Overview of GDPR and Cybersecurity
Definition of GDPR and its Scope
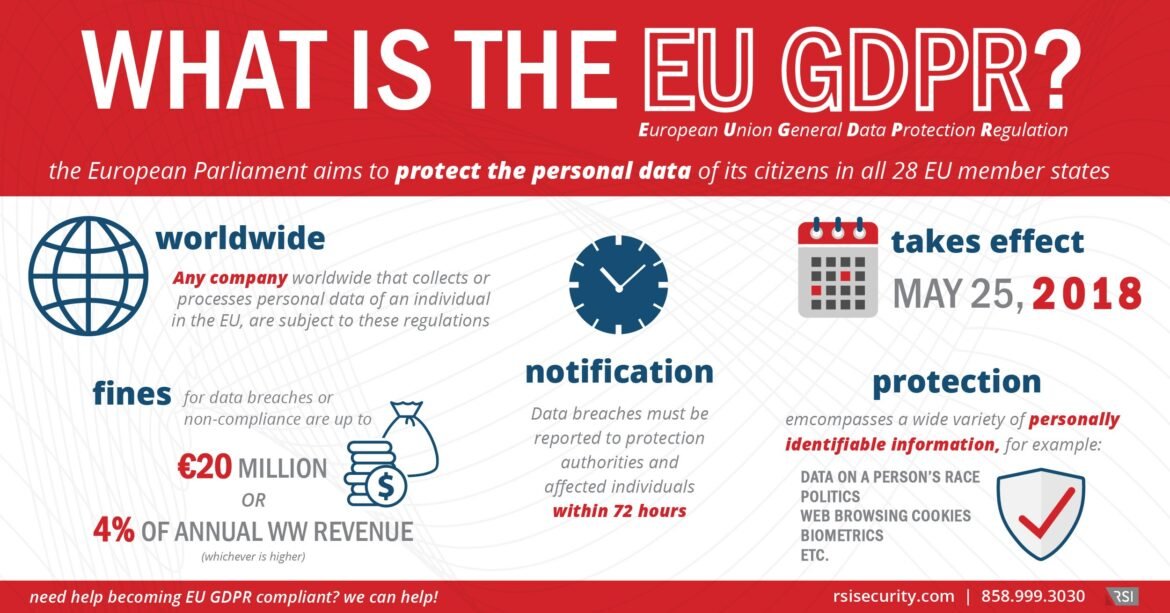
The General Data Protection Regulation (GDPR) is a robust legal framework established by the European Union in 2018, designed to govern the handling of personal data. It sets forth obligations for organizations that collect, process, or store personal data of EU residents, regardless of their location. Here’s a snapshot of GDPR’s core components:
- Data Protection Rights: Individuals are granted enhanced rights over their data, including the right to access, correct, or delete their information.
- Scope: GDPR applies to any organization, inside or outside the EU, that processes data belonging to EU citizens.
- Penalties: Non-compliance can lead to significant financial penalties, reaching up to 4% of a company’s global turnover or €20 million, whichever is higher.
This sweeping legislation highlights the importance of respecting individuals’ privacy while operating in a digital landscape increasingly vulnerable to breaches.
Importance of Cybersecurity in the Context of GDPR
Cybersecurity plays a critical role in ensuring compliance with GDPR. Think about the trust customers place in companies to handle their personal data responsibly. When organizations fail to protect this data, it not only leads to regulatory fines but can also damage their reputation.
Key points on the importance of cybersecurity include:
- Preventing Data Breaches: Robust cybersecurity measures safeguard against unauthorized access.
- Ensuring Customer Trust: Clients are more likely to engage with businesses that demonstrate strong data protection practices.
- Mitigating Risks: Cybersecurity protects organizations from emerging threats, fostering a secure environment for personal data processing.
As such, effective cybersecurity is not just a technical requirement but a pivotal aspect of GDPR compliance, ensuring individuals’ rights are protected while maintaining brand integrity in the digital age.

Understanding GDPR Regulations
Principles of GDPR Compliance
Navigating the realm of GDPR requires a solid grasp of its core principles, which serve as the foundation for compliance. Understanding these principles is essential for organizations looking to build a culture of data protection.
- Lawfulness, Fairness, and Transparency: Organizations must have a legal basis for processing personal data. This principle emphasizes honesty in how data is collected and used. For example, if a subscriber signs up for a newsletter, they should know what their data will be used for upfront.
- Purpose Limitation and Data Minimization: Organizations should only collect data that is strictly necessary for the given purpose. For instance, if a business collects customer data for order processing, it shouldn’t retain it indefinitely once the order is fulfilled.
Accuracy and Storage Limitation
Accuracy implies that data must be accurate and kept up-to-date, to avoid decisions based on faulty information. A practice that many companies adopt is regular data audits to ensure accuracy.
- Storage Limitation: Personal data should not be stored longer than necessary. This can be implemented through automated data deletion processes or policies.
Integrity and Confidentiality
This principle stresses the need for appropriate security measures to protect personal data. Organizations must implement technical and organizational security measures to avoid data breaches and unauthorized access.
Accountability and Privacy by Design
Organizations must not only comply with the regulations but also demonstrate that they do. This involves documenting data processes, ensuring staff training, and incorporating data protection into business operations from the outset.
By embracing these principles, organizations can not only meet legal obligations but also foster trust with their clients in an age where data security is paramount.

Relationship Between GDPR and Cybersecurity
How GDPR Impacts Cybersecurity Measures
As organizations navigate the complexities of GDPR, the interconnection between these regulations and cybersecurity measures becomes increasingly evident. GDPR mandates specific cybersecurity protocols to protect personal data, thereby placing the onus on businesses to strengthen their defenses.
Here’s how GDPR impacts cybersecurity strategies:
- Data Protection by Design and by Default: Organizations must integrate data protection into their operations and systems right from the outset. This means adopting secure software development practices, conducting risk assessments, and evaluating third-party service providers to mitigate vulnerabilities.
- Incident Response Plans: GDPR requires organizations to have clear protocols for notifying authorities and affected individuals of data breaches. This necessitates well-structured incident response plans that are regularly updated and tested.
- Access Controls: GDPR pushes businesses to restrict access to personal data to only those who need it for legitimate purposes, thus encouraging robust access control mechanisms.
Ensuring Data Security and Privacy under GDPR
To ensure compliance, organizations must adopt a holistic approach to data security. Here are actionable strategies:
- Regular Security Audits: Conducting periodic reviews of data management practices helps identify vulnerabilities and ensure compliance with GDPR.
- Employee Training: Creating awareness among staff about their role in data security is essential. For instance, phishing simulations can boost vigilance against potential attacks.
- Implementing Encryption: Utilizing encryption for sensitive data adds another layer of protection, making it difficult for unauthorized users to access meaningful information in the event of a breach.
By understanding and implementing these critical cybersecurity measures, organizations will not only comply with GDPR but will also build a more secure environment for personal data, thereby enhancing consumer confidence.

Common Cybersecurity Threats in the GDPR Framework
Phishing Attacks and Data Breaches
As organizations work to fortify their defenses under the GDPR framework, it’s crucial to understand the common cybersecurity threats lurking in the shadows. One of the most pervasive threats is phishing attacks, where cybercriminals attempt to trick individuals into revealing sensitive information. For example, an employee might receive an email that appears to be from a trusted source, prompting them to share login credentials.
- Data Breaches: When these attacks succeed, they can lead to significant data breaches, resulting in unauthorized access to personal data. GDPR mandates that organizations report such breaches, emphasizing the need for vigilant monitoring and quick response.
Ransomware and Malware Threats
Another formidable foe in the cybersecurity arena is ransomware. This malicious software can lock organizations out of their own data, demanding a ransom for access. The aftermath of a ransomware attack can be costly—not just in terms of the ransom itself but also regarding recovery efforts and reputational damage.
- Malware Variants: Organizations must also remain cautious of other malware variants designed to steal data or disrupt services. Regular updates and comprehensive security protocols can help mitigate these risks.
Social Engineering and Insider Threats
Social engineering attacks are less about technology and more about human psychology. Attackers often exploit employees’ trust or naivete to gain access to sensitive information. Similarly, insider threats can arise from disgruntled employees or careless data handling, leading to unintentional exposure of personal data.
To combat these threats:
- Awareness Training: Regular training sessions can educate employees on recognizing potential social engineering attempts and improving overall security mindfulness.
- Access Reviews: Conducting periodic access reviews to ensure that only authorized personnel have access to sensitive data can minimize the risk of insider threats.
Understanding these prevalent threats is crucial for organizations aiming to build a robust cybersecurity posture while remaining compliant with GDPR. By addressing these vulnerabilities, companies can better protect both their data and their customers’ trust.

Compliance Challenges and Solutions
Challenges in Aligning GDPR and Cybersecurity
Navigating the intersection of GDPR compliance and cybersecurity can present several challenges for organizations. Understanding these hurdles is essential for creating effective strategies moving forward.
One major challenge is the complexity of regulatory requirements. Organizations often struggle to interpret the intricacies of GDPR while simultaneously implementing robust cybersecurity measures. For example, small to medium-sized businesses may lack the resources to maintain both compliance and security infrastructure, resulting in gaps in protection.
- Resource Allocation: Balancing budget constraints with the need for advanced cybersecurity solutions can often lead to underfunded initiatives. This discrepancy can expose organizations to risks that GDPR was designed to mitigate.
- Cultural Shift: Adopting a mindset focused on data protection can be a challenge, requiring significant education and training efforts to ensure every employee understands their role in maintaining compliance.
Best Practices for Overcoming Compliance Hurdles
Fortunately, there are strategies organizations can employ to address these challenges effectively:
- Conduct Comprehensive Audits: Regular audits that assess both compliance with GDPR and the effectiveness of cybersecurity measures can identify gaps and areas for improvement.
- Incorporate Data Protection Training: Implementing training sessions to educate employees about GDPR requirements and best practices enhances understanding and accountability.
- Utilize Technology Solutions: Invest in comprehensive security tools that integrate compliance management with cybersecurity. Solutions such as data loss prevention (DLP) and encryption software can significantly enhance protection.
- Foster Collaboration: Encourage collaboration between compliance and IT teams, ensuring that both areas work in tandem to align efforts and share insights.
By embracing these best practices, organizations can effectively tackle compliance challenges, ensuring a robust cybersecurity posture that aligns seamlessly with the principles of GDPR while safeguarding personal data.

Role of Data Protection Officers (DPOs) in GDPR and Cybersecurity
Responsibilities of DPOs in Ensuring Compliance
In the ever-evolving landscape of data protection, the role of Data Protection Officers (DPOs) has become paramount. With GDPR imposing stringent requirements, DPOs serve as the cornerstone for organizations striving to achieve compliance. Their responsibilities encompass a wide range of critical activities:
- Monitoring Compliance: DPOs are tasked with overseeing the implementation of GDPR policies across the organization, ensuring that processes are in place to safeguard personal data.
- Conducting Data Protection Impact Assessments (DPIAs): They evaluate potential risks associated with data processing activities, providing insights on how to mitigate those risks effectively.
- Serving as a Liaison: DPOs act as the main point of contact for data subjects, supervisory authorities, and internal teams, facilitating communication and transparency.
Their role is not just limited to legal compliance; it extends to fostering a culture of data protection throughout the organization.
Collaborating with IT and Security Teams for Effective Data Protection
Collaboration is key in achieving robust data protection, and DPOs play a vital role in bridging the gap between compliance and cybersecurity teams. By working alongside IT and security experts, DPOs can implement comprehensive strategies that encompass both legal and technological perspectives.
- Shared Knowledge and Expertise: Regular meetings between DPOs and IT security teams can identify emerging threats and address vulnerabilities effectively.
- Integration of Security Measures: DPOs can ensure that data protection considerations are included in all technology deployments, such as encryption and secure access protocols.
- Continuous Training: Collaborating to provide ongoing training ensures that all employees are consistently up-to-date on data protection practices and cybersecurity essentials.
By fostering strong partnerships, DPOs help create a proactive environment where compliance and cybersecurity work together seamlessly, ultimately protecting both organizational integrity and individual privacy rights.

Impact of GDPR on Global Cybersecurity Landscape
International Data Transfers and Cross-Border Data Flows
The implementation of GDPR has not only transformed data protection within the European Union but has also significantly influenced the global cybersecurity landscape, particularly concerning international data transfers. Organizations that operate across borders must now navigate strict regulations regarding the transfer of personal data outside the EU.
- Adequacy Decisions: GDPR stipulates that countries receiving European data must ensure adequate data protection standards. This has led many organizations to re-evaluate and, in some cases, restructure their data flow processes to comply with these regulations.
- Standard Contractual Clauses (SCCs): For companies unable to operate under adequacy decisions, SCCs are often deployed to ensure that data transferred internationally achieves equivalent protection. They serve as a safeguard, ensuring that personal data remains protected even when moved across borders.
This emphasis on secure data transfers reflects a broader global trend towards enhanced data protection practices.
Influence of GDPR Standards on Global Data Protection
Beyond EU borders, GDPR has set a benchmark for data protection standards worldwide. Organizations around the globe are increasingly adopting principles derived from GDPR in an effort to bolster their privacy and security practices.
- Harmonization of Regulations: Numerous jurisdictions, including Brazil and California, have begun implementing data protection laws that echo GDPR’s key principles, fostering a global landscape where data privacy is prioritized.
- Corporate Responsibility: The global reach of GDPR has prompted businesses to take a proactive stance on data security. Companies now recognize the importance of demonstrating their commitment to data protection to maintain customer trust and meet international standards.
As such, GDPR has emerged as a pivotal reference point in the global discourse on data protection, encouraging organizations everywhere to enhance their cybersecurity practices and prioritize the safeguarding of personal data.

Recommendations for Strengthening GDPR and Cybersecurity Measures
Regular Security Audits and Risk Assessments
To maintain robust GDPR compliance and reinforce cybersecurity measures, organizations should prioritize regular security audits and risk assessments. These activities are not only essential for identifying vulnerabilities but also for ensuring adherence to data protection standards.
- Comprehensive Evaluations: Conducting annual or biannual audits helps organizations pinpoint weaknesses in their data handling practices. For instance, while reviewing access logs, a company might discover unauthorized access attempts that need immediate attention.
- Dynamic Risk Assessments: By continuously assessing potential risks associated with new technologies or processes, businesses can proactively adapt their strategies to combat emerging threats. This is particularly important as cyber threats are constantly evolving.
- Documentation: Keeping detailed records of audits and risk assessments can demonstrate due diligence and compliance with GDPR, ultimately safeguarding organizations against regulatory scrutiny.
Employee Training and Awareness Programs
Equipping employees with the knowledge to recognize and respond to cybersecurity threats is vital in fostering a culture of data protection within an organization.
- Regular Training Sessions: Implementing mandatory training workshops can familiarize staff with the latest GDPR regulations, phishing tactics, and best data handling practices.
- Engaging Materials: Using interactive materials, such as quizzes and scenario-based training, can make sessions more engaging and help employees better retain information. For instance, a simulated phishing attack might help staff identify suspicious emails in real-time.
- Ongoing Awareness Campaigns: Periodic reminders through newsletters or dedicated intranet sections can keep data protection top of mind, highlighting new trends and threats.
By investing in regular audits and robust employee training programs, organizations can create a proactive data protection environment that not only achieves GDPR compliance but bolsters overall cybersecurity resilience. This holistic approach helps secure sensitive data while building a culture of awareness among all employees.

Conclusion and Future Outlook
Recap of Key Points on GDPR and Cybersecurity
As we’ve explored throughout this blog, the relationship between GDPR and cybersecurity is intricate and ever-evolving. The importance of maintaining compliance with GDPR is essential not only for legal adherence but also for building trust with customers. Key points to remember include:
- GDPR’s Impact on Data Handling: It requires organizations to approach data protection proactively, embedding privacy measures into their operations.
- Role of Cybersecurity: Robust cybersecurity measures are essential for safeguarding personal data and minimizing risks associated with breaches.
- DPOs and Collaboration: The role of Data Protection Officers in ensuring compliance and working together with IT teams is critical for a well-rounded approach to data security.
Emerging Trends and Evolving Regulatory Landscape
Looking ahead, it’s clear that the landscape of data protection and cybersecurity will continue to evolve. Some emerging trends to watch for include:
- Artificial Intelligence (AI) in Compliance: Organizations may increasingly leverage AI for automating compliance processes and enhancing data security measures.
- Global Data Protection Standards: As more countries adopt GDPR-like regulations, organizations will need to prepare for a more complex compliance environment that respects diverse legal frameworks.
- Increased Focus on Privacy-Enhancing Technologies: Innovations aimed at enhancing data privacy, such as advanced encryption techniques and decentralized data storage solutions, will gain traction.
In conclusion, navigating the realms of GDPR and cybersecurity requires a proactive and flexible approach. Organizations that prioritize compliance and invest in security measures will not only protect personal data but will also foster trust and goodwill with their clients, ultimately paving the way for sustainable growth in the digital age. Embracing this journey will be essential as the regulatory landscape continues to unfold.