
Overview of Cybersecurity Mistakes
Defining Cybersecurity
In today’s digitally connected world, cybersecurity plays a crucial role in protecting sensitive data and ensuring the integrity of systems. At its core, cybersecurity refers to the practices, technologies, and measures designed to safeguard networks, devices, and information from cyber threats. Think of it as a security system for your home, but in the digital landscape, where malicious actors constantly seek ways to infiltrate and exploit vulnerabilities.
For example, just like locking your doors at night, implementing strong cybersecurity measures can prevent unauthorized access to your personal or business data.
Common Threats in Cyberspace
Cyber threats are diverse and constantly evolving. Here are some common threats that individuals and organizations often face:
- Malware: Malicious software designed to disrupt, damage, or gain unauthorized access to systems.
- Phishing: Deceptive emails or messages aimed at tricking users into revealing personal information.
- Ransomware: A type of malware that encrypts files and demands a ransom for the decryption key.
- Denial of Service (DoS) Attacks: Attempts to make a machine or network resource unavailable to users.
As the landscape of cybersecurity continues to evolve, being aware of these threats is the first step in prevention. Remember, knowledge is power, and staying informed can help you navigate the digital world more securely.

Not Using Strong Passwords
Importance of Strong Passwords
In the world of cybersecurity, passwords are your first line of defense. A strong password acts like a sturdy lock on your front door, keeping intruders at bay. Weak passwords, on the other hand, are akin to having your door wide open for anyone to walk in.
Consider this: many people still use simple passwords like “123456” or “password.” These are extremely easy for attackers to guess. Strong passwords help to protect not just your personal accounts but also sensitive information, reducing the risk of identity theft.
Tips for Creating Secure Passwords
Crafting robust passwords doesn’t have to be daunting. Here are some useful tips:
- Length: Aim for at least 12 characters; longer is better.
- Complexity: Use a mix of uppercase and lowercase letters, numbers, and special characters.
- Avoid Common Patterns: Steer clear of easily guessable phrases like your name, birthday, or common words.
- Use Passphrases: Create a memorable phrase, which is both lengthy and complex, like “PurpleElephantDances@11am!”
By implementing these strategies, you’ll significantly boost your account security. Adopting strong passwords is a simple yet effective way to enhance cybersecurity, ensuring the safety of your digital life.

Ignoring Software Updates
Risks of Not Updating Software
After strengthening your password, the next crucial step in safeguarding your cybersecurity is to keep your software updated. Ignoring software updates is like leaving a window open in a storm—inviting trouble. Outdated software can harbor vulnerabilities that cybercriminals are eager to exploit.
For instance, remember the time when a major ransomware attack affected countless systems simply because users had not applied updates? This can lead to data breaches, loss of sensitive information, and even financial loss.
Best Practices for Software Updates
To protect yourself effectively, here are some best practices for ensuring your software is current:
- Automatic Updates: Enable automatic updates whenever possible to ensure you’re always protected.
- Regularly Check for Updates: Set a reminder to periodically check for updates, especially for critical applications.
- Backup Before Updating: Always back up your data before applying updates to prevent potential issues during installation.
- Patch Management: Familiarize yourself with patch management practices, especially if you manage multiple devices.
By incorporating these best practices, you’ll fortify your defenses against cyber threats, keeping your systems secure and functioning smoothly. Remember, staying updated is a simple yet powerful way to enhance your cybersecurity strategy.
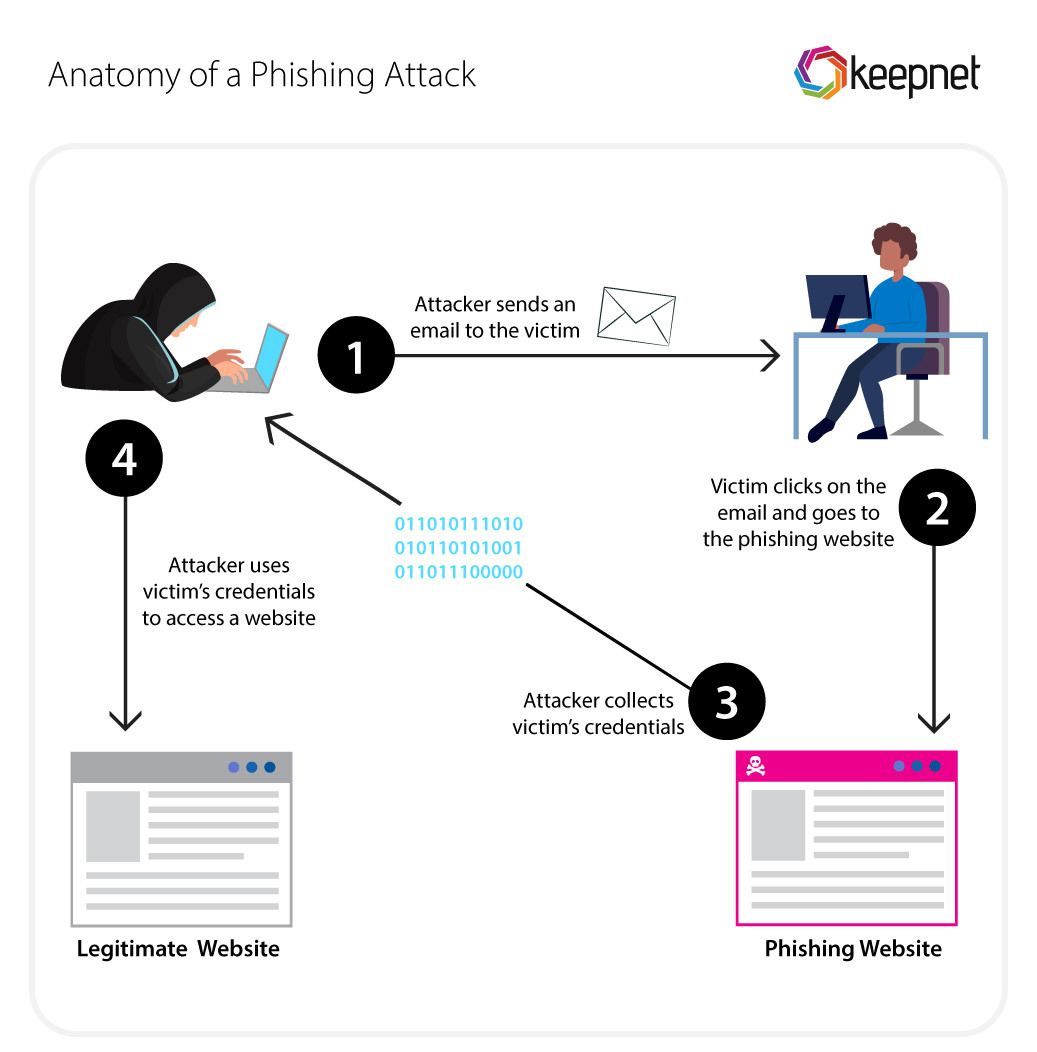
Clicking on Suspicious Links or Attachments
Types of Malicious Links and Attachments
As we’ve discussed software updates, it’s essential to now shift our focus to another significant cybersecurity concern: clicking on suspicious links or attachments. These threats come in various forms:
- Phishing Links: Designed to trick you into entering sensitive information on fake websites.
- Malware Attachments: Files that, when opened, install malicious software on your device.
- Shortened URLs: These can hide the true destination, making it easy to fall for a trap.
Imagine receiving an email from a seemingly trusted source, only to find it was a well-crafted phishing attempt.
How to Identify Suspicious Links
Recognizing these threats can be tricky, but here are some tips to help you stay safe:
- Hover Before Clicking: Place your cursor over links to reveal their true URLs; if they look odd, don’t click!
- Check the Sender’s Email: Ensure the email is from a legitimate source. Look for subtle misspellings in the domain.
- Use Link Scanners: Tools like VirusTotal allow you to scan links before clicking.
By practicing caution and vigilance, you can significantly reduce the chances of falling prey to malicious links and attachments, keeping your digital space secure.

Using Public Wi-Fi Networks Unprotected
Dangers of Public Wi-Fi
Having explored suspicious links, let’s now discuss a prevalent issue many users face: using public Wi-Fi networks without robust security measures. While logging in at a café or airport can be convenient, it poses significant risks. Public Wi-Fi networks are often unsecured, making it easy for hackers to intercept your data.
Imagine connecting to a coffee shop’s Wi-Fi and unknowingly allowing someone nearby to snoop on your online activities. Personal information, passwords, and credit card details can all be at risk.
Secure Ways to Use Public Wi-Fi
Fortunately, there are ways to use public Wi-Fi safely:
- Use a Virtual Private Network (VPN): A VPN encrypts your internet connection, keeping your data secure.
- Avoid Sensitive Transactions: If possible, postpone bank transactions or entering sensitive information until you’re on a secure network.
- Use HTTPS Websites: Look for the ‘https://’ designation in URLs, indicating a secure connection.
By adhering to these practices, you can enjoy the convenience of public Wi-Fi with peace of mind, ensuring your personal information remains protected.

Sharing Personal Information Online
Risks of Sharing Personal Data
Now that you’re more aware of public Wi-Fi vulnerabilities, it’s essential to address another pressing issue: sharing personal information online. In an age driven by social media, many individuals unknowingly expose sensitive data that can lead to identity theft or cyberbullying.
For example, posting details about your vacation dates can alert intruders to an opportunity for break-ins. It’s a harmless-sounding update that can have dire consequences.
Privacy Tips for Social Media
Safeguarding your personal information online doesn’t have to be overwhelming. Here are practical tips for enhancing your privacy:
- Adjust Privacy Settings: Review and customize your social media privacy settings to limit who can see your posts.
- Think Before You Post: Consider the potential consequences of sharing personal details, like locations or life events.
- Use Nicknames or Initials: For less critical information, consider using nicknames or initials instead of full names.
By adopting these strategies, you can enjoy the benefits of social media while keeping your personal information secure. Remember, safeguarding your data is a continuous effort and essential for a safer online experience.

Not Backing Up Data Regularly
Importance of Data Backup
Having discussed the significance of online privacy, it’s crucial to address another vital aspect of cybersecurity: regular data backups. Imagine losing essential files—photos, documents, or critical business information—due to a hardware failure or cyber attack. The aftermath can be devastating and often irreversible.
Backing up your data acts like an insurance policy, ensuring that even if something goes wrong, you can recover your vital information without a hitch.
Data Backup Methods and Tools
Fortunately, implementing regular backups is easier than ever. Here are some effective backup methods and tools:
- External Hard Drives: Store copies of your data on physical devices that can be easily connected to your computer.
- Cloud Storage: Services like Google Drive and Dropbox allow automatic backups and access from any device.
- Backup Software: Programs like Acronis or EaseUS can schedule regular backups, ensuring you don’t forget.
By establishing a regular backup routine, you’ll protect yourself from potential data loss, giving you peace of mind that your information remains secure and recoverable. Remember, taking this proactive step can save you from future headaches!

Disregarding Two-Factor Authentication
What is Two-Factor Authentication?
As we transition from data backup, let’s explore another crucial element of cybersecurity: Two-Factor Authentication (2FA). Essentially, 2FA is an extra layer of security that requires two forms of verification before granting access to your accounts. This typically includes something you know, like your password, and something you have, such as a smartphone or a security token. It’s similar to requiring both a key and a code to unlock your front door.
Think of it as having multiple locks on your door—each adding a level of protection against intruders.
Benefits of Using 2FA
Implementing 2FA can significantly enhance your online security. Here are some notable benefits:
- Increased Security: Even if someone steals your password, they can’t access your account without the second verification step.
- Peace of Mind: Knowing that you’re adding another layer of defense can reduce anxiety about potential breaches.
- Protection Against Phishing: 2FA helps thwart phishing attempts, as unauthorized users would still need access to your secondary verification method.
By embracing Two-Factor Authentication, you can bolster your defenses against cyber threats, making it a straightforward yet effective measure to safeguard your digital life. Prioritizing this step can be a game changer in cybersecurity!

Falling for Phishing Scams
Understanding Phishing Attacks
With Two-Factor Authentication and data backups in place, it’s equally vital to be vigilant against phishing scams, which are among the most deceptive tactics used by cybercriminals. Phishing attacks often involve emails or messages impersonating reputable organizations, luring individuals into providing sensitive information like passwords or credit card details.
For instance, you might receive an urgent email from what appears to be your bank, asking you to confirm your account information. It’s designed to create a sense of urgency, increasing the chances of a response.
How to Avoid Falling for Phishing Scams
Preventing phishing scams requires a keen eye and healthy skepticism. Here are effective strategies:
- Verify the Source: Always double-check the sender’s email address and look for inconsistencies.
- Avoid Clicking Links: Instead of clicking on links in emails, visit the official website directly by typing it into your browser.
- Look for Red Flags: Be wary of poor grammar, generic greetings, and urgent calls to action—these can indicate a phishing attempt.
By taking these precautions, you’ll enhance your overall digital security and reduce the likelihood of falling victim to phishing scams. Staying informed and cautious is key to navigating the online world safely!

Neglecting Cybersecurity Training
Importance of Cybersecurity Awareness
As we conclude our exploration of common cybersecurity mistakes, it’s vital not to overlook the importance of cybersecurity training. Awareness is the first line of defense against various threats. When individuals understand the risks, they’re better equipped to identify and respond to potential security incidents.
For instance, after attending a cybersecurity workshop, I felt more confident spotting a phishing email in my inbox, which could have otherwise compromised my information.
Implementing Ongoing Training Programs
To foster a culture of security, organizations should implement ongoing cybersecurity training programs. Here are a few best practices:
- Regular Workshops: Conduct training sessions at least twice a year to keep employees updated on the latest threats and practices.
- Interactive Learning: Use quizzes, simulations, and real-life scenarios to engage participants.
- Feedback Mechanism: Encourage participants to share experiences and suggest improvements for future training.
By prioritizing cybersecurity education, organizations not only protect themselves but also empower their employees, creating a steadfast defense against cyber threats. Continuous learning in this area is essential for staying one step ahead in the ever-evolving landscape of cybersecurity!

