
- NIST Cybersecurity Framework: Provides guidelines for improving security practices.
- GDPR: Regulations focused on data protection and privacy for individuals in the European Union.
Understanding these frameworks not only helps an organization stay compliant but is also essential for developing an effective cybersecurity strategy. By embedding these standards into their operational fabric, businesses can enhance their security posture significantly.
By grasping the fundamentals of cybersecurity compliance audits, organizations can lay a solid foundation for compliance initiatives and better prepare for future audits, ultimately strengthening their security defenses.
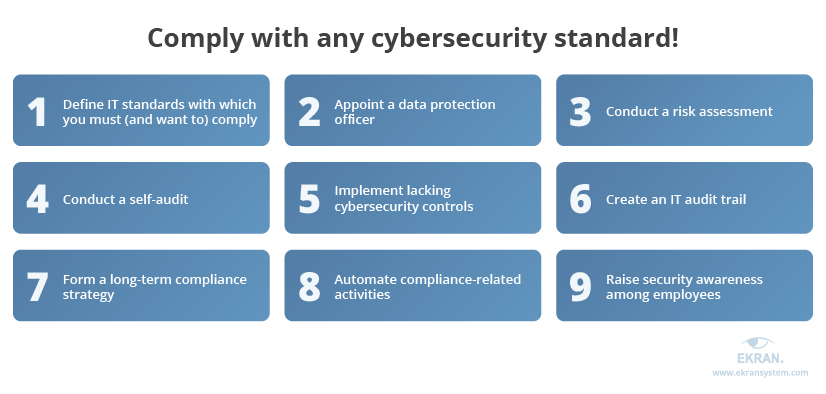
Importance of Preparing for a Cybersecurity Compliance Audit
Potential Consequences of Non-Compliance
Failing to prepare for a cybersecurity compliance audit can lead to severe repercussions that extend beyond just a failed audit. Organizations should understand that non-compliance can result in:
- Heavy Fines: Many regulatory bodies impose significant penalties for failing to meet compliance standards.
- Legal Ramifications: Non-compliance can open a floodgate to lawsuits from customers or other stakeholders.
- Reputation Damage: A publicized data breach or compliance failure can tarnish your brand’s reputation and erode customer trust.
For instance, consider a company that faced massive financial penalties after a data breach was attributed to non-compliance with data protection regulations. The fallout didn’t just affect their bank account but also jeopardized their client relationships.
Benefits of Proactive Preparation
On the flip side, preparing proactively for a compliance audit brings a host of advantages:
- Streamlined Processes: A well-prepared organization has smooth procedures in place, making audits less stressful.
- Risk Mitigation: Proactive measures help identify vulnerabilities before they turn into incidents.
- Boosted Credibility: Demonstrating compliance can greatly enhance your organization’s reputation, attracting new customers and retaining existing ones.
When companies actively engage in preparation, they foster a culture of security, ensuring that their cybersecurity practices become part of the organization’s DNA. It’s like building a robust defense wall before the storm hits—preparation today establishes a strong foundation for tomorrow.
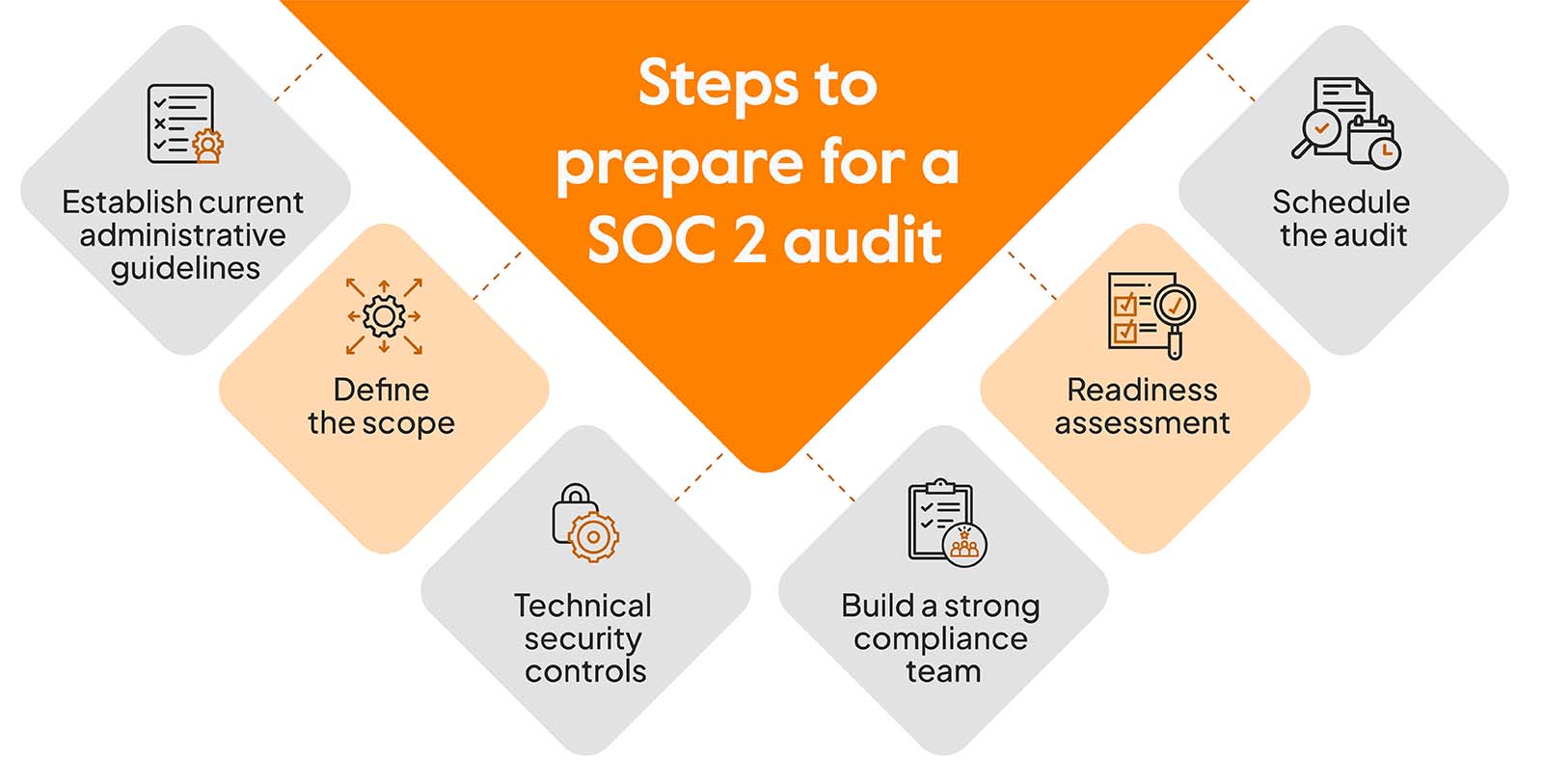
Initial Preparation Steps
Conducting a Security Risk Assessment
The journey to cybersecurity compliance begins with a comprehensive security risk assessment. This foundational step helps organizations identify their critical assets and the potential risks they face. By understanding these risks, businesses can prioritize their security efforts effectively.
To conduct a thorough risk assessment, consider these steps:
- Identify Assets: What data and systems are the most valuable?
- Determine Vulnerabilities: What weaknesses exist that could be exploited?
- Evaluate Threats: What potential threats could target these vulnerabilities?
An organization I once worked with discovered through their risk assessment that outdated software was exposing them to cyber threats. This realization prompted them to implement timely updates, significantly enhancing their security posture.
Gap Analysis for Compliance Requirements
Once you have a clear picture of your risks, the next step is to perform a gap analysis against the relevant compliance requirements. This process uncovers discrepancies between your current security practices and the standards you need to meet.
During a gap analysis, focus on:
- Mapping Policies: Compare existing security policies with compliance standards.
- Identifying Shortcomings: Highlight specific areas where your practices fall short.
- Developing Remediation Plans: Create action items to address identified gaps.
By doing this, businesses can proactively address compliance issues, reducing the risk of surprises during the audit and making the overall process less daunting. The groundwork laid at this stage is vital, as it sets the tone for a successful compliance audit, ensuring that organizations are not just reactive, but strategically prepared.

Developing a Compliance Strategy
Establishing Security Policies and Procedures
With a solid understanding of risks and compliance gaps in place, the next step is to develop a robust compliance strategy, beginning with the establishment of clear security policies and procedures. These policies serve as the organization’s security framework, guiding employees in safeguarding sensitive data.
When crafting effective security policies, consider the following:
- Define Clear Roles: Who is responsible for what? Establish roles for cybersecurity responsibilities.
- Data Classification: Categorize data based on sensitivity and apply appropriate security measures.
- Incident Response Plan: Outline steps for addressing potential security breaches to minimize impact.
For instance, a company I consulted with turned their security policy into a live document that was regularly reviewed and updated, ensuring employees always had access to the latest information. This proactive approach made a significant difference during audits.
Implementation of Technical Controls
Next comes the implementation of technical controls, which are essential to the effectiveness of your security policies. Technical controls are the software and hardware solutions that safeguard your systems from threats.
Key technical controls to consider include:
- Firewalls and Intrusion Detection Systems (IDS): To monitor and control network traffic.
- Encryption: Ensuring that sensitive data is unreadable to unauthorized users.
- Multi-Factor Authentication (MFA): Adding an extra layer of security for user access.
Think of technical controls as the defense mechanisms that work alongside your policies to create a fortified security environment. A small business I worked with saw exponential improvement in their security posture after deploying multi-factor authentication, significantly reducing unauthorized access attempts. By establishing effective policies coupled with the right technical controls, organizations can create a strong compliance strategy, ensuring they are well-prepared for any audits ahead.

Training and Awareness Programs
Educating Employees on Security Best Practices
Having established a solid compliance strategy, the next critical aspect is empowering your employees through training and awareness programs. After all, they are the first line of defense against cyber threats. Educating staff on security best practices not only helps protect sensitive data but also fosters a culture of security within the organization.
When implementing training programs, consider these key components:
- Regular Workshops: Host monthly or quarterly sessions to keep cyber awareness fresh.
- Customized Training Modules: Tailor content to specific roles within the organization to enhance relevance.
- Assessments: Follow up training with quizzes to gauge understanding and retention.
For example, I remember a financial services firm that introduced a fun, interactive quiz about phishing scams. Employees were eager to participate, and the result was a dramatic increase in their ability to spot potential threats.
Conducting Mock Audit Drills
The culmination of your training efforts can be seen in the results of conducting mock audit drills. These simulations replicate an actual compliance audit, allowing employees to practice what they’ve learned in a controlled environment.
Consider the following when planning mock drills:
- Realistic Scenarios: Create scenarios that mirror potential audit situations they’ll encounter.
- Feedback Sessions: Allow participants to discuss what went well and areas for improvement.
- Record Keeping: Document findings and action items for future reference.
One organization I consulted with conducted quarterly mock audits, uncovering gaps in their processes that hadn’t been previously noticed. This initiative not only prepared them for actual audits but also fostered teamwork and accountability. By prioritizing training and conducting mock audits, organizations can significantly bolster their compliance readiness, leading to a smoother audit experience.

Engaging External Auditors
Selecting an Audit Firm
Now that your organization has invested in training and preparation, it’s time to take the next critical step: engaging external auditors. Selecting the right audit firm can significantly impact the effectiveness of your compliance audit. You want a team that not only understands regulatory requirements but also aligns with your organization’s culture and goals.
Here are some tips for selecting the right audit firm:
- Industry Experience: Ensure the firm has experience in your specific industry and understands the relevant compliance requirements.
- Reputation: Check reviews and ask for references to gauge their credibility and effectiveness.
- Approachability: Choose a firm that communicates clearly and fosters a collaborative relationship.
For instance, I remember working with a healthcare provider that selected an audit firm known for its friendly approach. The auditors became not just assessors but valuable partners in improving their security processes.
Preparing Documentation for Audit Review
Once you’ve selected the right audit firm, the next step is to prepare the necessary documentation for the audit review. Thorough documentation is key to demonstrating compliance and streamlining the auditing process.
To ensure you’re well-prepared, consider these essential documents:
- Security Policies and Procedures: Provide an up-to-date copy of your organization’s security policies.
- Incident Reports: Include documentation of any past security incidents and how they were addressed.
- Training Records: Show evidence of employee training sessions and assessments on security best practices.
A client of mine once discovered that their documentation was outdated and poorly organized just weeks before an audit. They scrambled to compile everything, which led to unnecessary stress. By preparing ahead of time, organizations can not only meet compliance requirements but also build a productive relationship with their auditors, ultimately paving the way for a successful audit process.

Internal Compliance Monitoring
Continuous Monitoring and Incident Response
As the dust settles from the audit and preparations, the journey doesn’t end there; organizations must focus on internal compliance monitoring. Continuous monitoring ensures that your cybersecurity measures remain effective over time. It’s akin to keeping an eye on the health of your cybersecurity posture in real-time.
To establish an effective continuous monitoring process, organizations should:
- Implement Real-Time Alerts: Use security tools that send notifications for unusual activities or potential breaches.
- Conduct Regular Audits: Schedule monthly or quarterly audits to assess ongoing compliance with policies.
- Review Logs: Regularly analyze system logs for signs of suspicious activities.
For example, a banking institution I worked with implemented a real-time monitoring system that alerted them to anomalous behavior. Thanks to their proactive measures, they were able to thwart a potential breach before it escalated.
Review and Improvement Processes
Alongside continuous monitoring, regular review and improvement processes are essential for maintaining compliance. This involves revisiting policies, procedures, and technologies to adapt to emerging threats and regulatory changes.
Key steps in this process include:
- Feedback Loops: Establish channels for employees to report security concerns or suggest improvements.
- Annual Policy Reviews: Regularly update security policies based on findings from compliance monitoring and changing regulations.
- Performance Metrics: Use data from monitoring efforts to measure the effectiveness of compliance programs and identify areas for enhancement.
A former client found that by actively reviewing and updating their policies based on these metrics, they could not only meet compliance standards but also significantly reduce their vulnerability to security threats. By prioritizing internal compliance monitoring, organizations can cultivate a dynamic security environment that not only meets regulations but adapts to the ever-evolving cybersecurity landscape.
Remediation Plans and Follow-up Actions
Addressing Audit Findings
Following an audit, it’s crucial to address any findings promptly. These findings can highlight vulnerabilities or compliance gaps that require immediate attention. Ignoring them can lead to serious ramifications, but taking remedial action not only mitigates risks but also demonstrates a commitment to continuous improvement.
When addressing audit findings, consider these steps:
- Prioritize Findings: Categorize issues based on severity and potential impact to allocate resources effectively.
- Communicate Transparently: Keep stakeholders informed about findings and the steps being taken to address them. Transparency builds trust within the organization.
- Set Clear Deadlines: Establish timelines for when specific issues will be resolved, holding teams accountable for progress.
I recall assisting a tech company that faced several audit findings related to their data protection measures. By prioritizing these quickly, they were able to resolve significant issues, enhancing their system’s integrity.
Implementing Remediation Plans
Once findings are prioritized, the next step is to implement remediation plans. These plans outline specific actions to remediate each issue identified during the audit.
To effectively implement these plans, follow these guidelines:
- Assign Responsibilities: Designate team members responsible for executing each part of the remediation plan.
- Monitor Progress: Use performance metrics to track the effectiveness of remediation actions and ensure timely completion.
- Conduct Follow-Up Audits: Schedule subsequent reviews to evaluate the effectiveness of implemented changes and ensure compliance.
In one instance, a financial firm I worked with created a comprehensive remediation plan that not only addressed audit findings but also established ongoing monitoring processes. This proactive approach resulted in enhanced security and compliance resilience.
By diligently addressing audit findings and implementing effective remediation plans, organizations can significantly boost their security posture and safeguard against future compliance issues.
Maintaining Ongoing Compliance
Regular Security Assessments
To ensure that your organization remains compliant over the long haul, regular security assessments are essential. These assessments help identify new vulnerabilities and allow you to stay ahead of potential threats, much like regular check-ups keep your health in check.
When planning regular security assessments, consider these best practices:
- Schedule Assessments Periodically: Conduct assessments at least twice a year or whenever significant changes occur in your systems.
- Engage External Experts: Sometimes, a fresh set of eyes can uncover issues that internal teams might overlook.
For instance, an energy company I collaborated with conducted regular security assessments and discovered a software vulnerability they hadn’t recognized. This proactive approach saved them from potential data breaches and reinforced their commitment to security.
Updating Policies and Procedures
Alongside regular assessments, consistently updating your policies and procedures is vital for maintaining compliance. As technology evolves and regulations change, your policies must adapt accordingly.
Key steps in updating policies include:
- Review Regulatory Changes: Stay informed about new legislation or changes to existing regulations that may impact your organization.
- Incorporate Feedback: Use insights gained from security assessments and employee feedback to enhance policies.
- Train Employees on Updates: Ensure that your team is aware of the latest policies through regular training sessions.
A retail client of mine realized they had outdated payment processing policies. After revising procedures based on recent industry standards, they not only improved security but also enhanced customer trust.
By committing to regular security assessments and updating policies as needed, organizations can effectively maintain ongoing compliance, ensuring a secure environment that stands strong against evolving threats.

Conclusion and Post-Audit Reflection
Lessons Learned from the Audit Process
As organizations conclude their cybersecurity compliance audits, it’s crucial to take a step back and reflect on the lessons learned throughout the process. Every audit provides valuable insights that can help refine and strengthen compliance strategies moving forward.
Consider these key takeaways:
- Identify Strengths and Weaknesses: A thorough audit will highlight what your organization is doing well, along with areas that need improvement.
- Enhance Communication: Often, audits reveal gaps in communication. Ensuring everyone understands their role in compliance is essential.
- Document Learnings: Maintain a post-audit record of lessons learned to guide future audits and compliance efforts.
For example, after an audit, a healthcare provider realized their onboarding process for new employees was lacking in crucial security training. This led to the development of a more robust orientation program, significantly reducing their vulnerabilities.
Continuous Improvement in Cybersecurity Compliance
Post-audit reflections should not end the discussion; instead, organizations need to emphasize continuous improvement in cybersecurity compliance.
Strategies for fostering continuous improvement include:
- Regular Training: Offer continual education and awareness programs for employees to stay updated on best practices.
- Adopt a Culture of Security: Encourage everyone in the organization to take ownership of cybersecurity responsibilities.
- Revisit and Revise Policies: Regularly update your security policies to reflect lessons learned and new regulatory requirements.
One organization I consulted for adopted a culture of ongoing feedback and improvement after their audit, leading to an agile compliance framework that could swiftly adapt to emerging threats.
In conclusion, embracing a mindset of continuous improvement not only enhances compliance but also fortifies overall cybersecurity resilience. With the right approach, every audit becomes more than just a compliance checkbox; it evolves into a learning opportunity that cultivates a stronger, more secure organization.

