
Understanding Cybersecurity Audits
Definition of Cybersecurity Audit
A cybersecurity audit is a systematic evaluation of an organization’s information technology (IT) infrastructure, policies, and procedures to determine how well these align with industry standards and regulations. The goal is to assess the effectiveness of security measures in place and identify any vulnerabilities that might expose the organization to risk. Think of it as a health check-up for your digital landscape, ensuring everything is functioning optimally.
For example, if a restaurant reviews its food safety measures regularly, a business should conduct cybersecurity audits to ensure its digital assets are protected from potential threats.
Importance of Regular Audits
Regular cybersecurity audits play a vital role in maintaining the integrity and security of an organization’s data. Here are some key reasons why they are essential:
- Risk Identification: They help identify weaknesses and potential threats that could lead to data breaches.
- Compliance: Organizations can demonstrate compliance with industry regulations such as GDPR or HIPAA.
- Continuous Improvement: Regular audits provide opportunities for improving cybersecurity measures and protocols.
- Confidence Building: They enhance customer and stakeholder trust by showcasing a commitment to data security.
In today’s digital world, neglecting regular cybersecurity audits can be a costly oversight. As shared by a friend who faced a severe data breach, they learned the hard way that proactive measures are always better than reactive solutions. Emphasizing a strong cybersecurity strategy today ensures better protection for tomorrow.

Preparing for a Cybersecurity Audit
Establishing Audit Objectives
Before diving into a cybersecurity audit, it’s critical to establish clear objectives. These objectives serve as the foundation for what you hope to achieve during the audit process. Properly defined objectives not only guide the audit but also help ensure that resources are used efficiently.
A few key objectives to consider might include:
- Assessing Compliance: Ensuring that all cybersecurity measures align with industry regulations.
- Identifying Vulnerabilities: Finding any existing weaknesses in the system that might lead to a breach.
- Enhancing Security: Discovering areas for improvement to strengthen overall cybersecurity posture.
Consider a small tech startup my colleague worked with. They approached their audit without clear objectives and ended up missing critical vulnerabilities. They learned firsthand that a structured approach to establishing audit objectives can save time and resources.
Identifying Assets and Risks to Assess
Next, it’s time to identify the critical assets and potential risks that need assessment. This step requires a comprehensive understanding of the organization’s digital landscape.
Begin by listing out key assets such as:
- Data: Customer information, financial records, and proprietary data.
- Infrastructure: Servers, applications, and networks.
- Personnel: Employees who have access to sensitive information.
Once assets are identified, you should also evaluate the risks associated with each. This could include:
- Data Breaches: Unauthorized access or data theft.
- Malware Attacks: Infection or disruption of services.
- Insider Threats: Risks posed by employees with malicious intent.
By thoroughly identifying assets and risks, organizations position themselves for a more effective audit, ensuring that no stone is left unturned during the evaluation process. Remember, a well-prepared audit can significantly bolster your cybersecurity framework.
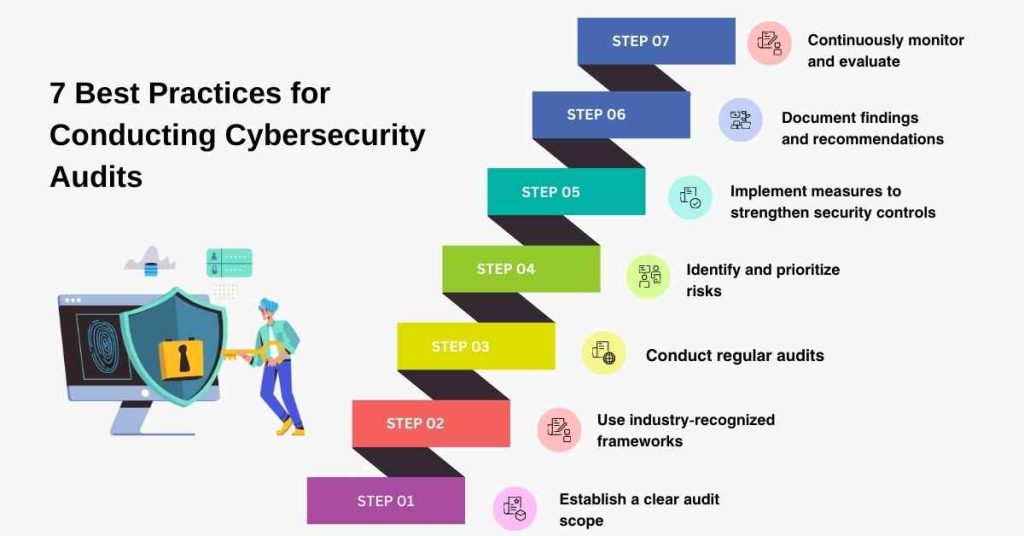
Conducting the Audit
Evaluating Existing Security Measures
With the groundwork laid and objectives defined, it’s time to conduct the actual cybersecurity audit. The first step in this phase involves evaluating existing security measures. This means taking a close look at the tools and protocols currently in place to safeguard sensitive data and systems.
Questions to consider during this evaluation include:
- What types of security software are being used?
- Are firewalls, intrusion detection systems, and encryption in effect?
- How often are security updates and patches applied?
For instance, my friend’s company had invested in a top-tier antivirus software but neglected to update it regularly. This oversight left them vulnerable to potential threats. Regular evaluations like these reveal gaps and encourage organizations to enhance their security frameworks.
Performing Vulnerability Assessments
Following the evaluation, the next step is to perform vulnerability assessments. This involves identifying, quantifying, and prioritizing vulnerabilities within the system. Here’s how to approach an effective vulnerability assessment:
- Automated Scanning: Use vulnerability scanning tools to identify known issues across systems and networks.
- Manual Testing: Conduct manual assessments to detect security weaknesses that automated tools might overlook.
- Risk Analysis: Evaluate the potential impact of discovered vulnerabilities on the organization’s assets.
In a recent audit conducted for a mid-sized business, a vulnerability assessment revealed outdated software that could expose them to data breaches. Addressing these vulnerabilities swiftly helped the company secure its infrastructure. Focusing on vulnerabilities can dramatically improve an organization’s resilience against cyber threats and fortify its overall cybersecurity posture.

Analyzing Audit Findings
Identifying Weaknesses and Gaps
After conducting a thorough cybersecurity audit and performing vulnerability assessments, the next pivotal step is analyzing the findings. This phase focuses on identifying weaknesses and gaps in the security framework. By closely reviewing the data collected during the audit, organizations can pinpoint specific areas needing attention.
Key areas to evaluate include:
- Outdated Software: Assess whether any systems are running obsolete applications susceptible to exploitation.
- Policy Flaws: Identify any security policies that may be lacking or poorly communicated among employees.
- Access Controls: Review user permissions to ensure that sensitive data is accessible only to those who need it.
A relatable example comes from a tech firm that discovered misconfigured user access rights during their audit. Employees had unnecessary permissions to sensitive databases, presenting a significant vulnerability. This realization emphasized the need for ongoing oversight.
Prioritizing Remediation Actions
Once weaknesses and gaps are identified, the next step involves prioritizing remediation actions. Not all vulnerabilities are created equal; hence, it’s crucial to address them according to their severity and potential impact.
Here’s a simple approach to prioritize remediation:
- Risk Level: Classify each vulnerability as high, medium, or low risk.
- Impact Analysis: Determine the potential impact on business operations or data integrity.
- Effort Required: Assess the resources needed to remediate each issue.
For instance, a data breach risk should be prioritized over minor policy updates. During a recent audit, a company prioritized fixing a critical vulnerability, preventing a potential breach that could have led to severe financial and reputational damage. By strategically tackling high-risk vulnerabilities first, organizations can significantly enhance their cybersecurity posture.
Implementing Security Improvements
Developing an Action Plan
After the audit findings have been analyzed and vulnerabilities prioritized, it’s time to take actionable steps towards implementing security improvements. Developing a structured action plan is essential. This plan outlines the specific measures to address the identified weaknesses and ensures that everyone in the organization is on the same page.
An effective action plan should include:
- Specific Goals: Clearly define what needs to be accomplished. For example, “Update all software applications by Q2.”
- Assigned Responsibilities: Designate team members to take ownership of each task.
- Deadlines: Set realistic timelines for completion to keep the team accountable.
For instance, a small business I worked with established an action plan that included appointing a cybersecurity champion to oversee the implementation of changes. This individual was critical in coordinating efforts and rallying the team.
Enhancing Security Controls
Following the creation of an action plan, the focus shifts to enhancing security controls. This can involve several strategies to fortify the organization’s defenses.
Consider these enhancement tactics:
- Implementing Multi-Factor Authentication (MFA): Adding an extra layer of security can significantly reduce the risk of unauthorized access.
- Regular Updates and Patch Management: Ensure that all systems are regularly patched to fix any vulnerabilities.
- Employee Training: Conduct training sessions to educate employees about cybersecurity best practices and the importance of adhering to security protocols.
A company I’m familiar with saw a dramatic reduction in phishing attacks after rolling out comprehensive employee training. By actively enhancing security controls, organizations can create a robust cybersecurity framework that effectively mitigates risks and fortifies their defenses against future threats.
Monitoring and Maintaining Cybersecurity Post-Audit
Establishing Continuous Monitoring Practices
Once security improvements are implemented, the work doesn’t end there. Monitoring and maintaining cybersecurity is crucial to safeguarding an organization’s assets in the long run. Establishing continuous monitoring practices enables organizations to detect and respond to potential threats in real time.
Key components to consider when setting up monitoring practices include:
- Security Information and Event Management (SIEM) Solutions: Implement SIEM tools to gather and analyze security data from across the network, helping identify anomalies.
- Network Traffic Monitoring: Use tools to scrutinize network traffic for suspicious activity or patterns that could indicate a breach.
- Incident Response Plans: Ensure your team is prepared with a clear plan for responding to security incidents swiftly and effectively.
A colleague of mine shared their experience where, after adopting continuous monitoring, they were alerted to unusual login attempts, which allowed them to avert a potential breach. Being proactive is undeniably crucial.
Conducting Periodic Security Reviews
In addition to continuous monitoring, conducting periodic security reviews is essential. These reviews, typically scheduled quarterly or biannually, assess the overall effectiveness of security measures and provide opportunities to adapt to evolving threats.
During a security review, organizations should:
- Reassess Vulnerabilities: Evaluate previous vulnerabilities to check if they have been adequately addressed.
- Update Security Policies: Revise security policies as needed based on current risk assessments and emerging technologies.
- Engage Employees: Reiterate cybersecurity training and gather feedback from employees about new threats they may have encountered.
Constant vigilance, like performing periodic reviews, enables organizations to stay one step ahead of cyber threats, ultimately creating a resilient cybersecurity landscape that evolves with the ever-changing digital environment.

Reporting and Documentation
Compiling Audit Reports
After the dust has settled from implementing security improvements and conducting periodic reviews, it’s time to focus on reporting and documentation. Compiling audit reports is a critical part of this process, as these documents serve as a formal record of the entire audit lifecycle.
An effective audit report typically includes:
- Executive Summary: A high-level overview of the audit, including purpose, key findings, and recommendations.
- Methodology: A description of the audit process and tools used.
- Findings: A detailed account of identified vulnerabilities, risks, and gaps discovered during the audit.
- Recommendations: Suggested actions to address the identified issues.
A friend of mine once participated in a cybersecurity audit where the compiled report proved invaluable during a board meeting. The well-structured audit report helped convey critical findings clearly and effectively, allowing the company to make informed decisions.
Documenting Audit Results and Actions Taken
In conjunction with compiling reports, documenting audit results and the actions taken is essential for ongoing accountability and improvement. This documentation should include:
- Action Plans: Detailed descriptions of the steps taken to mitigate identified vulnerabilities.
- Progress Updates: Regular updates on the status of remediation efforts, including any challenges faced.
- Follow-Up Reviews: Records of subsequent reviews to assess the effectiveness of the implemented actions.
For instance, by maintaining clear documentation, an organization can demonstrate compliance with industry regulations, which supports risk management efforts. Maintaining thorough records can also foster a culture of transparency and accountability, setting a strong precedent for future audits. Ultimately, effective reporting and documentation not only ensure that lessons are learned but also lay the groundwork for a more robust cybersecurity posture moving forward.

