Introduction
Understanding Cloud Security
In today’s digital landscape, cloud security has become paramount for businesses of all sizes. As organizations migrate their operations to cloud environments, understanding the complexities of securing data in this virtual space is crucial. Effective cloud security encompasses various strategies, from encrypting sensitive information to implementing robust access controls.
Risks of Data Breaches in the Cloud
Data breaches pose significant risks that can lead to devastating consequences, including:
- Financial Loss: The average cost of a data breach can reach into millions.
- Reputational Damage: Consumers may lose trust in brands that fall victim to breaches.
- Legal Consequences: Non-compliance with regulations can result in hefty fines.
Organizations must recognize these vulnerabilities and proactively implement protective measures to safeguard their data. The journey of cloud security requires diligence and a thorough understanding of its intrinsic risks.

Fundamentals of Cloud Security
Encryption and Key Management
As organizations embrace cloud solutions, maintaining the confidentiality of sensitive data through encryption is crucial. Encryption transforms readable data into unreadable formats, essentially acting as a shield against unauthorized access. However, it’s not just about encryption; effective key management is vital. Consider it the master key to your data vault. Proper strategies include:
- Regular Key Rotation: Changing keys periodically to minimize risks.
- Access Controls: Only authorized personnel should manage encryption keys.
Access Controls and Identity Management
Access controls and identity management play a pivotal role in cloud security. Implementing strong authentication measures ensures that only the right individuals have access to critical data. Consider the following approaches:
- Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring two or more verification methods.
- Role-Based Access Control (RBAC): Assigning access levels based on user roles to minimize exposure.
By combining encryption with robust access controls, organizations can fortify their cloud security framework effectively.

Securing Data in the Cloud
Data Loss Prevention
With an increasing amount of sensitive information stored in the cloud, Data Loss Prevention (DLP) becomes essential. DLP solutions help you monitor and protect critical data from being lost, misused, or accessed by unauthorized users. Here are some key strategies for effective DLP:
- Classifying Data: Understanding what data is sensitive helps in prioritizing protection efforts.
- Monitoring Data Movement: Keeping track of how data is shared and accessed can help identify anomalies.
Network Security in the Cloud
Network security is another cornerstone of cloud data protection. Ensuring secure connections and robust defenses against cyber threats minimizes risks. Implementing the following measures is crucial:
- Firewalls: Use virtual firewalls to monitor and control incoming and outgoing traffic.
- Intrusion Detection Systems (IDS): These systems help detect suspicious activities within your network.
Together, DLP and strong network security form a formidable defense, ensuring your data remains intact and secure in the cloud.

Compliance and Governance in Cloud Security
Regulatory Compliance
In the realm of cloud security, regulatory compliance is not just a checkbox; it’s a necessity. Organizations must navigate a labyrinth of local and international regulations, such as GDPR, HIPAA, or CCPA, to safeguard sensitive data. Compliance ensures that businesses uphold best practices and demonstrate accountability. Key steps include:
- Regular Compliance Assessments: Periodically evaluate your cloud operations against regulatory requirements.
- Documentation: Maintain thorough records of data processing activities and compliance efforts.
Security Auditing
Security auditing is the next vital layer in compliance and governance. Conducting regular audits allows organizations to identify potential vulnerabilities and ensure adherence to regulatory standards. Here’s how to approach it:
- Internal and External Audits: Bring in third-party auditors to provide fresh perspectives on your security posture.
- Continuous Monitoring: Use automated tools to monitor compliance in real-time, ensuring ongoing adherence to regulations.
By prioritizing regulatory compliance and security auditing, organizations can strengthen their cloud security framework and mitigate risks effectively.

Emerging Technologies in Cloud Security
Cloud Access Security Brokers (CASBs)
As cloud adoption increases, organizations are turning to Cloud Access Security Brokers (CASBs) to enhance their security frameworks. CASBs serve as intermediaries, providing robust security controls across different cloud services. These solutions can help organizations by:
- Visibility: Offering insights into user activities and data access across cloud services.
- Data Security: Enforcing encryption and tokenization to protect sensitive data.
Secure Cloud Storage Solutions
Alongside CASBs, secure cloud storage solutions are also gaining traction. These platforms focus on safeguarding data at rest and in transit. Key features to look for include:
- End-to-End Encryption: Ensures your data remains protected from unauthorized access.
- Redundancy: Multiple data copies stored in different locations to prevent loss.
Embracing these emerging technologies helps organizations bolster their cloud security posture while managing risks effectively. As the digital landscape evolves, staying ahead of vulnerabilities is essential for long-term success.
Incident Response and Disaster Recovery in the Cloud
Detection and Response Strategies
In the fast-paced world of cloud computing, effective incident response strategies are critical for minimizing damage during a security breach. Implementing real-time detection tools can help identify threats before they escalate. Key strategies include:
- Automated Alerts: Set up triggers that notify the security team of suspicious activities instantly.
- Collaboration Tools: Equip teams with communication platforms to streamline incident response efforts.
Business Continuity Planning
Alongside detection strategies, a solid business continuity plan ensures that operations can continue even during a disaster. This involves:
- Regular Testing: Conduct drills to evaluate plan effectiveness and ensure team readiness.
- Data Backup: Regularly schedule backups, both on-site and off-site, to protect essential information.
By prioritizing incident response and business continuity planning, organizations can not only recover from breaches but also enhance resilience in the cloud environment. These proactive measures foster a strong security culture, empowering teams to respond effectively to evolving threats.
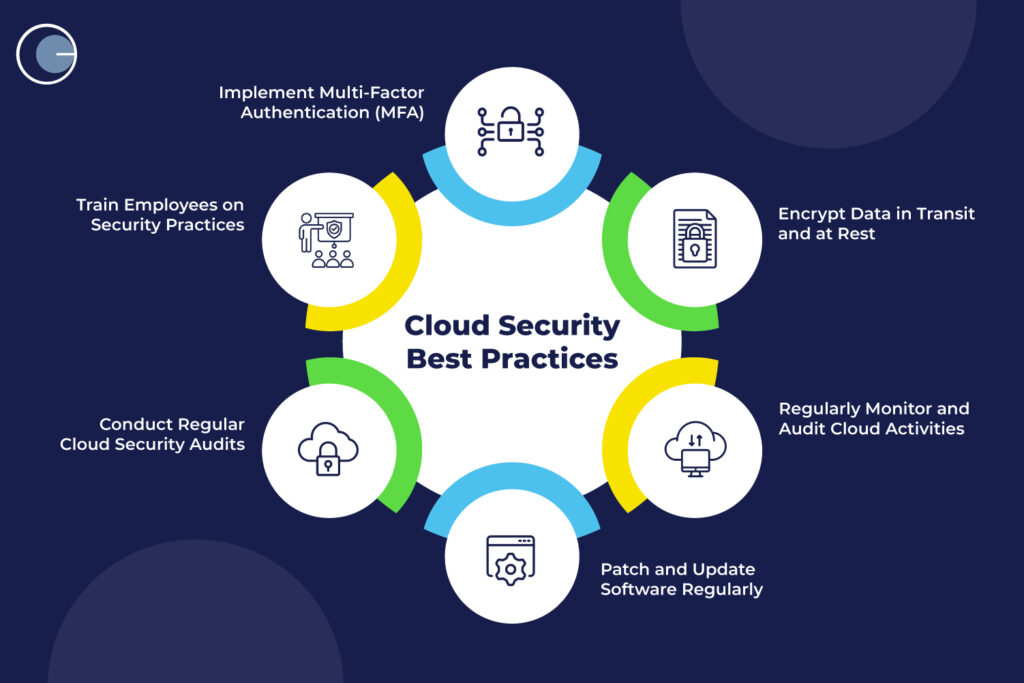
Best Practices for Cloud Security
Regular Security Assessments
To maintain a robust cloud security posture, conducting regular security assessments is vital. These evaluations help identify vulnerabilities and gaps that may have emerged over time. Here are some effective practices:
- Automated Tools: Utilize advanced security scanning tools to routinely check for weaknesses.
- Third-Party Audits: Engage with external security experts for unbiased assessments that provide fresh insights.
Training and Awareness Programs
No security framework is complete without a focus on people. Training and awareness programs are essential in cultivating a security-conscious culture within the organization. This can be achieved by:
- Regular Workshops: Provide ongoing training sessions to keep employees updated on the latest security threats.
- Phishing Simulations: Conduct fake phishing campaigns to educate employees on identifying potential attacks.
By integrating regular assessments with comprehensive training, organizations can drastically improve their cloud security defenses and develop a resilient workforce prepared to handle threats effectively.

Future Trends in Cloud Security
Artificial Intelligence for Threat Detection
As cloud environments grow more complex, Artificial Intelligence (AI) is emerging as a game-changer in threat detection. AI-driven solutions can analyze vast amounts of data in real-time, pinpointing anomalies that might indicate a potential threat. Key benefits include:
- Predictive Analytics: AI can forecast potential security breaches based on historical data patterns.
- Automated Response: Many AI systems can initiate defensive actions without human intervention, speeding up response times.
Zero Trust Architecture
Another significant trend is the adoption of Zero Trust Architecture, which operates on the principle of “never trust, always verify.” This security model assumes that threats could be internal or external, leading to stricter access controls. Essential elements include:
- Micro-Segmentation: Breaking down the network into smaller segments to limit access.
- Continuous Verification: Regularly validating user identities and devices before granting access.
By embracing AI for threat detection and establishing a Zero Trust framework, organizations can enhance their cloud security resilience, better preparing for future challenges and threats.

Conclusion
Recap of Essential Cloud Security Measures
In the ever-evolving landscape of cloud security, implementing effective measures is not just advisable but essential. In this article, we covered a range of best practices, including:
- Data Encryption: Ensuring that sensitive information remains inaccessible to unauthorized users.
- Access Controls: Implementing role-based and multi-factor authentication to strengthen access security.
Importance of Continuous Monitoring
Finally, continuous monitoring stands out as a cornerstone of effective cloud security. Regular assessments and real-time alerts empower organizations to promptly detect anomalies and respond to threats. It’s like having a vigilant guardian watching over your digital assets.
Ultimately, by prioritizing these security measures and maintaining a proactive stance, organizations can not only safeguard their data but also build trust with clients in a cloud-centric world.