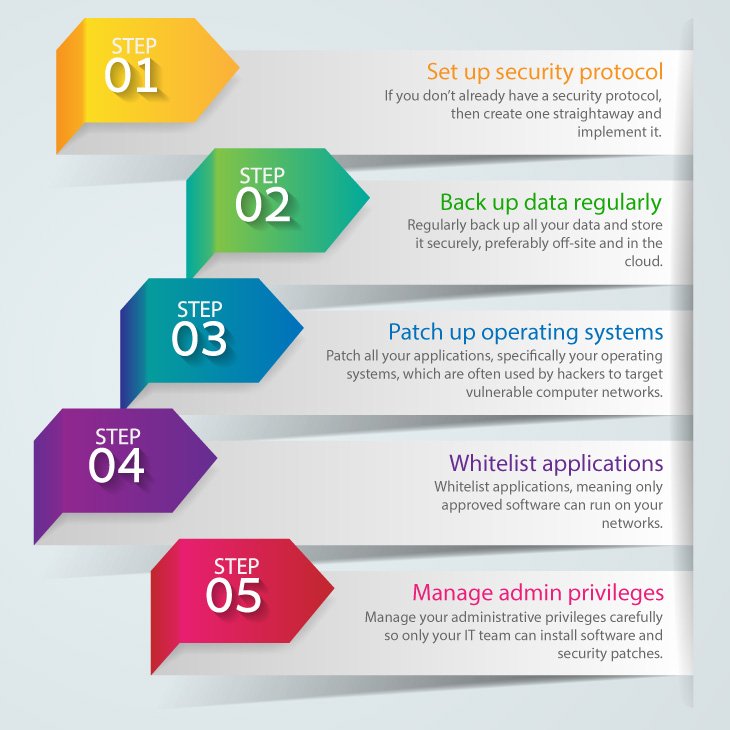
Introduction
Understanding Cybersecurity Compliance
In an age where cyber threats are increasingly sophisticated, understanding cybersecurity compliance is crucial for organizations of all sizes. Compliance refers to the adherence to standards, regulations, and laws that protect sensitive data from unauthorized access and breaches. Organizations like healthcare providers and financial institutions often find themselves navigating stringent regulations such as HIPAA or PCI DSS. The stakes are high; a single data breach not only jeopardizes client trust but can also result in hefty fines.
Significance of Creating a Checklist
Creating a compliance checklist serves as an essential tool for any organization aiming to adhere to these regulations. Checklists streamline the compliance process, enabling teams to focus on essential tasks. Here are a few benefits of an effective compliance checklist:
- Clarity: It provides clear steps to follow, reducing the chance of overlooking key tasks.
- Accountability: Assigning specific responsibilities fosters accountability within teams.
- Efficiency: By outlining tasks, it helps prioritize actions that need immediate attention.
As organizations delve deeper into the complexities of compliance, a well-structured checklist emerges as a foundational element in their cybersecurity strategy.

Identifying Regulatory Requirements
Overview of Common Cybersecurity Regulations
As organizations embark on their compliance journey, it’s vital to be familiar with common cybersecurity regulations that govern data protection. Some of the widely recognized regulations include:
- GDPR (General Data Protection Regulation): Enforced in the European Union, this regulation mandates strict rules regarding personal data handling and privacy.
- HIPAA (Health Insurance Portability and Accountability Act): This U.S. regulation governs the protection of health information and applies to healthcare providers, insurers, and their business associates.
- PCI DSS (Payment Card Industry Data Security Standard): A set of security standards designed to ensure that companies handling credit card information maintain a secure environment.
These regulations serve as a baseline for organizations to protect sensitive information effectively.
Importance of Complying with Regulations
Compliance is not just a legal obligation; it’s a strategic necessity. Ensuring adherence to these regulations entails several significant benefits:
- Trust Building: It strengthens public confidence in the organization’s ability to protect data.
- Risk Reduction: Compliance reduces the risk of data breaches and minimizes financial penalties.
- Competitive Advantage: Companies that demonstrate regulatory compliance can differentiate themselves in the market.
By weaving compliance into the organizational fabric, businesses not only fulfill their legal responsibilities but also bolster their reputation.
Components of a Cybersecurity Compliance Checklist
Risk Assessment Procedures
To navigate the complex landscape of cybersecurity compliance, a thorough risk assessment is indispensable. This process identifies potential vulnerabilities, threats, and the possible impact on the organization. By systematically evaluating risks, companies can prioritize their responses effectively. Key elements to consider in risk assessment include:
- Asset Identification: Determine which data and systems are crucial to your operations.
- Threat Analysis: Evaluate potential threats that could compromise these assets.
- Impact Assessment: Analyze the consequences of a data breach on operations and reputation.
Data Protection Measures
Data protection measures are critical in safeguarding sensitive information from unauthorized access. Implementing best practices ensures compliance with various regulations. Some fundamental strategies include:
- Encryption: Encrypt sensitive data both in transit and at rest.
- Access Controls: Limit data access to authorized personnel only.
- Regular Backups: Maintain frequent backups to recover data in case of breaches.
Incident Response Plans
Despite preventive measures, incidents can still occur. A robust incident response plan is essential for minimizing damage and ensuring compliance. This plan should outline:
- Roles and Responsibilities: Designate team members for specific tasks during an incident.
- Communication Protocols: Establish clear communication channels for internal and external stakeholders.
- Post-Incident Review: Analyze the response process to improve future strategies.
By integrating these components into a cybersecurity compliance checklist, organizations can enhance their overall security posture and cultivate resilience against cyber threats.
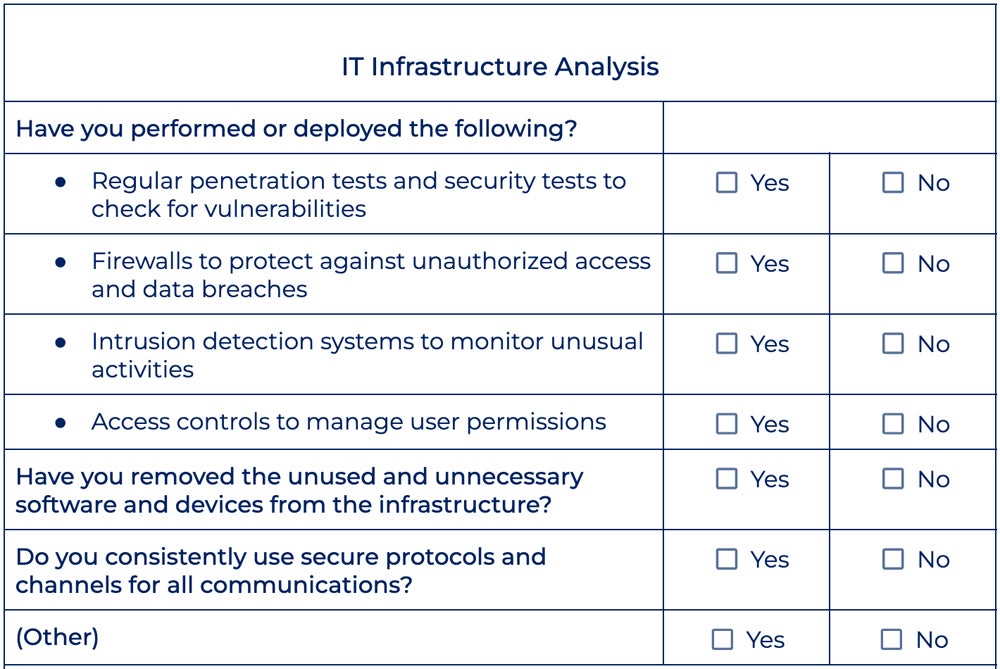
Developing a Customized Compliance Checklist
Tailoring Checklists to Specific Regulations
The journey towards compliance isn’t one-size-fits-all. To ensure effectiveness, organizations must develop a customized compliance checklist tailored to specific regulations they are subject to. This tailored approach enhances focus and efficiency. Here’s how to effectively customize your checklist:
- Identify Applicable Regulations: Start by determining which regulations impact your organization (e.g., GDPR, HIPAA, PCI DSS).
- Analyze Requirements: Break down each regulation into actionable items relevant to your operations.
- Prioritize Key Areas: Focus on areas with the greatest risk or complexity to ensure compliance.
By addressing specific regulatory needs, companies can better allocate their resources and meet compliance thresholds more effectively.
Involving Key Stakeholders in Checklist Creation
Creating an effective compliance checklist requires collaboration across various departments. Involving key stakeholders, including IT, legal, and operations teams, provides a comprehensive perspective. Here are methods to ensure stakeholder participation:
- Conduct Workshops: Host collaborative workshops to gather insights and prioritize compliance obligations.
- Assign Roles: Clearly define roles for each stakeholder involved, emphasizing accountability.
- Continuous Feedback: Establish a feedback loop during the checklist development process to refine and optimize.
Engaging stakeholders fosters a sense of ownership, ensuring that everyone is aligned with compliance objectives. This collaborative approach promotes a culture of compliance throughout the organization.
Implementing and Monitoring Compliance
Execution of Compliance Checklist
With a customized compliance checklist in hand, the next step is execution. This phase is critical, as it translates theory into practice. Here are some strategies for effective execution:
- Assign Responsibilities: Clearly designate who will execute each item on the checklist. This promotes accountability.
- Set Deadlines: Establish realistic timelines for each task to ensure steady progress toward compliance goals.
- Monitor Progress: Regularly check in on the status of each task, providing support or resources as needed.
By making execution a collaborative effort, organizations can maintain focus and drive toward compliance.
Regular Auditing and Updates
Once the checklist is being executed, regular auditing is essential. Audits not only verify compliance but also highlight areas for improvement. To keep the checklist relevant, consider the following:
- Schedule Audits: Conduct routine audits (e.g., quarterly or bi-annually) to assess ongoing compliance.
- Incorporate Feedback: Use insights from audits to update and refine the checklist continuously.
- Adapt to Changes: Stay informed about regulatory changes or emerging threats and adjust the checklist accordingly.
By implementing these practices, organizations can foster a dynamic compliance environment, ensuring both adherence and resilience in the face of evolving cyber threats.
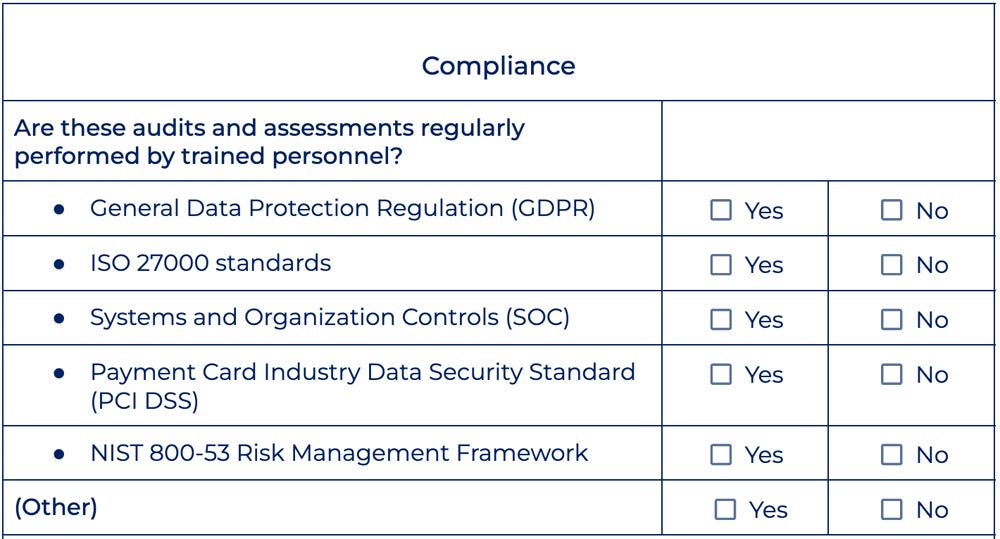
Case Studies: Successful Implementation of Compliance Checklists
Real-world Examples of Effective Compliance Strategies
Examining real-world examples of successful compliance checklist implementation can provide valuable insights for organizations. For instance, consider a financial institution that adopted a comprehensive compliance checklist tailored to the PCI DSS standards. By methodically addressing each requirement, the institution was able to reduce its risk of data breaches significantly and achieve certification ahead of schedule. Key strategies included:
- Thorough Risk Assessment: Regularly identifying vulnerabilities within their systems.
- Stakeholder Involvement: Engaging various departments during the checklist creation ensured broad ownership and insight.
Such strategies not only facilitated compliance but also fostered a proactive security culture.
Lessons Learned from Compliance Failures
Conversely, it’s crucial to learn from compliance failures as well. A notable case involved a healthcare provider that neglected to regularly update its HIPAA compliance checklist. As a result, they experienced a data breach, leading to hefty fines and reputational damage.
Key lessons from this unfortunate incident include:
- Regular Updates: Compliance checklists must evolve alongside regulations and organizational needs.
- Routine Training: Ongoing employee training ensures all team members are aware of compliance protocols and requirements.
By understanding both successes and missteps, organizations can create more effective compliance strategies to navigate the complexities of cybersecurity.

Tools and Technologies for Managing Compliance
Automation Solutions for Compliance Checks
As organizations strive to keep up with increasingly complex compliance requirements, automation solutions have emerged as a game changer. By automating compliance checks, organizations can save time, reduce human error, and enhance accuracy. For example, an enterprise that implemented automated compliance tools was able to run continuous monitoring of its security posture instead of relying on periodic manual checks. Key benefits of automation include:
- Real-Time Monitoring: Automated systems can identify compliance issues as they arise, allowing for swift corrective actions.
- Streamlined Reporting: Automated reports simplify documentation, making it easier to demonstrate compliance to auditors.
With these solutions, organizations can focus more on strategic initiatives rather than getting bogged down in mundane tasks.
Role of Software in Simplifying Compliance Processes
Software solutions play a critical role in simplifying compliance processes. Comprehensive compliance management platforms can consolidate various requirements, making it easier for teams to track their progress. For instance, a cloud-based compliance management tool allows organizations to:
- Centralize Documentation: Store all compliance-related documentation in one place for easy access.
- Facilitate Collaboration: Enable real-time collaboration among stakeholders, improving communication and accountability.
By leveraging these technologies, organizations can build a more resilient compliance framework and foster a culture of continuous improvement.

Ensuring Continuous Improvement
Feedback Loops in Compliance Checklists
To achieve lasting compliance success, it is essential to implement feedback loops in your compliance checklists. This iterative process allows organizations to gather insights and make improvements over time. For example, after a compliance audit, a team gathered input from various departments to discuss what worked and what didn’t. Some strategies for effective feedback loops include:
- Post-Implementation Reviews: After executing the checklist, hold debrief sessions to evaluate performance.
- Stakeholder Surveys: Collect anonymous feedback to understand challenges faced during compliance activities.
- Regular Staff Training: Use feedback to refine training programs to address identified gaps.
These techniques help foster a culture of openness, ensuring everyone is committed to continuous improvement.
Adapting Checklists to Evolving Threats
Lastly, it’s crucial to adapt compliance checklists to address evolving cybersecurity threats. The landscape is constantly changing, and what worked yesterday might not be sufficient tomorrow. Organizations should stay informed about:
- Emerging Threats: Regularly consult threat intelligence reports to identify new risks.
- Regulatory Changes: Update checklists to align with any new or revised regulations.
By continuously refining compliance checklists, organizations can maintain a proactive stance against emerging threats, ensuring their security measures remain effective and relevant. This commitment to evolution reinforces their overall compliance strategy and safeguards sensitive data.

Conclusion
Recap of Key Considerations
As we’ve explored throughout this discussion, developing a robust compliance strategy is imperative for any organization delving into cybersecurity. Key considerations include:
- Creating a Comprehensive Checklist: Tailoring checklists to specific regulations and involving stakeholders enhances accountability.
- Implementing and Monitoring: A proactive approach, including regular audits and feedback loops, ensures continual alignment with compliance standards.
- Leveraging Technology: Utilizing automation tools simplifies processes and supports real-time monitoring.
These elements form the backbone of an effective cybersecurity compliance strategy, safeguarding sensitive data and bolstering organizational integrity.
Future Trends in Cybersecurity Compliance
Looking ahead, several trends are likely to shape the landscape of cybersecurity compliance. Businesses must prepare for:
- Increased Regulation: As data protection becomes more critical, expect more stringent regulations across various sectors.
- Integration of AI: Artificial intelligence will play a pivotal role in enhancing compliance monitoring and threat detection.
- Focus on Zero Trust Models: Emphasizing continuous verification, zero trust architecture will become a standard framework for organizations aiming to strengthen their security posture.
By staying attuned to these trends, organizations can not only meet current requirements but also future-proof their compliance strategies against evolving threats and regulations.