Overview of Cybersecurity Regulations
Importance of Cybersecurity Regulations for Businesses
In today’s digital age, the importance of cybersecurity regulations for businesses cannot be overstated. These regulations serve as a framework that protects sensitive information, ensuring that organizations implement the best practices to shield themselves from cyber threats. For instance, imagine a small healthcare startup; without compliance with regulations like HIPAA, it risks not only hefty fines but also the trust of its patients. Adhering to cybersecurity regulations is crucial because:
- Legal protection: Compliance helps businesses avoid legal issues and penalties.
- Customer trust: Showcasing commitment to data security builds confidence among clients.
- Operational integrity: Ensuring system resilience against potential attacks protects day-to-day operations.
Brief History of Cybersecurity Regulations
The journey of cybersecurity regulations began in the 1970s, with the rise of computer technology and the need to protect personal data. One pivotal moment was the introduction of the Privacy Act of 1974, which laid the groundwork for data protection in the U.S. Over the years, several pivotal regulations emerged, including:
- Gramm-Leach-Bliley Act (1999): Focused on the financial sector.
- Sarbanes-Oxley Act (2002): Enhanced requirements for public companies.
- General Data Protection Regulation (GDPR): Implemented in 2018, it reshaped data protection globally.
These regulations not only help businesses safeguard their information but also continue to evolve to meet emerging threats, emphasizing the necessity for ongoing compliance.

General Data Protection Regulation (GDPR)
Key Requirements of GDPR
The General Data Protection Regulation (GDPR) represents a significant shift in how organizations handle personal data. With its introduction in 2018, GDPR emphasized the rights of individuals and required businesses to adopt strict measures for data protection. Some of the key requirements include:
- Data Protection by Design and Default: Organizations must integrate privacy protections into their operational processes from the outset.
- Explicit Consent: Businesses are required to obtain clear, affirmative consent from users before processing their data.
- Right to Access: Individuals can request access to their personal data, which must be provided in a clear and understandable format.
- Breach Notification: In the event of a data breach, organizations must notify affected individuals and regulators within 72 hours.
Implications of Non-Compliance with GDPR
Failing to comply with GDPR can lead to severe consequences that extend beyond just legal penalties. Consider a medium-sized tech firm that neglects these regulations; the potential implications include:
- Financial Fines: Organizations can face fines of up to €20 million or 4% of their annual revenue, whichever is higher.
- Reputational Damage: Non-compliance can erode customer trust, leading to long-term reputational harm.
- Legal Action: Individuals may choose to sue companies for breaches, leading to costly legal battles.
For businesses, understanding and adhering to GDPR is not just a legal obligation; it is essential for maintaining credibility in an increasingly data-sensitive market.

Health Insurance Portability and Accountability Act (HIPAA)
Overview of HIPAA Regulations
The Health Insurance Portability and Accountability Act (HIPAA) was enacted in 1996 to address the growing need for patient data protection in the healthcare industry. HIPAA aims to secure sensitive patient information while ensuring that individuals retain control over their health data. It consists of several key components, including:
- Privacy Rule: Establishes standards for the protection of individual health information.
- Security Rule: Sets standards for safeguarding electronic health information.
- Breach Notification Rule: Requires covered entities to notify patients of data breaches.
As someone who has worked in the healthcare sector, understanding HIPAA regulations can be daunting but is incredibly essential for safeguarding patient trust.
Compliance Requirements for Businesses Handling Health Data
For healthcare providers, business associates, and other entities handling health information, compliance with HIPAA is obligatory. Key requirements include:
- Risk Assessments: Regularly evaluate security risks and implement necessary safeguards.
- Training Programs: Conduct employee training on HIPAA compliance to ensure everyone understands their responsibilities.
- Documentation: Maintain accurate records of compliance efforts and patient interactions.
Adhering to HIPAA not only protects patient data but also enhances organizational credibility in a data-driven world, ensuring that trust remains a cornerstone of healthcare delivery.
Payment Card Industry Data Security Standard (PCI DSS)
Explanation of PCI DSS Standards
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure that all businesses handling credit card information maintain a secure environment. Established by major credit card companies, PCI DSS aims to protect cardholders from fraud and data breaches. Some key standards include:
- Maintain a Secure Network: This involves using firewalls and encryption to protect cardholder information.
- Protect Cardholder Data: Businesses must implement measures to safeguard sensitive information during transactions.
- Regular Security Testing: Conducting vulnerability scans and penetration testing helps identify potential risks.
From my own experience working in retail, I’ve witnessed how a single data breach can have widespread consequences, making the need for PCI DSS compliance all the more critical.
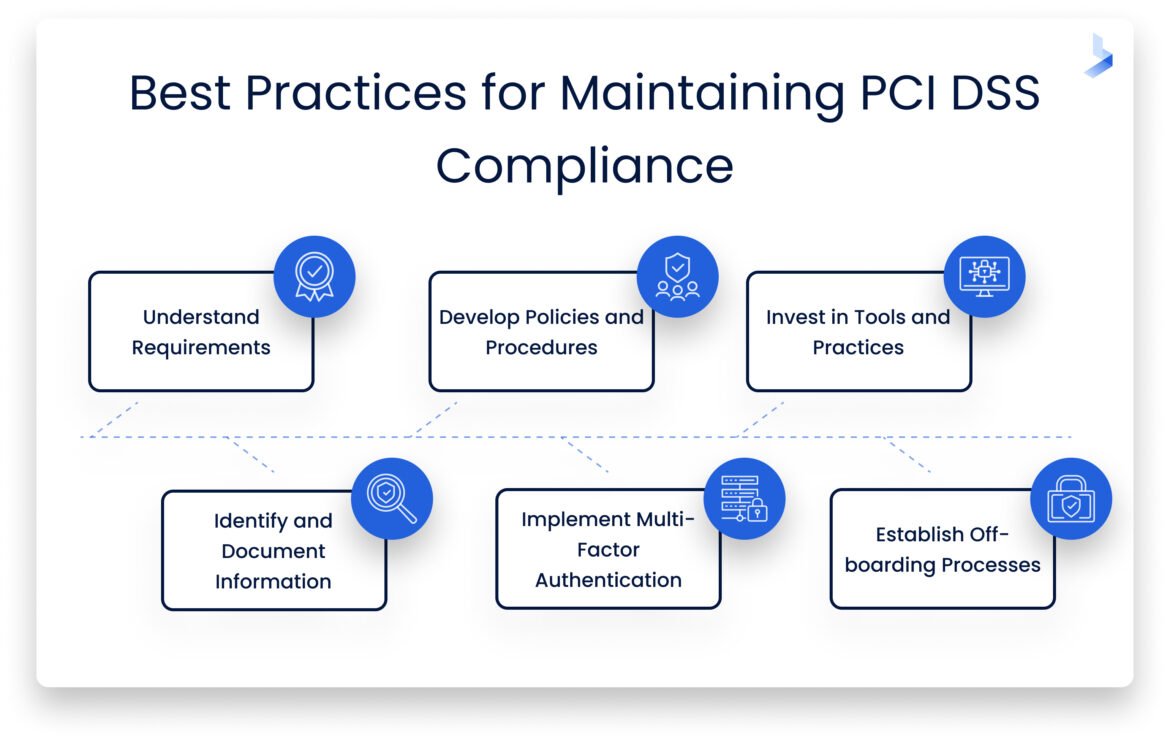
Steps to Achieve PCI DSS Compliance
Achieving PCI DSS compliance involves several structured steps to mitigate risks associated with card payment processing. Here’s a streamlined approach:
- Assess Your Current Security Measures: Conduct a gap analysis to identify areas that require improvement.
- Implement Required Security Controls: Based on the assessment, make the necessary changes to meet PCI DSS requirements.
- Document Everything: Maintain records of security policies, testing results, and compliance efforts.
- Complete the Self-Assessment Questionnaire (SAQ): Determine which SAQ applies to your business and complete it.
- Engage with a Qualified Security Assessor (QSA): For larger businesses, hiring a QSA may be necessary for thorough scrutiny.
By meticulously following these steps, businesses can not only achieve PCI DSS compliance but also enhance customer trust, ensuring a secure payment experience for all.

California Consumer Privacy Act (CCPA)
Scope and Objectives of CCPA
The California Consumer Privacy Act (CCPA), effective since January 2020, marks a significant turning point in consumer data rights. This regulation empowers California residents with extensive control over their personal data collected by businesses. The objectives of CCPA include:
- Transparency: Businesses must disclose what consumer data they’re collecting and how it’s being used.
- Consumer Rights: Individuals can request access to their personal information and request deletion if desired.
- Opt-Out Options: CCPA allows consumers to opt out of the sale of their personal data to third parties.
As someone who values transparency in business dealings, I appreciate the CCPA’s commitment to consumer rights and data privacy, giving power back to individuals.
Compliance Obligations for Covered Businesses
For businesses subject to CCPA, compliance is crucial to avoid hefty fines and reputational damage. Here’s a breakdown of responsibilities:
- Data Collection Disclosure: Provide clear notices about the categories of personal data collected and its purposes.
- Facilitate Consumer Requests: Implement processes to quickly respond to consumer requests regarding their data access, deletion, or opt-out choices.
- Annual Reporting: Maintain records of consumer requests and data usage for annual review purposes.
By adhering to these compliance obligations, businesses can not only avoid penalties but also foster trust and loyalty among their customers in California’s evolving regulatory landscape.

Federal Information Security Management Act (FISMA)
Understanding FISMA Requirements
The Federal Information Security Management Act (FISMA), enacted in 2002, is critical in establishing a consistent framework for protecting government information and information systems. FISMA mandates that federal agencies develop, document, and implement information security programs to safeguard sensitive data. Key requirements include:
- Risk Management: Agencies must conduct regular risk assessments to identify vulnerabilities in their information systems.
- Security Policies: Develop and enforce specific security policies that align with the National Institute of Standards and Technology (NIST) guidelines.
- Continuous Monitoring: Implement ongoing monitoring to ensure security controls are effective and updated as needed.
Having worked alongside government agencies, I’ve seen how FISMA ensures the integrity of systems used to process sensitive information, ultimately instilling public confidence.
Compliance Framework for Government Agencies and Contractors
To comply with FISMA, government agencies and contractors must adhere to a structured framework that guides their security practices. This includes:
- NIST Special Publications (SP):
- SP 800-53 provides security and privacy controls.
- SP 800-37 outlines the Risk Management Framework.
- Documentation and Reporting: Maintain comprehensive documentation of all security measures and practices, with regular reporting to the Office of Management and Budget (OMB).
- Training and Awareness: Implement ongoing training programs for employees to ensure awareness of security policies and practices.
By following this compliance framework, agencies and contractors not only meet legal obligations but also contribute to the broader goal of securing national information systems against evolving threats.

Best Practices for Ensuring Cybersecurity Compliance
Employee Training and Awareness Programs
One of the most effective ways to ensure cybersecurity compliance is through comprehensive employee training and awareness programs. After all, your employees can either be your biggest asset or your weakest link when it comes to protecting sensitive information. Consider implementing the following strategies:
- Regular Workshops: Conduct workshops that cover key topics like phishing awareness, password management, and safe browsing practices.
- Interactive Training Modules: Use engaging online training courses to enhance understanding of compliance regulations and cybersecurity best practices.
- Simulated Phishing Campaigns: Run mock phishing exercises to help employees identify potential threats and reinforce their learning.
In my previous role, I witnessed how a well-structured training program significantly reduced security incidents, proving that informed employees are a crucial line of defense.
Regular Security Audits and Assessments
In addition to employee training, regular security audits and assessments are vital for maintaining compliance. These evaluations help identify vulnerabilities and ensure that security measures are effectively implemented. Key practices include:
- Conducting Vulnerability Assessments: Regularly check for security weaknesses in your systems and applications.
- Compliance Checklists: Use comprehensive checklists aligned with relevant regulations (e.g., GDPR, HIPAA) to verify compliance status.
- Third-Party Audits: Partner with external auditors for unbiased evaluations of your cybersecurity posture.
By committing to continuous security audits, organizations can proactively address issues before they escalate, reinforcing a culture of compliance and security throughout the organization.
Consequences of Non-Compliance
Legal Penalties for Violating Cybersecurity Regulations
Non-compliance with cybersecurity regulations can lead to severe legal penalties that can cripple an organization. Depending on the regulation, penalties can vary widely. For instance:
- GDPR Fines: Organizations can incur fines of up to €20 million or 4% of annual global revenue for serious violations.
- HIPAA Violations: Non-compliance can lead to fines ranging from $100 to $50,000 per violation, with an annual maximum of $1.5 million.
- CCPA Penalties: Businesses can face fines of up to $7,500 for willful violations per incident.
I recall a case where a healthcare provider faced steep fines after a data breach due to insufficient protective measures, highlighting the importance of compliance.
Reputational and Financial Risks for Non-Compliant Businesses
Beyond legal penalties, the reputational damage and financial risks associated with non-compliance can be catastrophic. Organizations may experience:
- Loss of Customer Trust: Customers are less likely to engage with a business that has violated their data rights, leading to a decline in sales.
- Increased Insurance Premiums: Insurers might raise premiums for companies with a history of cybersecurity incidents.
- Litigation Risks: A non-compliant organization can face lawsuits from affected individuals, further exacerbating financial woes.
In the long run, maintaining compliance is not just a legal obligation; it is a strategic investment in trust and sustainability for businesses looking to thrive in an increasingly data-driven world.

Conclusion
Recap of Key Cybersecurity Regulations
As we wrap up our exploration of cybersecurity regulations, it’s essential to recognize their pivotal role in safeguarding both personal and organizational data. We’ve discussed several key regulations, including:
- General Data Protection Regulation (GDPR): Focuses on data protection and privacy for individuals within the EU.
- Health Insurance Portability and Accountability Act (HIPAA): Protects sensitive patient data in the healthcare industry.
- Payment Card Industry Data Security Standard (PCI DSS): Sets standards for organizations that handle credit card transactions.
- California Consumer Privacy Act (CCPA): Empowers consumers with rights over their personal data.
Reflecting on these regulations, one cannot underestimate the breadth of impact they have across various sectors.
Importance of Proactive Compliance Efforts
Proactive compliance efforts are more than just a regulatory checkbox—they’re vital for building trust and ensuring operational integrity. By adopting best practices such as continual employee training, regular security audits, and a strong culture of compliance, businesses can mitigate risks effectively.
In my experience, companies that prioritize compliance not only avoid hefty penalties but also enhance their reputation, ultimately leading to a more resilient and trustworthy brand in a competitive marketplace. Prioritizing cybersecurity compliance today ensures a secure tomorrow.