Understanding Cyber Espionage and Cyber Crime
Differentiating Cyber Espionage and Cyber Crime
When discussing the murky waters of the digital world, the terms “cyber espionage” and “cyber crime” are often thrown around interchangeably. However, there is a significant distinction between the two, which can help individuals and organizations better prepare against these threats.
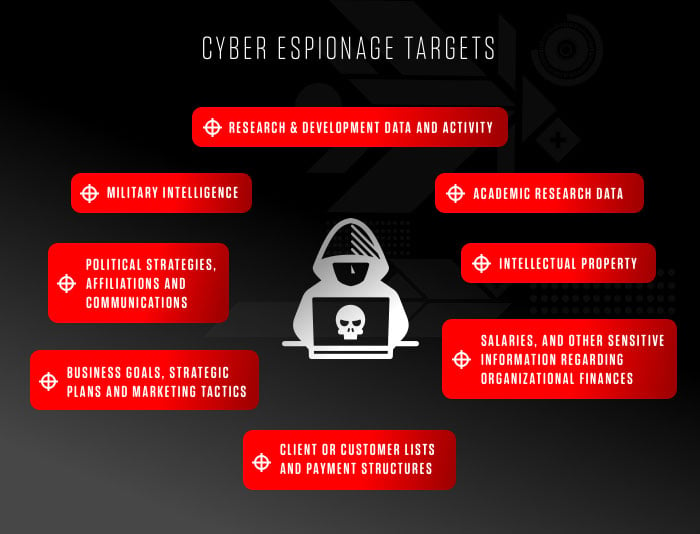
Cyber espionage primarily involves the stealthy acquisition of sensitive or confidential information, typically conducted by state actors or corporate competitors. The intent is to gain strategic advantages—often in areas like defense, technology, or trade secrets.
On the other hand, cyber crime encompasses a broader range of illicit activities conducted online, aimed at personal or financial gain. This can include anything from hacking into personal bank accounts to large-scale identity theft schemes.
Here’s a quick breakdown:
- Cyber Espionage:
- Purpose: Gain strategic information
- Actors: Often state-sponsored or corporations
- Intended Impact: Economic or political advantage
- Cyber Crime:
- Purpose: Financial profit or personal gain
- Actors: Individual hackers or organized crime groups
- Intended Impact: Financial loss, data breaches, or personal harm
Importance of Distinguishing Between the Two
Understanding the differences between cyber espionage and cyber crime is crucial for effective risk management. For instance, a company may establish different security protocols based on whether they are protecting against corporate spies or individual hackers.
Consider this: a firm could invest heavily in cybersecurity measures tailored for espionage but may overlook simple phishing attempts that cyber criminals use to exploit vulnerabilities. Without recognizing the nuances, organizations run the risk of focusing resources in the wrong areas, thereby increasing their exposure to possible threats.
In essence, distinguishing between cyber espionage and cyber crime not only clarifies the nature of the threats but also informs the decisions on deploying the right defenses. This knowledge equips companies and individuals alike to be proactive rather than reactive in their cybersecurity strategies, ensuring a more secure digital landscape.

Methods and Techniques in Cyber Espionage
Social Engineering Attacks
As organizations work tirelessly to fortify their cybersecurity measures, one crucial methodology that cyber spies still employ is social engineering attacks. These tactics exploit human psychology rather than technological vulnerabilities. Essentially, it’s all about tricking individuals into divulging sensitive information or granting access they wouldn’t normally allow.
Consider a common scenario: a fraudulent email appears to be from IT, asking employees to reset their passwords. Unsuspecting staff members click on the link, unwittingly handing over their credentials to the attackers. This simple yet effective method highlights how a skilled manipulator can bypass sophisticated security systems with little more than clever persuasion.
Key elements of social engineering include:
- Phishing: Deceptive emails that appear legitimate.
- Pretexting: Creating a fabricated scenario to steal information.
- Baiting: Offering something enticing to lure individuals into a trap.
Advanced Persistent Threats (APTs)
While social engineering relies on human error, Advanced Persistent Threats (APTs) take a more systematic approach. APTs represent a prolonged and targeted cyberattack, often orchestrated by organized groups seeking high-value information. Unlike a one-off hack, APTs are deeply strategic and can go undetected for an extended period.
An example frequently cited in cybersecurity discussions involves nation-state actors, who utilize APTs to infiltrate government or corporate networks. Once inside, these attackers may linger undetected, gathering intelligence over time.
APTs often involve:
- Infiltration via Malware: Utilizing sophisticated software to establish and maintain access.
- Data Exfiltration: Stealing large volumes of sensitive data gradually to avoid detection.
- Multiple Attack Vectors: Exploiting various weaknesses across networks and systems.
Understanding these methods equips organizations with the insight needed to develop better defenses against the persistent threats that loom in the digital landscape. Educating employees about social engineering and implementing advanced security measures can turn the tide against these sophisticated espionage techniques.

Types of Cyber Crimes
Malware Attacks
In the digital realm, malware attacks are among the most pervasive and destructive forms of cyber crime. Simply put, malware is malicious software designed to infiltrate and damage systems without the user’s consent. From spyware that collects user information to viruses that corrupt files, malware can create chaos in both personal and business environments.
For instance, imagine a small business unaware that an employee mistakenly downloaded a malicious file attached to a seemingly innocuous email. As the malware spreads, it could compromise sensitive client data or disrupt workflows.
Types of malware include:
- Viruses: Programs that replicate themselves and spread to other files.
- Trojan Horses: Malicious software disguised as legitimate applications.
- Worms: Standalone malware that replicates to spread across networks.
Phishing Scams
Closely related to malware are phishing scams, which employ deceptive tactics to trick individuals into revealing personal information, such as passwords or credit card details. Phishing attacks usually come in the form of fake emails or websites that appear legitimate.
A relatable example is receiving an alert from a well-known bank, requesting urgent verification of account details—only to find out that the communication was a disguise crafted by cyber criminals.
Key elements of phishing scams include:
- Spoofed Emails: Emails claiming to be from trusted sources.
- Clone Websites: Websites that mimic the look and feel of real ones.
- Urgent Language: Messages designed to create panic and prompt rash actions.
Ransomware Incidents
Ransomware incidents have become increasingly prevalent and are particularly alarming due to their capacity to disrupt operations. This form of cyber crime involves encrypting a victim’s files and demanding a ransom for their release.
Consider the case where a hospital’s network is locked down, preventing staff from accessing patient records. The attackers demand a hefty sum in exchange for the decryption key, leaving the institution in a precarious position.
Characteristics of ransomware include:
- Infection Vectors: Phishing emails or unsecured networks through which malware spreads.
- Encryption: Locking files, rendering them inaccessible to the victim.
- Demand for Payment: Usually in cryptocurrencies to protect the identity of the criminals.
By recognizing these types of cyber crimes, individuals and organizations can better prepare their defenses and develop a mindset of vigilance in the ever-evolving digital landscape. Knowing how to spot potential threats is the first step in safeguarding not only one’s data but also overall digital health.

Motivations Behind Cyber Espionage and Cyber Crimes
State-Sponsored Activities
The motivations behind cyber espionage and cyber crimes often stem from a variety of objectives, with state-sponsored activities being one of the most prominent. Governments around the world engage in cyber espionage to obtain sensitive information about other nations or organizations, aiming to build strategic advantages in various domains, including military, economic, and technological.
For example, consider how one country may target another’s defense systems to identify vulnerabilities or monitor military capabilities. Such activities not only highlight the complexity of international relationships but also deepen the level of mistrust among nations.
Characteristics of state-sponsored activities include:
- Geopolitical Objectives: Gaining leverage in diplomatic relations.
- Economic Espionage: Stealing trade secrets to bolster national industries.
- Military Intelligence: Understanding the capabilities of rival nations.
Financial Gain
Another significant driver of cyber crimes is financial gain, which motivates various criminals including hackers and organized crime syndicates. The ease and anonymity of operating online create fertile ground for illicit profits. This is particularly clear in cases like identity theft or credit card fraud, where criminals exploit personal information for direct financial benefit.
A classic scenario involves individuals falling prey to data breaches at large retailers, leading to stolen credit card numbers and subsequent financial losses.
Some common forms of financially motivated cyber crime include:
- Ransomware: Demanding payment to restore access to encrypted files.
- Phishing: Deceiving individuals into providing sensitive financial details.
- Fraudulent Transactions: Conducting unauthorized transactions using stolen credentials.
Hacktivism
Lastly, hacktivism introduces a highly intriguing motivation into the mix. Here, individuals or collectives engage in cyber crimes to promote political agendas or social change. This form of activism uses hacking techniques to protest against governments, corporations, or other entities.
One notable instance involves the group Anonymous, which has garnered headlines for various operations aimed at exposing perceived injustices or restricting free speech.
Characteristics of hacktivism include:
- Ideological Motivations: Seeking to promote social or political causes.
- Targeted Attacks: Focusing on specific entities deemed problematic.
- Raising Awareness: Using cyber attacks as a means to highlight issues.
Understanding these motivations is pivotal for organizations and individuals alike, as it aids in crafting effective defenses against the multifaceted threats posed by both cyber espionage and cyber crimes. By being aware of the “why” behind these activities, stakeholders can implement more targeted strategies to combat them effectively.

Legal Implications and Consequences
International Laws and Treaties
As cyber crime and cyber espionage loom larger on the global stage, the legal landscape surrounding these issues has become increasingly complex. International laws and treaties play a crucial role in establishing frameworks to address cyber offenses that transcend national borders.
For instance, treaties such as the Council of Europe’s Convention on Cybercrime, also known as the Budapest Convention, aim to facilitate international cooperation in combating cyber crime. This treaty creates standards for the investigation and prosecution of cyber crimes, ensuring that nations can work together effectively.
Key aspects of international laws and treaties include:
- Jurisdiction: Defining where a cyber crime occurs and where it can be prosecuted.
- Extradition: Establishing procedures for surrendering offenders between nations.
- Collaboration: Encouraging nations to share information and resources to tackle cyber threats.
Prosecution of Cyber Criminals
The prosecution of cyber criminals is a pressing concern for law enforcement agencies worldwide. However, bringing these criminals to justice can be fraught with challenges, given the anonymity of the internet and the complexity of digital evidence.
An illustrative example is the case of a hacker based in one country targeting businesses in another. The differences in legal systems can complicate the process of gathering evidence and pursuing charges.
Some common challenges in prosecution include:
- Attribution: Pinpointing the actual perpetrator can be difficult, as cyber criminals often use proxies or masks to hide their identities.
- Digital Evidence: The collection and presentation of digital evidence require specialized skills and tools.
- Varying Laws: Disparities between different countries’ laws may hinder successful prosecution.
In conclusion, understanding the legal implications and consequences of cyber espionage and cyber crimes is essential for both businesses and individuals. By staying informed about international laws and the prosecution landscape, stakeholders can better navigate the complexities of cyber security, ensuring they are not only protected from potential threats but also aware of their rights and responsibilities in a digital world. Adapting to this evolving legal framework will be key in the quest for a safer cyberspace.

Preventive Measures and Security Practices
Cybersecurity Protocols
As the digital landscape continues to evolve, implementing robust cybersecurity protocols becomes increasingly critical in safeguarding against cyber threats. Organizations must adopt a comprehensive approach, blending technological solutions with human vigilance.
For instance, regular security training for employees can be a game-changer. Consider a company that conducts monthly workshops on recognizing phishing emails. The difference is clear: employees who are more educated about potential threats are less likely to fall victim to them.
Key cybersecurity protocols to consider include:
- Firewall Management: Configuring firewalls to restrict unauthorized access to internal networks.
- Regular Software Updates: Ensuring that all software and systems are updated promptly to patch vulnerabilities.
- Access Controls: Implementing role-based access controls to limit data access to only those who need it.
By establishing such protocols, organizations can significantly reduce the risk of cyber breaches, creating a culture of security awareness among employees.
Data Encryption Techniques
Another potent preventive measure is data encryption. Encrypting sensitive data ensures that even if it falls into the wrong hands, it remains unreadable without the proper decryption keys. This technique is particularly important for businesses dealing with personal or financial information.
For example, consider a financial institution that encrypts its customer data both in transit and at rest. In the unfortunate event of a data breach, even if hackers access the data, what they find would be scrambled and useless.
Some effective data encryption techniques include:
- AES (Advanced Encryption Standard): A widely adopted symmetric encryption technique known for its strength.
- SSL/TLS Encryption: Used for securing data transferred across the internet, such as during online transactions.
- End-to-End Encryption: Ensures that only communicating users can access the data, safeguarding it from intermediaries.
Incorporating both cybersecurity protocols and data encryption techniques serves as a dual defense strategy against cyber threats. While protocols establish robust barriers and educate users, encryption adds an invaluable layer of security to sensitive data — providing peace of mind that critical information is protected in an increasingly dangerous digital world. By being proactive in adopting these preventive measures, individuals and organizations can significantly reduce their vulnerability to cyber crimes and espionage.

Case Studies: Real-World Examples
Notable Cyber Espionage Incidents
Examining real-world examples of cyber espionage sheds light on the tactics employed and the implications for national security and corporate integrity. One infamous incident occurred with the 2015 breach of the U.S. Office of Personnel Management (OPM). Hackers, believed to be state-sponsored, accessed sensitive data of over 22 million government employees, gathering not just personal information but also security clearance details.
This breach exemplifies the strategic nature of cyber espionage, revealing how adversaries can exploit governmental vulnerabilities to obtain invaluable intelligence. Key aspects of this incident included:
- Complex Infiltration: Attackers used sophisticated techniques to bypass security protocols.
- Long-Term Objectives: The focus was on acquiring sensitive data that could be leveraged for future intelligence operations.
- International Ramifications: The incident heightened tensions between nations, showcasing the delicate balance of cyber diplomacy.
High-Profile Cyber Crime Cases
On the other side of the spectrum, high-profile cyber crime cases illustrate the varied motivations of individual hackers and organized crime groups. A glaring example is the 2017 Equifax breach, where hackers exploited a vulnerability to access the personal information of approximately 147 million people, including Social Security numbers and financial data.
What made this case particularly alarming was not just the scale of the breach, but the prolonged time it took for Equifax to detect and disclose the attack. Highlights from this case include:
- Failure to Patch: A known vulnerability was not addressed promptly, allowing the breach to occur.
- Massive Data Theft: The scale of the breach had severe consequences for victims, ranging from identity theft to financial ruin.
- Reputation Damage: The fallout included lawsuits, regulatory scrutiny, and a significant loss of public trust.
These case studies emphasize the critical need for reliable cybersecurity measures and threat awareness. By learning from both notable cyber espionage incidents and high-profile cyber crimes, organizations can better understand the tactics used by criminals and implement effective strategies to protect themselves from similar threats in the future. Through vigilance and proactive measures, the digital landscape can be made considerably safer.

The Future of Cyber Threats
Emerging Trends in Cyber Espionage
As technology continues to advance, the landscape of cyber espionage is evolving, bringing new challenges and concerns for organizations and governments alike. One prominent trend is the increasing sophistication of attacks, often utilizing artificial intelligence (AI) and machine learning to automate and enhance the reconnaissance phase.
For example, cyber espionage actors can deploy AI algorithms to analyze vast amounts of publicly available data and pinpoint potential vulnerabilities in targeted organizations. This not only speeds up the attack planning process but also makes it more precise. Some emerging trends to watch for include:
- Supply Chain Attacks: Targeting third-party vendors to infiltrate larger organizations.
- Internet of Things (IoT) Vulnerabilities: As smart devices proliferate, so do their security flaws, becoming attractive targets for espionage.
- Deepfake Technology: The potential for creating misleading content that could deceive employees or stakeholders into divulging sensitive information.
Evolving Strategies of Cyber Criminals
On the other hand, cyber criminals are also adapting their strategies, making their attacks more elusive and harder to identify. One notable tactic is the rise of ransomware-as-a-service, where malicious actors sell ransomware kits on the dark web. This democratization of cyber crime allows less technically savvy individuals to launch attacks, exponentially increasing the threat landscape.
Additionally, public outrage over data breaches is prompting a shift toward more sophisticated social engineering schemes. For instance, criminals might exploit current events or social movements to create compelling phishing campaigns that resonate emotionally with potential victims.
Here are some evolving strategies to keep an eye on:
- Targeted Phishing: Using tailored messages that appeal specifically to the recipient.
- Multi-Stage Attacks: Combining various techniques over time to achieve objectives without being detected.
- Focus on Remote Workers: With more people working from home, cyber criminals are capitalizing on less secure home networks.
As we move into the future, understanding these emerging trends in cyber espionage and the evolving strategies of cyber criminals is vital for preparing defenses. Staying alert and proactive can make a significant difference in safeguarding sensitive data and maintaining trust in digital interactions. By fostering a culture of awareness and preparedness, individuals and organizations can better navigate the complexities of the ever-changing cyber threat landscape.

