Introduction
Understanding Cyber Threats
In today’s digital landscape, the prevalence of cyber threats has reached alarming proportions. Businesses, regardless of size, are constantly faced with potential security breaches that can compromise sensitive information. These threats can originate from various sources, including:
- Hackers exploiting system vulnerabilities
- Insider threats where employees inadvertently (or deliberately) expose data
- Ransomware that holds critical files hostage until a payment is made
As exemplified by high-profile breaches in recent years, the fallout from a cyberattack can be catastrophic, leading to significant financial losses and reputational damage.
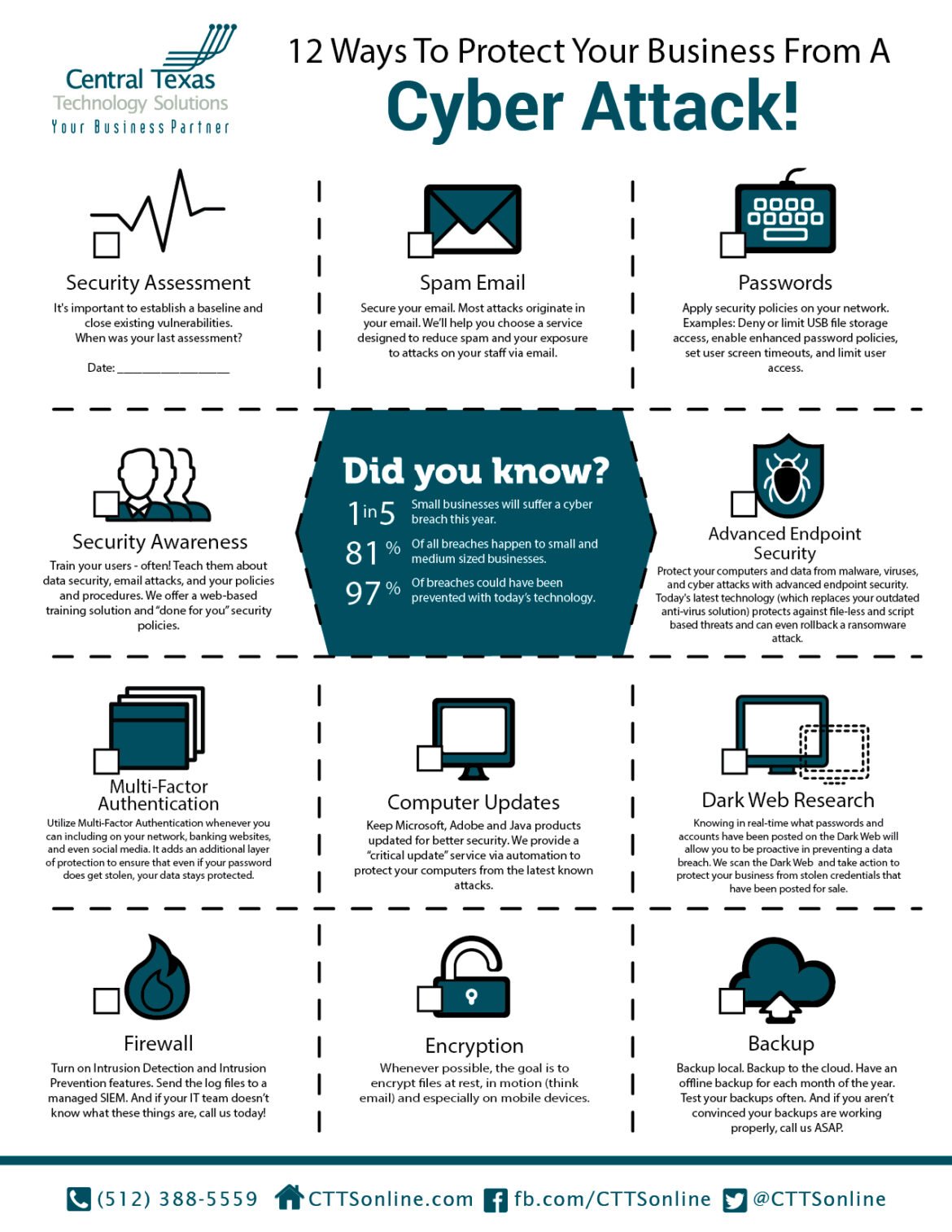
Importance of Cybersecurity for Businesses
Given these risks, cybersecurity must be a top priority for businesses. An effective cybersecurity strategy not only serves as a safeguard but also enhances customer trust and loyalty. Investing in robust security measures can help businesses:
- Protect sensitive data such as customer information and financial records
- Minimize downtime in the event of a breach
- Comply with regulations that mandate data protection measures
In a world where cyber threats are ever-evolving, being proactive about cybersecurity is no longer optional; it’s essential for business survival. This is where TECHFACK comes into play—offering insights and solutions that equip businesses to enhance their cybersecurity posture effectively.
Types of Cyber Threats
Malware Attacks
Malware attacks represent one of the most common and dangerous forms of cyber threats. These malicious software programs can infiltrate systems without the user’s knowledge, leading to severe consequences. Types of malware include:
- Viruses: Harmful code that replicates itself to spread to other files.
- Trojan Horses: Deceptive software that appears harmless but is designed to cause harm once activated.
- Ransomware: Restricts access to files and demands payment for restoration.
Hearing about a friend’s recent malware experience underscores the importance of vigilance; their personal pictures were held hostage until a ransom was paid.
Phishing Attempts
Phishing attempts are another prevalent threat where attackers masquerade as trustworthy entities to steal sensitive information. These attempts often come in the form of emails or messages that may include:
- Deceptive links that lead to fake websites
- Urgent requests for personal information, mimicking legitimate institutions
For instance, a colleague once fell for a phishing email claiming to be from their bank, ultimately jeopardizing personal finances.
DDoS Attacks
Distributed Denial of Service (DDoS) attacks aim to overwhelm a target’s system, rendering it inoperable. These attacks can disrupt access to:
- Websites: Resulting in loss of revenue and customer trust.
- Online services: Causing significant downtime and frustration.
Just like an unexpected flood can cripple a road, a DDoS attack can halt business operations, leading to loss of productivity. Recognizing these threats is essential for any business looking to bolster its cybersecurity defenses. Engaging with resources like TECHFACK can provide valuable insights into safeguarding against such vulnerabilities.

Vulnerabilities in Business Systems
Outdated Software
One of the most significant vulnerabilities found in business systems is outdated software. Neglecting to update applications and operating systems invites numerous risks, such as:
- Security loopholes: Hackers can exploit known vulnerabilities.
- Compatibility issues: Outdated software may falter against newer systems.
A former coworker experienced this firsthand when her team’s outdated antivirus software failed to detect a malware attack, allowing it to wreak havoc on their network.
Weak Password Policies
Moreover, weak password policies present another critical vulnerability. Many businesses fall into the trap of allowing simple passwords, leading to increased susceptibility to breaches. Some common pitfalls include:
- Default passwords: Often overlooked upon setup.
- Reused passwords: Employees using the same credentials across multiple platforms.
A friend’s experience illustrates this: their account was easily compromised because they used the same password for both their work email and personal accounts.
Lack of Employee Training
Lastly, a lack of employee training can severely undermine a business’s cybersecurity measures. Without adequate education on best practices, employees may unknowingly contribute to vulnerabilities. Training should cover:
- Identifying phishing attempts: Recognizing signs of fake communications.
- Safe data handling: Understanding the importance of securing sensitive information.
For example, an employee in an organization I know clicked on a malicious link simply because they hadn’t received any training on cybersecurity awareness. Organizations like TECHFACK highlight the necessity of addressing these vulnerabilities to fortify defenses against cyber threats. By proactively tackling these weaknesses, businesses can create a more robust cybersecurity posture.
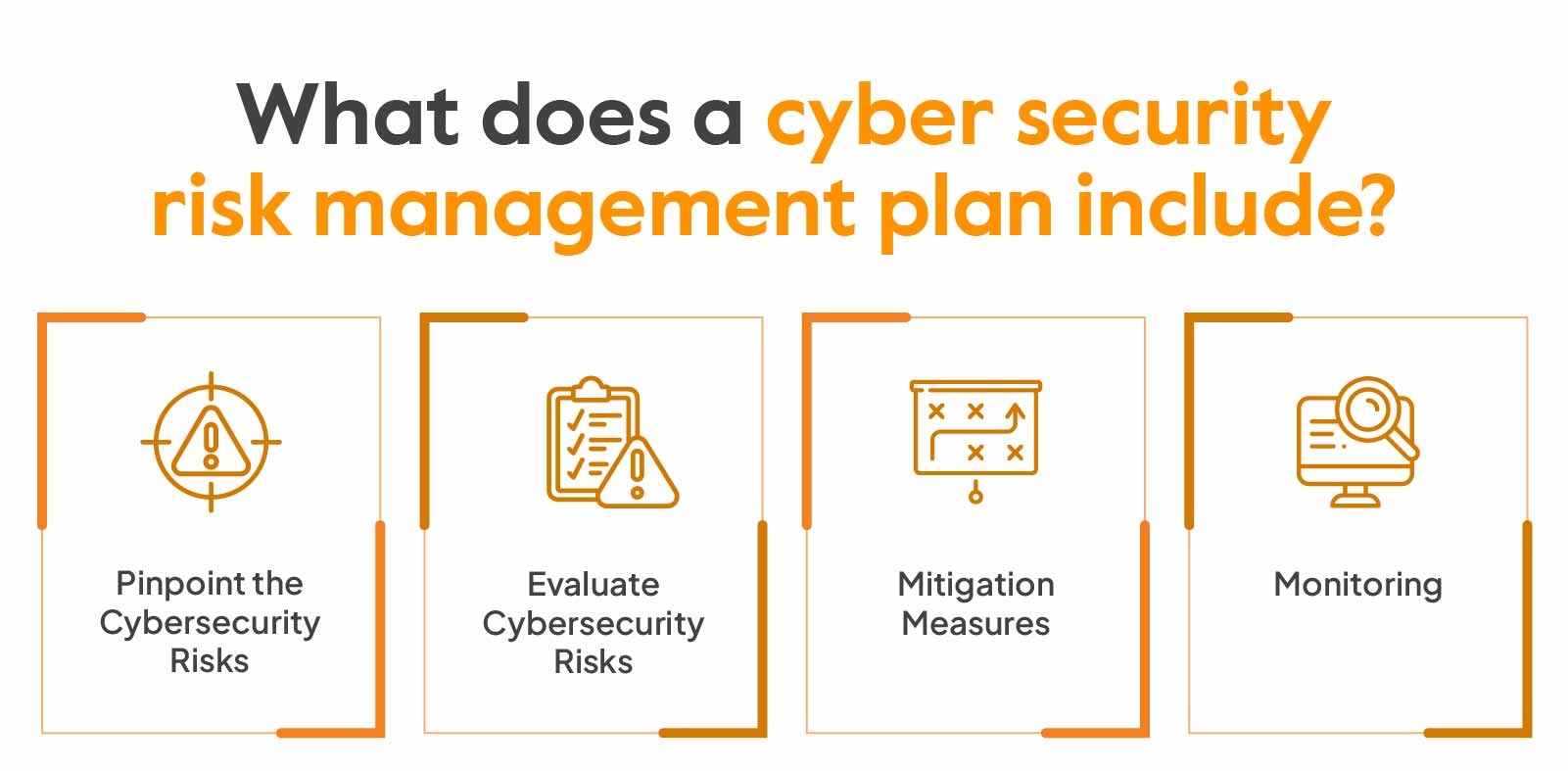
Assessing Cyber Risk
Conducting Security Audits
To effectively address vulnerabilities in business systems, assessing cyber risk is paramount. One of the foundational steps in this process is conducting security audits. These evaluations help organizations identify weaknesses in their cybersecurity framework by:
- Reviewing security policies: Ensuring they align with best practices.
- Testing systems: Evaluating defenses against potential threats.
I recall a case where a small business performed a security audit and uncovered outdated permissions that left sensitive files exposed. This proactive step not only enhanced their security posture but also safeguarded customer trust.
Identifying Critical Assets
The next step in assessing cyber risk involves identifying critical assets. Understanding what data and systems are essential for business operations allows organizations to prioritize their protection efforts. Key considerations include:
- Customer data: Personal information that must be safeguarded to comply with regulations.
- Intellectual property: Proprietary information that drives competitive advantage.
By mapping out these critical assets, businesses can allocate resources effectively and implement more stringent security measures. With the help of resources from TECHFACK, organizations can effectively navigate this process to bolster their defenses against cyber threats. In a rapidly evolving digital landscape, taking these precautionary measures is not just prudent—it’s essential for sustainability and growth.
Developing a Cybersecurity Plan
Creating Incident Response Procedures
Once vulnerabilities and critical assets have been assessed, the next crucial step is developing a comprehensive cybersecurity plan. A vital component of this plan is creating incident response procedures. These procedures outline the steps to take in the event of a cyber incident, aiming to minimize damage and restore operations quickly. Key elements to consider include:
- Defined roles: Assign responsibilities to team members for efficient communication and action.
- Incident classification: Establish criteria for identifying the severity of incidents.
- Response timelines: Create checklists for immediate actions to take.
I witnessed a local business recover swiftly from a breach because they had a well-documented incident response plan in place, allowing them to act decisively without panic.
Implementing Data Backup Systems
Equally important is implementing data backup systems. These systems ensure that critical information is regularly saved and can be restored in case of a cyber threat. Best practices for effective data backup include:
- Regular schedules: Automate backups to run at scheduled intervals.
- Off-site solutions: Store backups in a secure, off-site location or cloud-based service.
- Testing restore processes: Regularly test data restoration to ensure backups are reliable.
By adopting these protocols, organizations will bolster their resilience against cyber attacks. With guidance and support from resources like TECHFACK, businesses can develop a robust cybersecurity plan that not only protects their assets but also fosters confidence among stakeholders in navigating potential threats.
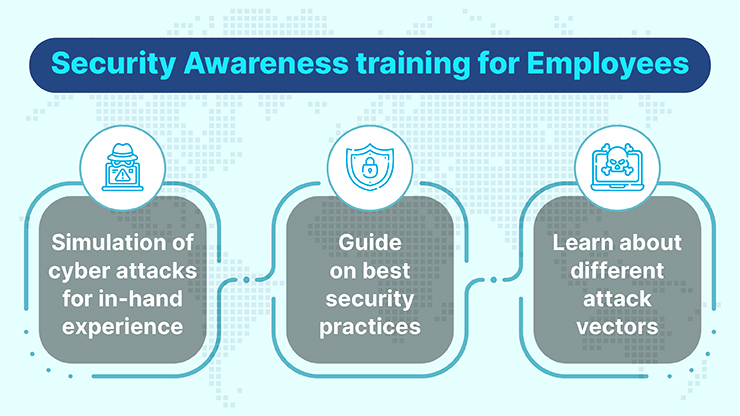
Employee Awareness and Training
Importance of Cybersecurity Training
After developing a robust cybersecurity plan, organizations must turn their focus to the human element—employees. Employee awareness and training are crucial in the fight against cyber threats. A well-informed workforce can make a significant difference in detecting and mitigating risks. For example, consider the tale of a startup that suffered a data breach due to an employee unwittingly downloading malware. Had that employee received proper training, the incident might have been prevented.
- Empower employees: Training equips staff with knowledge and tools to recognize threats.
- Reduce human error: Comprehensive training reduces mistakes that lead to security breaches.
Best Practices for Employees
To reinforce this learning, organizations should implement best practices for employees, such as:
- Regular training refreshers: Keep cybersecurity awareness top of mind.
- Phishing simulations: Conduct real-world tests to prepare employees for potential threats.
- Encourage reporting: Create a culture where employees feel comfortable reporting suspicious activities.
By prioritizing employee awareness and training, businesses not only strengthen their cybersecurity defenses but also foster a sense of shared responsibility. This is where organizations like TECHFACK come into play—providing tailored training solutions to ensure that every team member is equipped to protect against cyber threats effectively. Developing a culture of cybersecurity begins with informed and engaged employees, creating a more resilient organization overall.

Investing in Security Technologies
Firewalls and Antivirus Software
As organizations focus on bolstering their cybersecurity defenses through employee training, it’s equally important to invest in advanced security technologies. One of the primary layers of defense is the use of firewalls and antivirus software. Firewalls act as a barrier between a trusted internal network and untrusted external networks, monitoring incoming and outgoing traffic. Key benefits include:
- Blocking unauthorized access: Preventing threats before they reach the network.
- Monitoring activity: Keeping an eye on suspicious behavior.
Antivirus software complements firewalls by detecting and eliminating malware threats. A friend of mine who leads an IT department emphasizes the importance of regularly updating antivirus solutions to ensure they recognize the latest malware.
Encryption Tools
In addition to these technologies, encryption tools play a pivotal role in securing sensitive data. Encryption transforms plaintext into unreadable code, making it difficult for unauthorized users to gain access. Important aspects of encryption include:
- Data at rest: Encrypting files on servers and workstations.
- Data in transit: Securing information sent over networks.
Consider a scenario where a company’s client data is encrypted; even if a breach occurs, the information remains unintelligible to cybercriminals. By investing in firewalls, antivirus software, and encryption tools, businesses enhance their defense mechanisms and protect their most valuable assets. Resources like TECHFACK provide insights into these technologies, ensuring organizations make informed decisions that bolster their cybersecurity posture. Ultimately, the right investment in security technologies will significantly reduce the likelihood of data breaches and build trust with stakeholders.

Collaboration and Information Sharing
Industry Partnerships
As businesses continue to invest in security technologies, another crucial aspect of a robust cybersecurity strategy is collaboration and information sharing. One effective approach is forming industry partnerships. By collaborating with other organizations, companies can enhance their overall cybersecurity posture through shared knowledge and resources. Benefits of forming these partnerships include:
- Access to threat intelligence: Staying informed about emerging threats that affect the industry.
- Shared best practices: Learning from the successes and failures of others.
For instance, I recently attended a cybersecurity conference where businesses shared their experiences with recent attacks and recovery strategies. This kind of open dialogue enables organizations to preemptively safeguard their networks.
Reporting Security Incidents
Additionally, having a clear process for reporting security incidents can significantly strengthen an organization’s defensive capabilities. Prompt reporting allows companies to:
- Minimize damage: Quick action can prevent the spread of an incident.
- Enhance learning: Documenting incidents provides valuable data for future prevention efforts.
Encouraging a culture where reporting is seen positively helps create an alert workforce. By prioritizing collaboration and information sharing through industry partnerships and effective incident reporting mechanisms, organizations can foster a more resilient cybersecurity environment. Partnering with resources like TECHFACK can facilitate these efforts, providing valuable insights to navigate the complexities of cybersecurity collaboratively. Ultimately, a unified approach enhances protection for everyone involved.

Continuous Monitoring and Updates
Patch Management
Continuing from the importance of collaboration and information sharing, another critical aspect of maintaining a strong cybersecurity posture is continuous monitoring and updates. One key element of this process is patch management. Software developers frequently release patches to fix vulnerabilities and improve functionality. Keeping systems up-to-date through effective patch management ensures that businesses safeguard themselves against potential exploits. Important steps include:
- Regular assessments: Evaluating software to determine which programs need updates.
- Automated updates when feasible: Streamlining the process to ensure timely application of patches.
I remember a scenario where a delayed patch led a local business to suffer a serious data breach, highlighting the necessity of vigilance in this area.
Security Policy Review
In addition to patch management, conducting regular security policy reviews is essential for adapting to evolving threats. Policies should reflect current best practices and align with organizational goals. Considerations for a robust policy review include:
- Assessing existing protocols: Ensuring they’re effective and relevant.
- Incorporating employee feedback: Gaining insights from those on the front lines.
By actively engaging in continuous monitoring and updates—through patch management and regular security policy reviews—organizations can significantly reduce their risk exposure. Partnering with experts like TECHFACK can facilitate a comprehensive review process, ultimately leading to stronger defenses that adapt to the ever-changing cybersecurity landscape. In a world where threats are persistent, staying ahead through continuous vigilance is not merely advantageous; it’s essential for ongoing success.
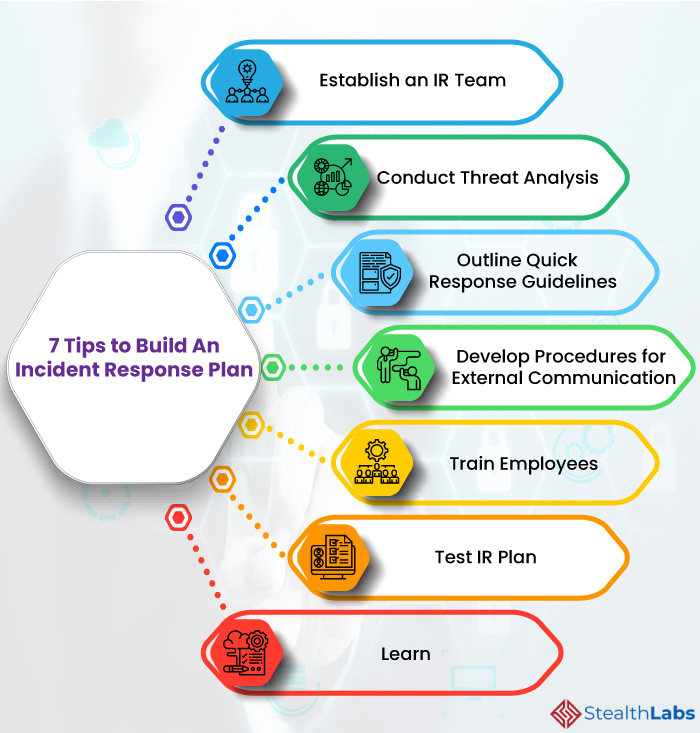
Incident Response and Recovery
Containment and Mitigation
Building on the theme of continuous monitoring, an effective cybersecurity strategy must also include a well-defined incident response and recovery plan. When a cyber incident occurs, the first step is containment and mitigation. This process aims to limit the damage and prevent further breaches. Key actions include:
- Isolating affected systems: Disconnecting impacted devices from the network to halt the spread.
- Identifying the entry point: Understanding how the breach occurred can help inform future defenses.
I recall a situation where a friend’s company faced a ransomware attack. Their immediate response to isolate systems allowed the IT team to control the situation before it escalated further, mitigating potential losses.
Business Continuity Planning
Beyond addressing immediate threats, robust business continuity planning is essential for long-term resilience. This involves creating comprehensive strategies to ensure that essential operations can continue, even during disruptions. Important components of business continuity planning include:
- Alternative operational strategies: Developing plans that allow functions to continue from alternative locations or through remote work.
- Regular testing of plans: Conducting drills to evaluate the effectiveness of the business continuity strategies.
By incorporating both containment and mitigation strategies alongside effective business continuity planning, organizations can recover swiftly from incidents and resume normal operations. With the support of resources like TECHFACK to guide the process, businesses can reinforce their defenses and be better prepared for future cyber threats, ensuring long-term stability and confidence. Ultimately, a proactive approach to incident response lays the groundwork for a resilient organizational culture.