
Introduction
Overview of Cyber Threats
In a world increasingly driven by technology, cyber threats have evolved into a formidable challenge for businesses and individuals alike. These threats manifest in various forms, ranging from malware and phishing attacks to more sophisticated ransomware and distributed denial-of-service (DDoS) attacks. The reality is that cybercriminals are continuously developing new methods to exploit vulnerabilities, creating a constantly shifting threat landscape.
Some common types of cyber threats include:
- Malware: Malicious software designed to cause harm, often lurking in unsuspecting downloads.
- Phishing: Deceptive communications aimed at tricking individuals into revealing sensitive information.
- Ransomware: A type of malware that encrypts files, demanding payment for their release.
- DDoS Attacks: Overwhelming a server with traffic, causing website outages.
Significance of Identifying Emerging Threats
Understanding emerging cyber threats is critical in maintaining cybersecurity. Identifying these threats early allows organizations to implement protective measures and mitigate risk. For instance, many companies now monitor their networks for behavioral anomalies, proactively detecting unusual patterns that may indicate a breach.
In today’s digital environment, staying one step ahead can mean the difference between a secure system and a significant data breach. Therefore, having a robust strategy for recognizing and combating these new threats is more important than ever. Engaging in proactive threat identification not only protects valuable data but also helps maintain customer trust and organizational integrity.

Understanding Cyber Threat Landscape
Different Types of Cyber Threats
After gaining insight into the overarching nature of cyber threats, it’s essential to delve deeper into the various types that organizations face today. Each type of threat has its unique characteristics and methods of operation. Familiarizing oneself with these can significantly enhance an organization’s defensive strategies.
The predominant types of cyber threats include:
- Malware: Broadly categorized into viruses, worms, trojans, and spyware, malware seeks to disrupt or damage devices and networks.
- Ransomware: This specific malware locks users out of their systems, demanding a ransom for access restoration. The infamous WannaCry attack in 2017 showcased just how damaging ransomware could be.
- Phishing Scams: A deceptively simple yet effective method where attackers impersonate legitimate entities to trick individuals into providing sensitive information.
- Insider Threats: Current or former employees may exploit their access to systems and data, causing harm either intentionally or through negligence.
Common Entry Points for Cyber Attacks
Understanding where attackers are likely to gain access can help in fortifying defenses. Cyber criminals often exploit the following common entry points:
- Email: Phishing emails remain one of the most popular ways for attackers to infiltrate networks.
- Unpatched Software: Outdated software can contain vulnerabilities that hackers can exploit.
- Weak Passwords: Many breaches occur due to poor password management. Simple passwords can easily be cracked.
- Remote Desktop Protocol (RDP): Exposed RDP services can allow attackers to take control of systems remotely.
Recognizing these vulnerabilities is the first step in effectively securing an organization against cyber threats. By addressing these entry points, organizations can significantly reduce their risk of being targeted.

Identifying Emerging Cyber Threats
Behavioral Anomalies Detection
As cyber threats continue to evolve, organizations must employ innovative detection methods to identify potential risks. One highly effective approach is behavioral anomalies detection, which focuses on identifying deviations from established user behaviors. This technique leverages advanced machine learning algorithms and analytics to monitor user activity.
Imagine a scenario where a finance employee, typically logging in from the office, suddenly accesses company systems from an unusual geographical location at odd hours. Such anomalies can signal unauthorized access attempts. Key benefits of behavioral anomalies detection include:
- Real-time Alerts: Immediate notifications when suspicious activities are detected.
- User Context Awareness: Understanding normal behaviors helps pinpoint actual threats effectively.
- Reduced False Positives: By focusing on behavioral patterns, organizations can minimize alerts for benign activities.
Threat Intelligence Gathering Techniques
In tandem with behavioral detection, gathering threat intelligence is a vital component of identifying emerging cyber threats. This process involves collecting and analyzing data about potential threats to inform decision-making. Some effective techniques include:
- Open Source Intelligence (OSINT): Utilizing publicly available information to monitor emerging threats.
- Information Sharing Platforms: Collaborating with other organizations and sharing insights on recent threats.
- Dark Web Monitoring: Keeping an eye on underground forums to anticipate potential data breaches.
By integrating these techniques, organizations can develop a more comprehensive understanding of the threat landscape. This, in turn, allows for more proactive defenses against emerging cyber risks, potentially saving both time and resources in the long run.
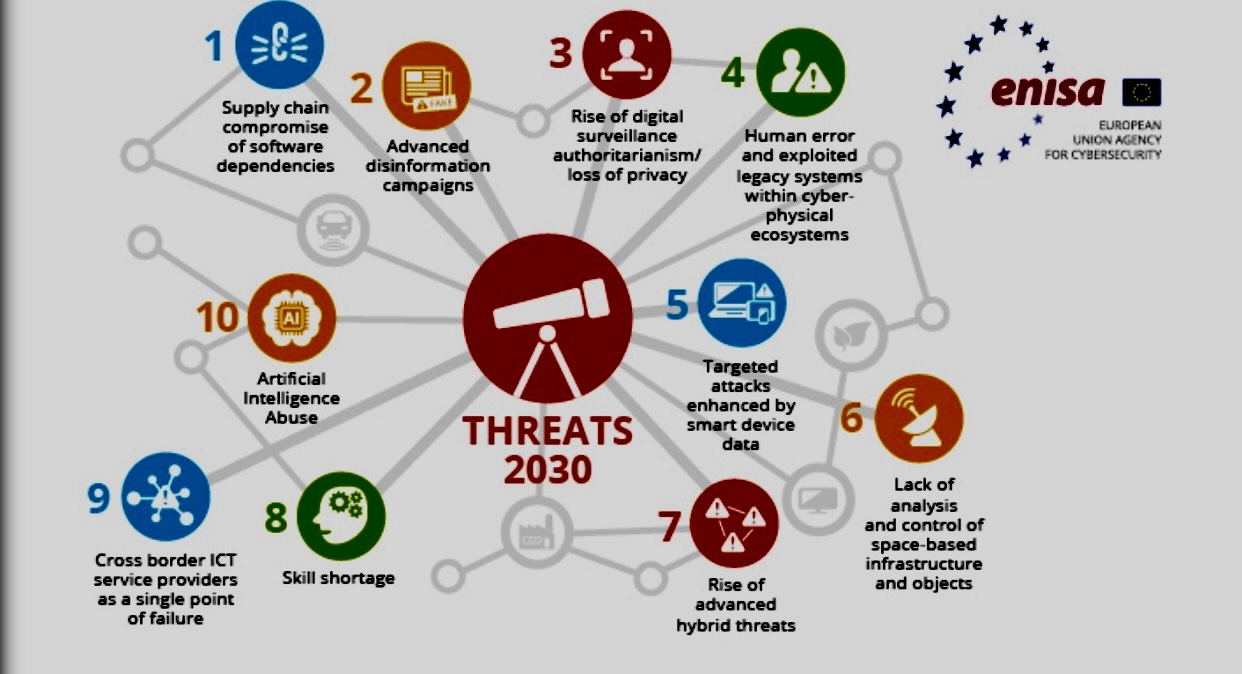
Impact of Emerging Cyber Threats
Consequences of Ignoring Threats
Failing to recognize and address emerging cyber threats can lead to catastrophic consequences for organizations. Ignoring these risks can create vulnerabilities that cybercriminals are eager to exploit. The fallout from these breaches can be extensive, affecting not just the immediate victims but also customers and partners.
Some serious consequences include:
- Financial Loss: The cost of recovering from a cyber incident can reach millions, including fines, legal fees, and lost revenue.
- Reputation Damage: Customers are less likely to trust organizations that fail to protect their data, leading to long-lasting reputational harm.
- Operational Disruption: Cyber attacks can paralyze operations, disrupting services and delaying projects.
- Regulatory Penalties: Non-compliance with data protection regulations may result in hefty fines and increased scrutiny from authorities.
Given these risks, the imperative to act cannot be understated.
Case Studies
Examining specific cases helps illustrate the devastating effects of ignoring emerging cyber threats. Take, for example, the infamous Equifax data breach in 2017. The company neglected to patch a known vulnerability, resulting in the exposure of sensitive data for over 147 million people. The aftermath included:
- Over $4 billion in costs related to breach mitigation and legal settlements.
- Severe damage to trust, with stock prices plummeting and a significant loss of customer loyalty.
Another example is the Colonial Pipeline ransomware attack, which led to fuel shortages across the East Coast of the United States. The company’s failure to proactively monitor their security environment resulted in:
- A ransom payment of $4.4 million.
- Extended operational disruptions, highlighting the importance of robust cybersecurity protocols.
These case studies serve as poignant reminders of the necessity to stay vigilant and proactive in identifying and combating emerging cyber threats.

Combatting Cyber Threats
Cybersecurity Measures and Tools
In the ongoing battle against cyber threats, organizations must deploy a diverse array of cybersecurity measures and tools to create robust defenses. It’s not just about having a single firewall or antivirus; a layered security approach is essential to fend off sophisticated attacks effectively.
Here are some key cybersecurity measures that are proving effective today:
- Firewalls: Act as a barrier between trusted internal networks and untrusted external networks.
- Intrusion Detection Systems (IDS): Monitor network traffic for suspicious activity and alert administrators.
- Endpoint Protection: This safeguards devices like computers and mobile phones, crucial in today’s mobile work environment.
- Data Encryption: Protects sensitive data by making it unreadable to unauthorized users, thus adding an extra layer of security.
- Regular Software Updates: Keeping software updated closes vulnerabilities that attackers exploit.
Incident Response Planning
Despite the best defenses, breaches can still occur, making incident response planning vital. A well-defined and practiced response plan ensures that organizations can react swiftly and effectively to minimize damage.
Key components of an incident response plan include:
- Preparation: Training staff and ensuring tools are in place.
- Detection and Analysis: Rapid detection of the incident and determining its nature and extent.
- Containment, Eradication, and Recovery: Taking immediate steps to contain the breach, eliminate the threat, and recover systems and data.
- Post-Incident Analysis: Reviewing the response to identify lessons learned and improve future defenses.
An example from the retail sector illustrates this well: a company that proactively developed and tested its incident response plan managed to contain a data breach quickly, mitigating losses and reinforcing customer trust.
By implementing comprehensive cybersecurity measures and a robust incident response plan, organizations can better prepare themselves to combat cyber threats head-on.

Proactive Defense Strategies
Vulnerability Assessment
In the ever-evolving landscape of cyber threats, proactive defense strategies are essential for maintaining security. One of the most effective approaches is conducting regular vulnerability assessments. This practice enables organizations to identify, classify, and prioritize vulnerabilities within their systems before cybercriminals can exploit them.
A vulnerability assessment involves:
- Systematic Scanning: Utilizing automated tools to identify known vulnerabilities in software and hardware.
- Configuration Reviews: Checking system configurations to ensure compliance with security best practices.
- Risk Evaluation: Analyzing the potential impact of identified vulnerabilities to prioritize remediation efforts.
For instance, a financial institution that regularly conducts vulnerability assessments can swiftly identify weaknesses in their online banking platform, allowing them to address these issues before customer data is compromised.
Penetration Testing
While a vulnerability assessment identifies potential threats, penetration testing takes it a step further. This simulated cyber attack mimics real-world scenarios to assess the effectiveness of an organization’s security measures.
Key aspects of penetration testing include:
- Identifying Weaknesses: Testing systems, networks, and applications to discover exploitable vulnerabilities.
- Realistic Scenarios: Utilizing techniques similar to those employed by cybercriminals provides invaluable insights into potential breaches.
- Remediation Insights: Offering recommendations on how to strengthen defenses based on findings.
For example, a healthcare organization that undergoes penetration testing may discover that their remote access protocols are insufficient, leading to a strategy overhaul before any breach occurs.
By implementing both vulnerability assessments and penetration testing as part of their security posture, organizations can take significant strides in proactively defending against emerging cyber threats, thereby enhancing their overall resilience.

Collaboration and Information Sharing
Importance of Information Sharing
In the complex world of cybersecurity, collaboration and information sharing are paramount to effectively combat emerging threats. Organizations, whether public or private, are increasingly realizing that they cannot navigate this landscape in isolation. By sharing insights and experiences, companies can enhance their collective defenses and bolster resilience against cyber attacks.
The benefits of information sharing include:
- Access to Real-Time Threat Data: Organizations can stay informed about the latest vulnerabilities and attack vectors.
- Improved Incident Response: By understanding how others have responded to breaches, companies can refine their own response strategies.
- Building Trust and Resilience: Collaborative relationships foster a culture of security awareness, encouraging proactive measures across industries.
For instance, a tech company that shares intelligence about a recent phishing attack can help other firms in the sector strengthen their defenses against similar threats.
Public-Private Partnerships
Public-private partnerships play a crucial role in enhancing cybersecurity efforts. These collaborations bring together government agencies and private enterprises to share resources, tools, and expertise effectively.
Key elements of successful public-private partnerships include:
- Joint Training Programs: Conducting simulations and workshops to prepare both sectors for potential cyber incidents.
- Information Sharing Platforms: Establishing forums where stakeholders can exchange threat intelligence securely.
- Resource Allocation: Governments can support private firms in implementing security measures through grants and subsidies.
A notable example is the Cybersecurity and Infrastructure Security Agency (CISA) in the United States, which actively collaborates with businesses to enhance national cybersecurity readiness. Through partnerships like these, organizations can better defend against cyber threats and create a more secure digital environment for everyone.
By fostering collaboration and effective information sharing, the cybersecurity community can remain agile and responsive, significantly improving the chances of mitigating risks in a rapidly changing landscape.

Continuous Monitoring and Adaptation
Cyber Threat Hunting
Continuously monitoring for cyber threats is a vital component of a robust security strategy, and proactive cyber threat hunting plays a key role in this process. It involves actively searching for threats within an organization’s environment, not just relying on automated tools or alerts. This proactive approach helps organizations uncover hidden vulnerabilities that might otherwise go unnoticed.
Some key benefits of cyber threat hunting include:
- Enhanced Detection Capabilities: Skilled hunters can identify advanced threats that evade traditional security measures.
- Improved Incident Response: By understanding the tactics, techniques, and procedures (TTPs) used by attackers, organizations can better prepare for potential incidents.
- Strengthening Security Posture: Regular hunting exercises highlight weaknesses and inform security improvements.
For instance, a financial services firm that implemented a threat-hunting program found several unauthorized devices connected to their network, allowing them to shut down potential breaches before any damage occurred.
Importance of Regular Updates
Alongside threat hunting, the importance of regular updates cannot be overstated. Keeping systems, software, and applications up to date acts as a line of defense against known vulnerabilities. Cybercriminals often exploit outdated systems, so consistent patch management is crucial.
Regular updates deliver benefits such as:
- Fixing Vulnerabilities: Manufacturers release patches to address known security flaws, keeping systems secure.
- Increased System Performance: Updates often improve functionality and efficiency, enhancing user experience and productivity.
- Compliance Maintenance: Many regulatory frameworks require organizations to adhere to strict update schedules.
Consider a healthcare organization that regularly updates its patient management system. By applying these updates consistently, they not only protect sensitive patient data from breaches but also ensure compliance with healthcare regulations.
By implementing continuous monitoring through proactive threat hunting and ensuring regular updates, organizations can effectively improve their overall cybersecurity defenses and remain adaptive in the ever-evolving landscape of cyber threats.
Conclusion
Recap of Key Points
As we wrap up our exploration of identifying and combating emerging cyber threats, it’s essential to revisit the key points covered throughout the article. Cyber threats come in various forms, and organizations must be proactive in understanding these risks.
Here’s a quick recap:
- Identifying Emerging Threats: Utilizing behavioral anomalies detection and threat intelligence can significantly enhance threat identification.
- Proactive Defense Strategies: Conducting regular vulnerability assessments and penetration testing fortifies defenses against potential attacks.
- Collaboration and Information Sharing: Working together—especially through public-private partnerships—enhances collective defense efforts.
- Continuous Monitoring and Adaptation: Cyber threat hunting, coupled with regular updates, helps organizations stay ahead of evolving threats.
By keeping these strategies in mind, organizations can ensure a more secure environment.
Future Outlook
Looking ahead, the landscape of cybersecurity will continue to evolve alongside technological advancements. As cybercriminals develop more sophisticated tactics, organizations must stay ahead of the curve by adopting innovative security solutions.
Emerging trends include:
- Artificial Intelligence (AI) in Cybersecurity: AI tools will enhance threat detection and response times.
- Zero Trust Architecture: This approach requires verification from everyone trying to access resources, effectively reducing vulnerabilities.
- Increased Regulatory Scrutiny: Organizations should prepare for stricter compliance requirements as cyber threats become more widespread.
Ultimately, the future of cybersecurity lies in continuous adaptation and a commitment to remaining vigilant. By fostering a culture of security awareness and collaboration, organizations can build a resilient defense against the evolving landscape of cyber threats. By staying informed and proactive, the fight against cybercrime can continue effectively, ensuring a safer digital world for everyone.
