Overview of Cybersecurity Software
Definition of Cybersecurity Software
Cybersecurity software refers to a range of tools and solutions designed to protect systems, networks, and data from cyber threats. These applications serve as the first line of defense against a multitude of online vulnerabilities, including malware, phishing attacks, and data breaches.
In essence, cybersecurity software encompasses several types of programs, including:
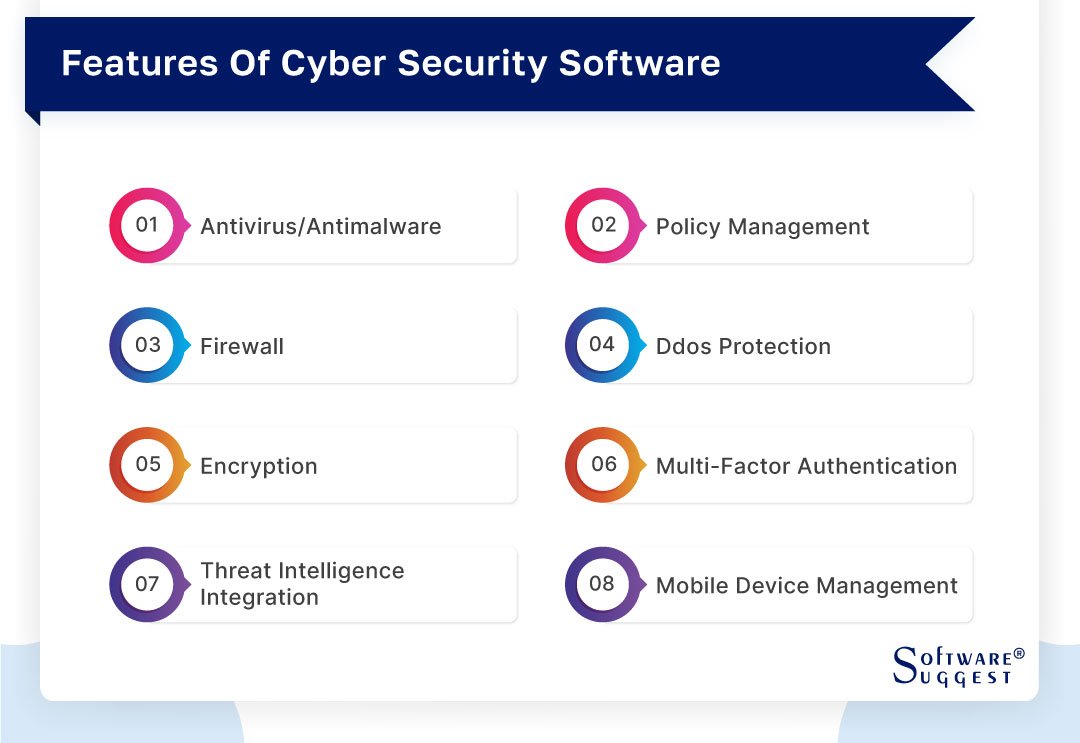
- Antivirus Software: Detects and removes malicious software.
- Firewall Solutions: Monitors and controls incoming and outgoing network traffic.
- Intrusion Detection Systems (IDS): Identifies suspicious activity within a network.
- Data Loss Prevention (DLP): Protects sensitive data from unauthorized access or breaches.
By integrating these tools, organizations can create a robust security framework that minimizes risks associated with cyberattacks.
Importance of Cybersecurity in Today’s Digital World
In our increasingly digital society, the significance of cybersecurity cannot be overstated. With a staggering number of devices connected to the internet, the potential for cyber threats has grown exponentially. Consider the following:
- Data Breaches: In 2023, millions of records were exposed due to inadequate security measures.
- Financial Losses: Businesses lost an estimated $6 trillion globally due to cybercrime over the past year.
- Reputation Damage: A significant breach can tarnish a company’s reputation, causing customers to lose trust.
A personal anecdote highlights the necessity of cybersecurity. Imagine a small business owner who trusted their outdated software to protect against cyber risks. After experiencing a devastating data breach, not only did they lose significant financial resources, but their loyal customer base dwindled as trust eroded.
This demonstrates that investing in robust cybersecurity software is no longer an option but a requirement for securing sensitive information and maintaining organizational integrity.

Key Features to Consider in Cybersecurity Software
Real-time Threat Detection
When evaluating cybersecurity software, one of the pivotal features to consider is real-time threat detection. This functionality continuously scans networks for potential threats, providing immediate alerts and allowing for quick responses. Without this feature, malicious activities could go unnoticed, leading to serious data breaches. A friend of mine, a network administrator, attributed the survival of his company through a recent cyberattack to their effective real-time detection system, which alerted them right before a major breach could occur.
Data Encryption Capabilities
Next on the list is data encryption capabilities. Encryption transforms sensitive data into unreadable formats that can only be deciphered with the correct key. This feature is crucial for protecting confidential information, especially for businesses handling personal data. For instance, a healthcare provider I know switched to a new cybersecurity solution that included strong encryption. As a result, they were able to bolster patient confidentiality and comply with regulatory mandates.
Multi-factor Authentication
Multi-factor authentication (MFA) is an essential feature that adds an extra layer of security, requiring users to verify their identity through multiple means. Simple username and password combinations are often inadequate; MFA can include SMS codes, fingerprint scans, or facial recognition. When implementing MFA, users feel more secure knowing their accounts are better protected.
Firewall Protection
Firewall protection acts as a barrier between your network and potential intruders, monitoring incoming and outgoing traffic. An effective firewall can prevent unauthorized access, making it a cornerstone of cybersecurity software.
Automatic Updates and Patch Management
The feature of automatic updates and patch management ensures your software is always up-to-date with the latest security enhancements. Cyber threats constantly evolve, and regular updates are necessary to protect against them. Outdated software is one of the leading causes of security breaches.
User-Friendly Interface
Lastly, a user-friendly interface is vital for ensuring that all team members can effectively use the software. Complex systems can lead to errors and inefficiencies, making training a significant consideration. A colleague shared how their new cybersecurity solution significantly improved productivity due to its intuitive layout, allowing the team to focus on defense rather than deciphering complicated software features.
Each of these key features plays a critical role in safeguarding organizational data, making them indispensable when evaluating the best cybersecurity software.

Factors to Evaluate When Choosing Cybersecurity Software
Compatibility with Existing Systems
As organizations explore options for cybersecurity software, compatibility with existing systems should be at the forefront of their evaluation. Integrating new software with legacy systems can often present a significant challenge. A colleague learned this the hard way when his company purchased a robust cybersecurity solution that turned out to be incompatible with their outdated infrastructure. The result? A complicated and costly overhaul of their entire system. To avoid such headaches, ensure the software can seamlessly integrate with your current setup before committing.
Scalability
Another vital factor is scalability. As a business grows, its cybersecurity needs will evolve. It’s important to choose software that can expand alongside your organization. For example, a startup I consulted for initially needed minimal protection, but as they rapidly scaled, they required more comprehensive cybersecurity solutions. They wisely selected a software option that allowed them to easily upgrade their services and add features as needed, saving both time and money in the long run.
Cost and Licensing Options
Cost and licensing options are also key considerations. Cybersecurity software can range from budget-friendly solutions to premium services with extensive features. It’s essential to evaluate not just the upfront costs but also ongoing expenses and licensing structures. Many companies offer tiered pricing models based on the number of users or features; understanding these can help you select an option that fits your budget without sacrificing security.
Customer Support and Service Level Agreements
Finally, consider customer support and service level agreements (SLAs). In the world of cybersecurity, timely support can make all the difference. A friend faced a ransomware attack late at night, and their quick-thinking response was thwarted by poor customer support from their cybersecurity vendor. Thoroughly review the support options, response times, and SLAs to ensure you’re making the right choice. Solid support can mean the difference between a minor inconvenience and a major disaster.
By carefully evaluating these factors, organizations can choose the cybersecurity software that best suits their needs while ensuring protection against ever-evolving threats.
Comparison of Top Cybersecurity Software Solutions
Analysis of Features and Benefits
As organizations delve into the cybersecurity landscape, conducting a thorough comparison of top cybersecurity software solutions is essential. Many options in the market offer a variety of features tailored to different needs. For example:
- Software A: Provides comprehensive real-time threat detection, advanced data encryption, and multi-factor authentication—all essential for robust security.
- Software B: Focuses on user-friendly interfaces and strong firewall protection, making it ideal for smaller businesses with limited IT resources.
- Software C: Highlights exceptional customer support and automatic updates, which are crucial for organizations that prioritize up-to-date security measures.
When assessing these features, it’s important to align them with your organization’s specific needs and potential threat landscape.
Pricing Models
Next, consider the pricing models of different cybersecurity solutions. The costs can vary widely based on features, company size, and licensing agreements. Here are some common models:
- Subscription-Based Pricing: Provides ongoing updates and support (usually billed monthly or annually).
- One-time License Fee: A larger upfront cost with potentially higher long-term maintenance expenses.
- Freemium Models: Offering basic features for free while charging for advanced functionalities.
For example, I once assisted a nonprofit organization that benefited from a freemium model. They enjoyed basic protection and later upgraded to a paid plan as their needs expanded.
User Reviews and Ratings
Lastly, don’t underestimate the value of user reviews and ratings when making your choice. User feedback can provide insights into real-world performance and customer satisfaction. Websites like G2 and Capterra can be helpful, as they aggregate ratings and detailed user experiences.
- Look for common praises or complaints about reliability and effectiveness.
- Note responses to customer support inquiries, which can also indicate how responsive a vendor is in emergencies.
By carefully analyzing features, pricing models, and user feedback, organizations can identify the cybersecurity software solution that aligns perfectly with their requirements, paving the way for a secure digital environment.

Case Studies: Successful Implementation of Cybersecurity Software
Company A: Implementing Software X
To truly understand the impact of cybersecurity software, examining real-world examples can provide invaluable insights. Let’s explore Company A, a mid-sized financial institution that recently decided to implement Software X. Faced with growing cyber threats, they aimed to enhance their security posture significantly.
After a thorough evaluation, they selected Software X for its robust features, including:
- Real-time threat detection: Ensured immediate alerts on suspicious activities.
- User-friendly interface: Allowed the IT team to monitor systems without extensive training.
- Strong customer support: Guaranteed assistance during emergencies.
Once implemented, the company reported a 60% reduction in phishing attempts and successful threat mitigation within minutes of detection. Employees felt more secure, resulting in improved productivity. The implementation of Software X not only protected sensitive financial data but also fortified the organization’s reputation in the industry.
Company B: Impact of Software Y on Data Security
Another noteworthy example is Company B, a healthcare provider that adopted Software Y to comply with stringent regulations while ensuring patient data privacy. The unique features of Software Y that caught their attention included:
- Automatic updates and patch management: Keeping the software up-to-date without manual intervention.
- Data encryption capabilities: Protecting sensitive patient records from unauthorized access.
After integrating Software Y into their infrastructure, Company B experienced a notable transformation. They achieved compliance with federal regulations, minimizing the risk of costly penalties. Additionally, patient trust skyrocketed, as many patients appreciated their commitment to data security.
A firsthand account reveals that staff members felt empowered by the software’s seamless integration, allowing them to focus on patient care rather than worrying about data breaches.
These case studies illustrate how effective cybersecurity software implementation not only mitigates risks but also enhances overall organizational efficiency and reputation. Organizations looking to bolster their cybersecurity arsenal should draw inspiration from these success stories as they explore their options.

Future Trends in Cybersecurity Software Development
Artificial Intelligence and Machine Learning Integration
As the cybersecurity landscape evolves, artificial intelligence (AI) and machine learning (ML) are at the forefront of future software development. These technologies enable organizations to predict potential threats by analyzing patterns and behaviors, making them incredibly valuable for real-time threat detection. For instance, a close associate of mine in the tech sector recently shared how their company implemented an AI-based system that could autonomously identify and neutralize cyber threats. The result? A significant reduction in response time and the ability to handle an increased volume of attacks without overwhelming their security team.
Some benefits of AI and ML in cybersecurity include:
- Enhanced threat detection: AI algorithms can learn from existing data to unearth hidden vulnerabilities.
- Automated responses: Quick reaction to potential breaches or anomalous activities without human intervention.
Cloud-based Security Solutions
Another emerging trend is the rise of cloud-based security solutions. As businesses increasingly migrate their operations to the cloud, the need for secure cloud infrastructure has never been more pressing. Cloud security solutions can provide the flexibility and scalability that on-premise solutions often lack.
For instance, a small business I advised recently transitioned to a cloud-based cybersecurity solution. They benefited from:
- Cost-effective scalability: Paying only for the protection they needed while easily upgrading as they grew.
- Centralized management: Simplifying security across various locations within a singular dashboard.
Internet of Things (IoT) Security
Lastly, Internet of Things (IoT) security is becoming a critical area of focus as more devices become connected. Each smart device can be a potential entry point for cyber threats, making it crucial to apply robust security measures. A family member who owns a smart home device learned this the hard way when a security vulnerability exposed their personal data.
Emerging innovations in IoT security include:
- Device authentication: Ensuring that only authorized devices can connect to networks.
- Network segmentation: Isolating IoT devices to limit potential breaches.
As these trends continue to shape the future of cybersecurity software development, organizations must remain vigilant and proactive in adapting to these changes. By staying ahead of the curve, businesses can effectively protect themselves against evolving cyber threats while maximizing operational efficiency.

Conclusion
Recap of Essential Features in Cybersecurity Software
As we wrap up our exploration of cybersecurity software, it’s essential to highlight the key features that play a critical role in safeguarding your digital assets. Effective cybersecurity solutions should include:
- Real-time threat detection: To identify vulnerabilities before they can be exploited.
- Data encryption capabilities: Ensuring that sensitive information is protected from unauthorized access.
- Multi-factor authentication: Adding an extra layer of security to user accounts.
- Firewall protection: Monitoring and controlling network traffic.
- Automatic updates and patch management: Keeping systems current and secure against emerging threats.
- User-friendly interface: Enabling seamless integration and ease of use for all employees.
Each of these features contributes to a comprehensive security framework, empowering organizations to tackle the complexities of modern cyber threats.
Final Recommendations for Choosing the Best Solution
When it comes to selecting the best cybersecurity software, consider your organizational needs and future growth. Here are some practical recommendations to guide your decision-making process:
- Conduct a thorough needs assessment: Consider the specific threats your organization faces and identify which features are necessary for your unique context.
- Evaluate compatibility and scalability: Ensure that the software can integrate well with your existing systems and can grow as your organization expands.
- Research customer support options: Timely and effective support is crucial; look for vendors with positive reviews regarding their customer service.
- Compare costs and licensing models: Find a solution that fits your budget while providing the features you need without compromising security.
By taking these steps, organizations can make informed decisions that lead to a secure digital environment. After all, investing in cybersecurity software is more than just a business expense—it’s a commitment to protecting valuable data and maintaining trust. Remember, across various industries, the right cybersecurity solution is not just a defensive measure but a strategic advantage in today’s digital landscape.