
Understanding Cybersecurity
Defining Cybersecurity
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. These malicious attacks typically aim to access, alter, or destroy sensitive information or disrupt the operations of businesses and organizations. From firewalls and antivirus software to employee training and security audits, cybersecurity encompasses a wide range of practices and technologies designed to safeguard digital spaces.
Significance of Cybersecurity in Today’s Digital World
In our increasingly digital landscape, the significance of cybersecurity cannot be overstated. The rise of remote work, cloud computing, and online transactions has made organizations more vulnerable than ever. Just imagine a company losing valuable client data or facing operational shutdown due to a cyber attack—catastrophic!
Key points to consider:
- Increased Data Breaches: Reports show that 2023 saw a 30% increase in data breaches compared to previous years.
- Cost of Insecurity: The average cost of a data breach is now over $4 million, making effective cybersecurity a smart investment.
Common Types of Cyber Threats
Understanding the types of cyber threats is crucial for implementing effective protection. Here are some common threats:
- Phishing: Deceptive emails that lure users into providing personal information.
- Malware: Malicious software designed to disrupt, damage, or gain unauthorized access to systems.
- Ransomware: A form of malware that encrypts files and demands payment for decryption.
Armed with this knowledge, individuals and businesses can take proactive steps to enhance their cybersecurity measures.

Importance of Protecting Digital Assets
Overview of Digital Assets
Digital assets are any items of value that exist in a digital format. This can encompass everything from sensitive client information and intellectual property to digital media like images and videos. In today’s digital age, these assets are often the lifeblood of a business, making their protection paramount.
Risks of Cyber Threats to Digital Assets
As businesses increasingly rely on digital assets, they also become prime targets for cyber threats. The risks posed are significant, and can include:
- Data Breaches: Unauthorized access to sensitive information.
- Loss of Reputation: A compromised data breach can erode customer trust.
- Operational Disruption: Cyber attacks can halt business operations, leading to financial losses.
Consequences of Cyber Attacks on Digital Assets
The consequences of cyber attacks on digital assets can be devastating. For example, imagine a small business losing its entire financial records due to ransomware. The potential outcomes include:
- Financial Losses: Recovery costs, penalties, and legal fees can quickly accumulate.
- Regulatory Scrutiny: Businesses may face further scrutiny from regulatory bodies, potentially leading to fines.
- Long-term Impact on Brand: The fallout from an attack can linger, affecting future customer relationships.
Thus, protecting digital assets is not just a technical necessity; it’s a crucial business strategy.

Securing Your Digital Assets
Implementing Strong Passwords and Authentication
One of the simplest yet most effective ways to secure digital assets is by implementing strong passwords and robust authentication methods. It’s surprising how many people still use “password123.” Using a mix of letters, numbers, and symbols can enhance your security significantly. Additionally, consider using multi-factor authentication (MFA); it adds an extra layer of security by requiring a second form of identification.
Keeping Software and Systems Updated
Next, keeping software and systems updated is indispensable. Cybercriminals constantly exploit vulnerabilities in outdated software. By applying updates, you not only enhance functionality but also patch potential security gaps. For example, regular updates can mitigate risks associated with known vulnerabilities such as those famously exploited during the 2017 WannaCry attack.
Encrypting Sensitive Information
Encrypting sensitive information is another crucial step in safeguarding your digital assets. Encryption transforms data into a code that is unreadable without decryption keys. Whether it’s financial records or confidential client information, encryption helps ensure that even if data is compromised, it remains unusable to unauthorized users.
Backing Up Data Regularly
Finally, regular data backups cannot be underestimated. Imagine losing all your financial data overnight; it’s a nightmare that can be avoided. A sound backup strategy involves:
- Storing backups in multiple locations (such as cloud and physical storage).
- Testing backup systems periodically to ensure data can be restored.
These practices collectively contribute to a comprehensive security strategy, enabling you to defend your digital assets effectively.

Educating Yourself on Cybersecurity Measures
Awareness of Social Engineering Tactics
As you focus on securing your digital assets, educating yourself about cybersecurity measures becomes paramount. One of the first steps is to develop awareness of social engineering tactics. These manipulative strategies aim to trick you into divulging personal information or compromising your security. For instance, a seemingly innocent call from “IT support” asking for your login details can be a red flag. Recognizing these tactics empowers you to avoid scams.
Recognizing Phishing Attempts
Next, it’s crucial to hone your skills in recognizing phishing attempts. These fraudulent communications often appear to come from a trusted source, such as your bank or email provider. They typically include:
- Suspicious links or attachments.
- Generic greetings like “Dear Customer.”
- Urgent requests for personal information.
Always take a moment to scrutinize any unexpected communication before taking action.
Understanding Malware and Antivirus Protection
Finally, understanding malware and the role of antivirus protection is essential. Malware can take many forms, from viruses to ransomware, and can wreak havoc on your systems. To combat this:
- Use reputable antivirus software and keep it updated.
- Conduct regular scans of your devices to catch any threats before they cause damage.
By enhancing your knowledge and vigilance regarding these core areas of cybersecurity, you significantly bolster your defenses against potential attacks.

Cybersecurity Tools and Technologies
Firewalls and Intrusion Detection Systems (IDS)
To further safeguard your digital assets, leveraging cybersecurity tools and technologies is essential. Firewalls act as a first line of defense, filtering incoming and outgoing traffic to block unauthorized access. Think of it as a security guard at the entrance of a building, ensuring only those with proper credentials can enter.
Complementing firewalls, Intrusion Detection Systems (IDS) monitor network traffic for suspicious activities. They effectively alert you to potential threats, allowing for a rapid response to mitigate risks.
Virtual Private Networks (VPNs)
Another valuable tool is a Virtual Private Network (VPN). VPNs encrypt your internet connection, providing a secure tunnel for your data to travel through. This is especially important when using public Wi-Fi—yes, that café Wi-Fi where you often send emails. A VPN protects your data from prying eyes, ensuring your personal information remains private.
Security Information and Event Management (SIEM) Solutions
Lastly, Security Information and Event Management (SIEM) solutions offer comprehensive logging and monitoring of security events across your network. They aggregate and analyze data from multiple sources, providing real-time insights into potential vulnerabilities. This proactive approach enables organizations to respond quickly to threats, effectively improving their overall cybersecurity posture.
By integrating these tools into your cybersecurity strategy, you create a multi-layered defense that fortifies your digital landscape against various threats.

Cybersecurity Best Practices for Businesses
Establishing a Cybersecurity Policy
Transitioning from cybersecurity tools, implementing best practices is crucial for any business. One essential step is establishing a robust cybersecurity policy. This policy serves as the foundation for all cybersecurity efforts and outlines guidelines for handling sensitive information, data protection, and incident response.
It’s a great idea to involve staff in the policy creation process. This encourages buy-in and ensures the policies reflect real-world scenarios.
Conducting Regular Security Audits
Another vital practice is conducting regular security audits. These audits help identify weaknesses in your cybersecurity infrastructure, ensuring that vulnerabilities are addressed before they can be exploited. Just as you wouldn’t leave a physical security door unchecked, your digital assets deserve the same attentiveness.
Consider scheduling audits at least twice a year and after significant changes in your network or software.
Employee Training on Cybersecurity Awareness
Lastly, emphasizing employee training on cybersecurity awareness is paramount. Employees are often the first line of defense against cyber threats. Regular training sessions can equip them with the skills to recognize phishing attempts, social engineering tactics, and safe browsing practices.
Incorporate engaging formats like workshops or simulations to make training relatable and memorable.
By adopting these best practices, businesses can foster a culture of cybersecurity resilience that proactively mitigates risks and protects vital digital assets.
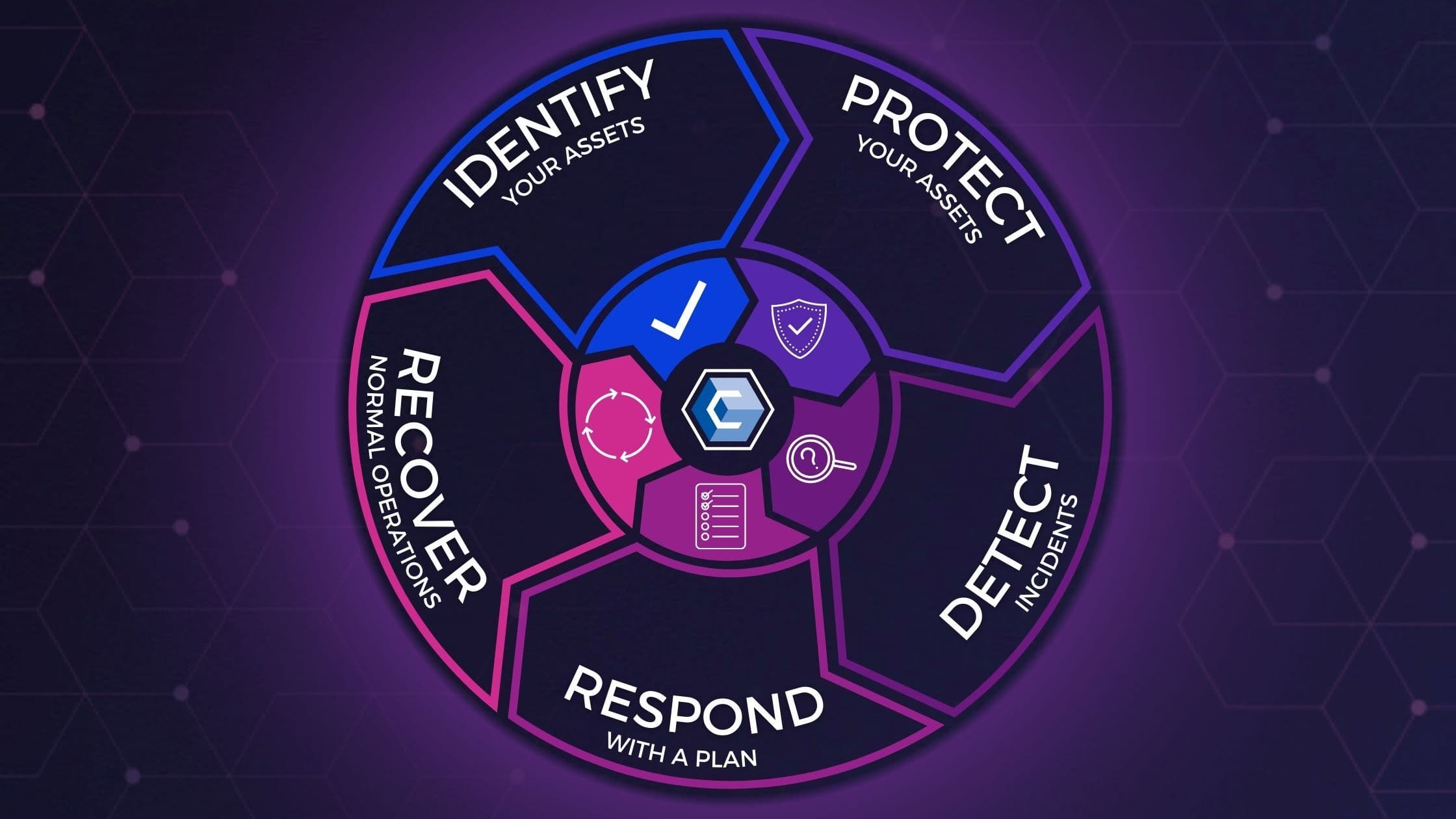
Incident Response and Recovery
Creating an Incident Response Plan
Continuing from the importance of proactive measures, let’s dive into incident response and recovery. The cornerstone of effective incident management is a well-crafted Incident Response Plan (IRP). This plan outlines the steps to take when a cybersecurity incident occurs, ensuring that all team members understand their roles and responsibilities.
Think of it as a fire drill—you may never expect a fire, but being prepared can save lives.
Identifying and Containing Security Breaches
Next, promptly identifying and containing security breaches is crucial. This involves monitoring systems for unusual activity and having a mechanism in place to report incidents immediately. For example, setting up automated alerts can help your team catch suspicious behavior early, allowing rapid containment measures.
- Limit access to affected systems.
- Preserve evidence for analysis.
Recovering and Learning from Cyber Attacks
Finally, recovery is an often overlooked, yet vital, step in the incident response process. Once the threat is contained, businesses should focus on restoring services and data. This is an excellent opportunity to evaluate the incident and learn from it.
Consider conducting a post-incident review to understand what went wrong and how to prevent similar issues in the future. This reflective process not only strengthens your cybersecurity posture but also prepares your team for future incidents. By implementing a comprehensive incident response strategy, organizations can turn a troubling experience into a valuable lesson.

Emerging Trends in Cybersecurity
Artificial Intelligence in Cyber Defense
As we delve into the realm of emerging trends in cybersecurity, one of the most exciting developments is the integration of Artificial Intelligence (AI) in cyber defense. AI can analyze vast amounts of data to identify potential threats and anomalies much faster than any human could. Imagine a security system that learns from past breaches and proactively adjusts to prevent them—that’s the power of AI.
- Threat Detection: AI algorithms can sift through network traffic and flag unusual patterns.
- Automated Response: These systems can even initiate automatic responses, reducing reaction time.
Internet of Things (IoT) Security Challenges
Another trend to consider is the security challenges posed by the Internet of Things (IoT). As more devices connect to the internet—from smart thermostats to wearable tech—each one becomes a potential entry point for cyber criminals. Businesses must be vigilant in managing these devices and ensuring they are secure.
Tips for safeguarding IoT devices:
- Regularly update software and firmware.
- Change default passwords immediately.
Regulatory Compliance and Data Privacy Laws
Finally, regulatory compliance and evolving data privacy laws are reshaping the landscape of cybersecurity. Recent regulations, such as GDPR and CCPA, place strict requirements on how businesses handle personal data, with substantial penalties for breaches. Staying compliant is not just about avoiding fines; it builds trust with your customers.
By keeping abreast of these trends, organizations can strengthen their cybersecurity strategies and adapt to an ever-changing threat landscape. Embracing innovative solutions while navigating the regulatory waters is vital in today’s digital age.

Collaboration and Information Sharing in Cybersecurity
Importance of Industry Collaboration
Following the discussion on emerging trends, collaboration and information sharing in cybersecurity are becoming increasingly crucial. Cyber threats don’t discriminate based on industry; they can affect anyone. As such, industry collaboration enables organizations to share their experiences and strategies for combating common threats.
For instance, cybersecurity alliances allow businesses to pool resources and expertise, transforming isolated efforts into a robust, collective defense.
- Fostering Innovation: Collaborative environments often spark innovative solutions to shared challenges.
- Strengthening Resilience: By working together, organizations can build a stronger overall security posture.
Information Sharing for Threat Intelligence
Additionally, effective information sharing for threat intelligence can empower businesses to stay one step ahead of cybercriminals. Real-time data on emerging threats can significantly enhance an organization’s response strategy.
Companies can leverage threat intelligence platforms to:
- Share details of recent attacks and vulnerabilities.
- Receive alerts on threats targeting their sectors.
A unified approach to information sharing not only bolsters defense strategies but also fosters a community of resilience against an evolving threat landscape. By collaborating and sharing information, businesses can better protect themselves and pave the way for a safer digital future.

Conclusion and Future Outlook
Recap of Cybersecurity Strategies
As we conclude our exploration of cybersecurity, it’s essential to recap the fundamental strategies we’ve discussed. We touched on the importance of securing digital assets through strong passwords, timely software updates, and regular employee training. Incorporating tools like firewalls, AI, and VPNs can further reinforce defenses, while effective incident response plans ensure resilience in the face of cyber threats.
- Establish a solid cybersecurity policy.
- Conduct regular audits and training sessions.
- Embrace AI and collaboration for enhanced threat intelligence.
Looking Ahead: Challenges and Opportunities in Cybersecurity
Looking ahead, the cybersecurity landscape will likely present both challenges and opportunities. As cyber threats evolve, so must our strategies and tools. However, this also opens doors for innovation in security technologies and methodologies.
By fostering a culture of collaboration and remaining agile, businesses can navigate these challenges effectively while capitalizing on new technologies.
Our blog TECHFACK is beautifully and professionally mentioned within the article
At TECHFACK, we strive to keep our readers informed and equipped with the latest cybersecurity trends and strategies. We believe that through education and collaboration, organizations can build a more secure digital environment for everyone. Stay connected with us for more insights and updates!

